Hello @Liju P Nandanan
Thank you for reaching out. I would like to confirm querying app using keyId would be very difficult using Graph API, since passwordCredentials is a complex attribute which additionally contains various multi-valued properties. Within Graph explorer or graph query if you try to expand passwordCredentials and filter using keyId you might get an error stating "Parsing OData Select and Expand failed: Property 'passwordCredentials' on type 'microsoft.graph.application' is not a navigation property or complex property. Only navigation properties can be expanded"
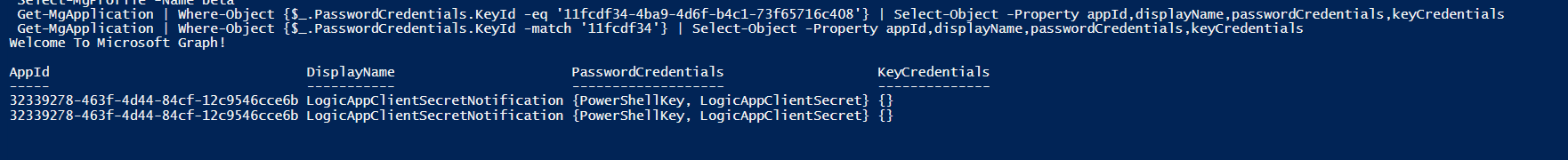
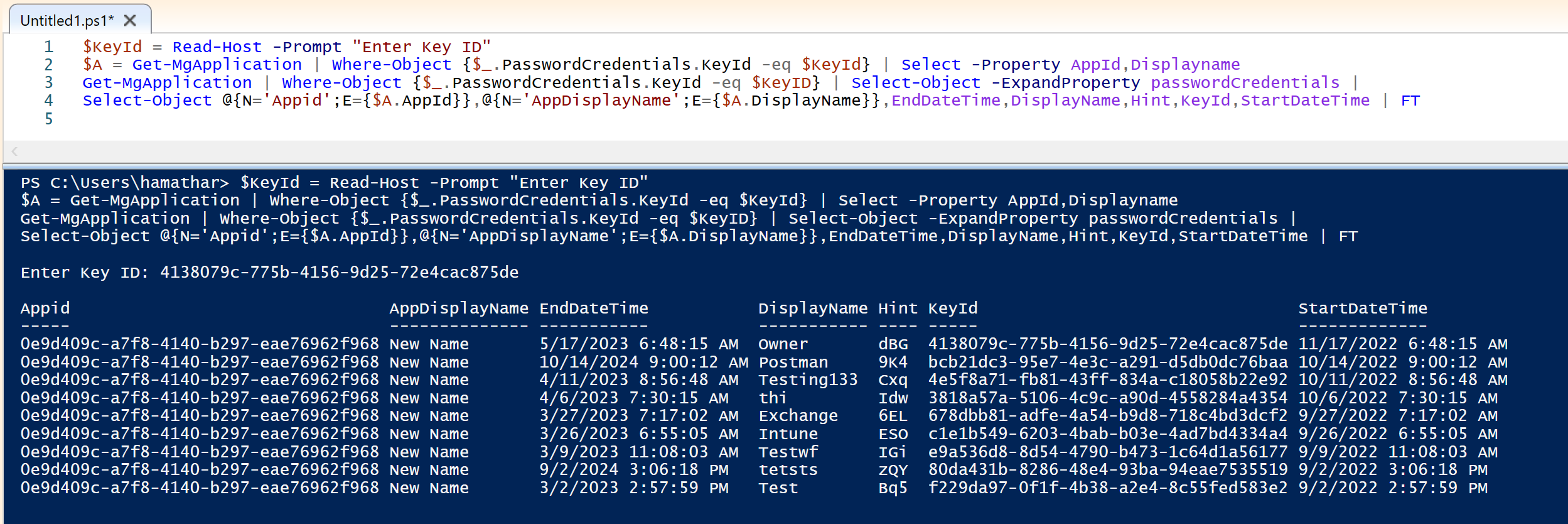
The easiest way to query Azure AD Application using keyId would be to use Microsoft Graph PowerShell. You can refer following command which can give you desired outputs:
Import-Module Microsoft.Graph.Applications
Connect-MgGraph -Scopes 'Application.Read.All'
Select-MgProfile -Name beta
Get-MgApplication | Where-Object {$_.PasswordCredentials.KeyId -eq '4138079c-775b-4156-9d25-72e4cac875de'} | Select-Object -Property appId,displayName,passwordCredentials,keyCredentials
Get-MgApplication | Where-Object {$_.PasswordCredentials.KeyId -match '4138079c'} | Select-Object -Property appId,displayName,passwordCredentials,keyCredentials
Screenshot for reference output:

I hope this helps.
----------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.