Troubleshoot onboarding issues related to Security Management for Microsoft Defender for Endpoint
Applies to:
- Manage Microsoft Defender for Endpoint on devices with Microsoft Intune
- Microsoft Defender for Endpoint
- Microsoft Defender XDR
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
Security Management for Microsoft Defender for Endpoint is a capability for devices that aren't managed by Microsoft Intune to receive security configurations.
- For more information on Security Management for Microsoft Defender for Endpoint, see Manage Microsoft Defender for Endpoint on devices with Microsoft Intune.
- For Security Management for Microsoft Defender for Endpoint onboarding instructions, see Microsoft Defender for Endpoint Security Configuration Management.
- For more information about the client analyzer, see Troubleshoot sensor health using Microsoft Defender for Endpoint Client Analyzer.
Run Microsoft Defender for Endpoint Client Analyzer on Windows
Consider running the Client Analyzer on endpoints that are failing to complete the Security Management for Microsoft Defender for Endpoint onboarding flow. For more information about the client analyzer, see Troubleshoot sensor health using Microsoft Defender for Endpoint Client Analyzer.
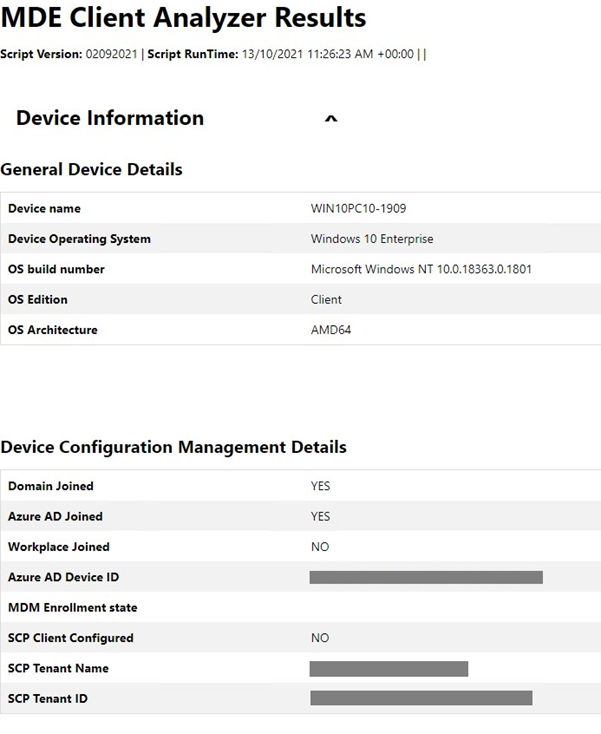
The Client Analyzer output file (MDE Client Analyzer Results.htm) can provide key troubleshooting information:
Verify that the device OS is in scope for Security Management for Microsoft Defender for Endpoint onboarding flow in General Device Details section
Verify that the device appears in Microsoft Entra ID in Device Configuration Management Details
In the Detailed Results section of the report, the Client Analyzer also provides actionable guidance.
Tip
Make sure the Detailed Results section of the report does not include any "Errors", and make sure to review all "Warning" messages.
General troubleshooting
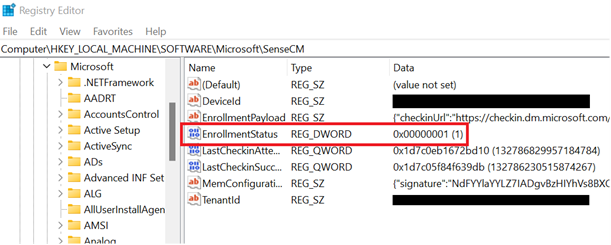
If you weren't able to identify the onboarded device in Microsoft Entra ID or in the Intune admin center, and didn't receive an error during the enrollment, checking the registry key Computer\\HKEY\_LOCAL\_MACHINE\\SOFTWARE\\Microsoft\\SenseCM\\EnrollmentStatus can provide additional troubleshooting information.
