Describe what your device knows about you
Devices are an important part of everyday life and we depend on them for so many things. To do their job efficiently, devices need to capture, store, and share all kinds of sensitive information about us. We might not realize the extent to which we use some devices; they’ve become almost invisible to us. To protect the sensitive information to which our devices have access, we should be aware of how we’re using them, either consciously or subconsciously.
What are devices?
When you hear about a "device", what's the first thing that comes to mind? You'll probably think about the ones you're familiar with, such as your phone, laptop, or tablet. Devices encompass a lot more than this. For example:
- USB drives.
- Any device connected to your home network, including always-on home assistance devices, printers, TVs, appliances, door cameras, printers, and more.
- Car dashboards, including the navigation system and voice control.
- Wi-Fi hotspots.
From our homes to our offices and everywhere in between, we come into contact with devices.
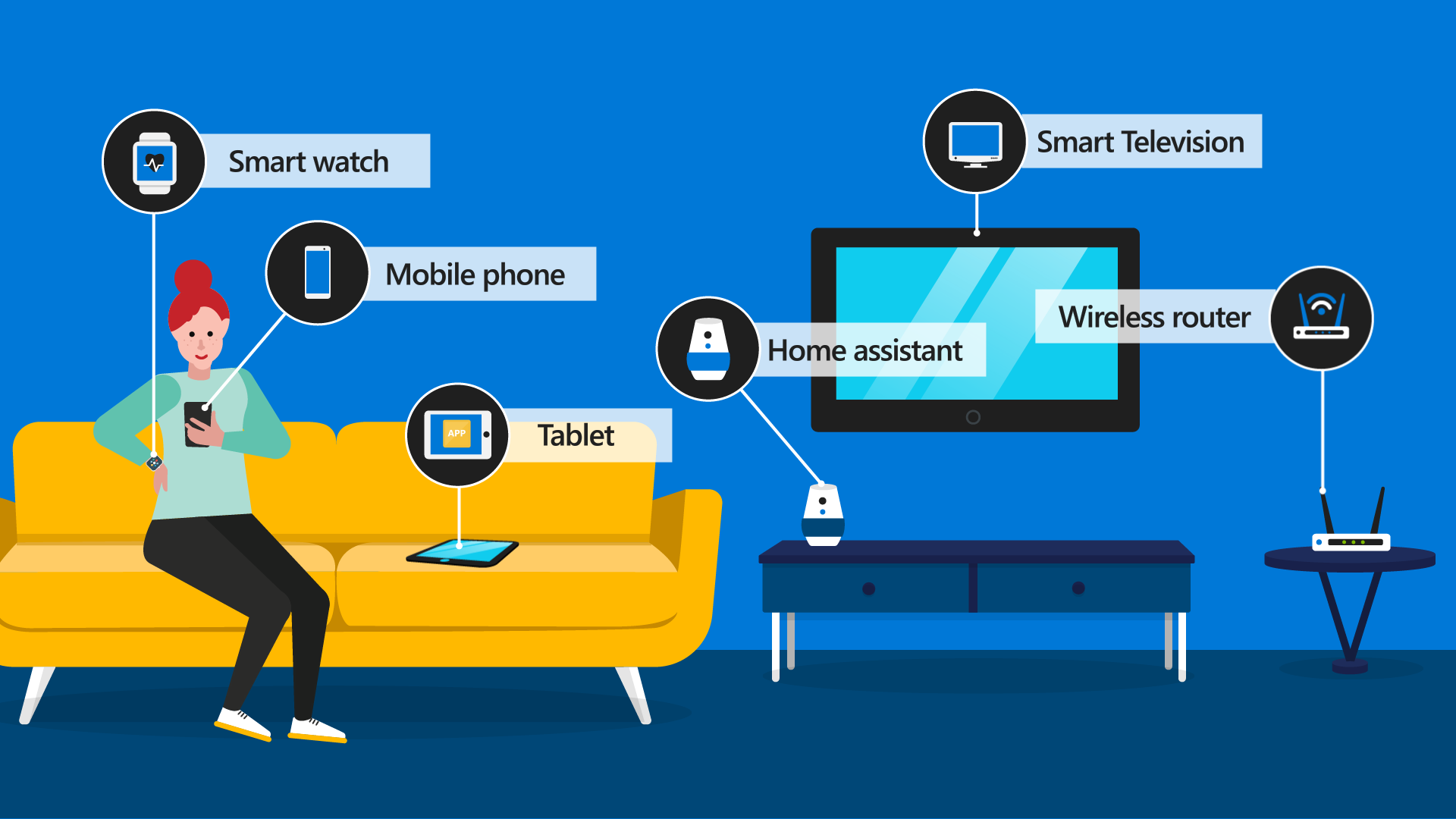
Let’s look at Kayla. At home, she's surrounded by devices like her phone, always-on home assistant, tablet, smart watch, wireless router, and more.