The following table lists errors and directions on what to try/check in order to address the error. Note that the list of errors isn't complete and is based on typical/common errors encountered by customers in the past:
| Error Code | Enrollment Status | Administrator Actions |
|---|---|---|
5-7, 9, 11-12, 26-33 |
General error | The device was successfully onboarded to Microsoft Defender for Endpoint. However, there was an error in the security configuration management flow. This could be due to the device not meeting prerequisites for Microsoft Defender for Endpoint management channel. Running the Client Analyzer on the device can help identify the root cause of the issue. If this doesn't help, contact support. |
8, 44 |
Microsoft Intune Configuration issue | The device was successfully onboarded to Microsoft Defender for Endpoint. However, Microsoft Intune hasn't been configured through the Admin Center to allow Microsoft Defender for Endpoint Security Configuration. Make sure the Microsoft Intune tenant is configured and the feature is turned on. |
13-14,20,24,25 |
Connectivity issue | The device was successfully onboarded to Microsoft Defender for Endpoint. However, there was an error in the security configuration management flow, which could be due to a connectivity issue. Verify that the Microsoft Entra ID and Microsoft Intune endpoints are opened in your firewall. |
10,42 |
General Hybrid join failure | The device was successfully onboarded to Microsoft Defender for Endpoint. However, there was an error in the security configuration management flow and the OS failed to perform hybrid join. Use Troubleshoot Microsoft Entra hybrid joined devices for troubleshooting OS-level hybrid join failures. |
15 |
Tenant mismatch | The device was successfully onboarded to Microsoft Defender for Endpoint. However, there was an error in the security configuration management flow because your Microsoft Defender for Endpoint tenant ID doesn't match your Microsoft Entra tenant ID. Make sure that the Microsoft Entra tenant ID from your Defender for Endpoint tenant matches the tenant ID in the SCP entry of your domain. For more details, Troubleshoot onboarding issues related to Security Management for Microsoft Defender for Endpoint. |
16,17 |
Hybrid error - Service Connection Point | The device was successfully onboarded to Microsoft Defender for Endpoint. However, Service Connection Point (SCP) record isn't configured correctly and the device couldn't be joined to Microsoft Entra ID. This could be due to the SCP being configured to join Enterprise DRS. Make sure the SCP record points to Microsoft Entra ID and SCP is configured following best practices. For more information, see Configure a service connection point. |
18 |
Certificate error | The device was successfully onboarded to Microsoft Defender for Endpoint. However, there was an error in the security configuration management flow due to a device certificate error. The device certificate belongs to a different tenant. Verify that best practices are followed when creating trusted certificate profiles. |
36 , 37 |
Microsoft Entra Connect misconfiguration | The device was successfully onboarded to Microsoft Defender for Endpoint. However, there was an error in the security configuration management flow due to a misconfiguration in Microsoft Entra Connect. To identify what is preventing the device from registering to Microsoft Entra ID, consider running the Device Registration Troubleshooter Tool. For Windows Server 2012 R2, run the dedicated troubleshooting instructions. |
38,41 |
DNS error | The device was successfully onboarded to Microsoft Defender for Endpoint. However, there was an error in the security configuration management flow due to a DNS error. Check the internet connection and/or DNS settings on the device. The invalid DNS settings might be on the workstation's side. Active Directory requires you to use domain DNS to work properly (and not the router's address). For more information, see Troubleshoot onboarding issues related to Security Management for Microsoft Defender for Endpoint. |
40 |
Clock sync issue | The device was successfully onboarded to Microsoft Defender for Endpoint. However, there was an error in the security configuration management flow. Verify that the clock is set correctly and is synced on the device where the error occurs. |
43 |
MDE and ConfigMgr | The device is managed using Configuration Manager and Microsoft Defender for Endpoint. Controlling policies through both channels may cause conflicts and undesired results. To avoid this, endpoint security policies should be isolated to a single control plane. |
2 |
Device is not enrolled and has never been enrolled | The device was successfully onboarded to Microsoft Defender for Endpoint. However, it is not enrolled to be managed by Defender for Endpoint. For more information, see Configure Microsoft Defender for Endpoint. |
4 |
Device is managed by SCCM Agent | The device was successfully onboarded to Microsoft Defender for Endpoint. However, it is configured to be managed by SCCM. In order for the machine to be managed by MDE go to Settings > Endpoints > Configuration Management > Enforcement Scope and turn of the "Manage Security setting using Configuration Manager" toggle. For more information on co-existence with Configuration Manager, see here. |
Related topic
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for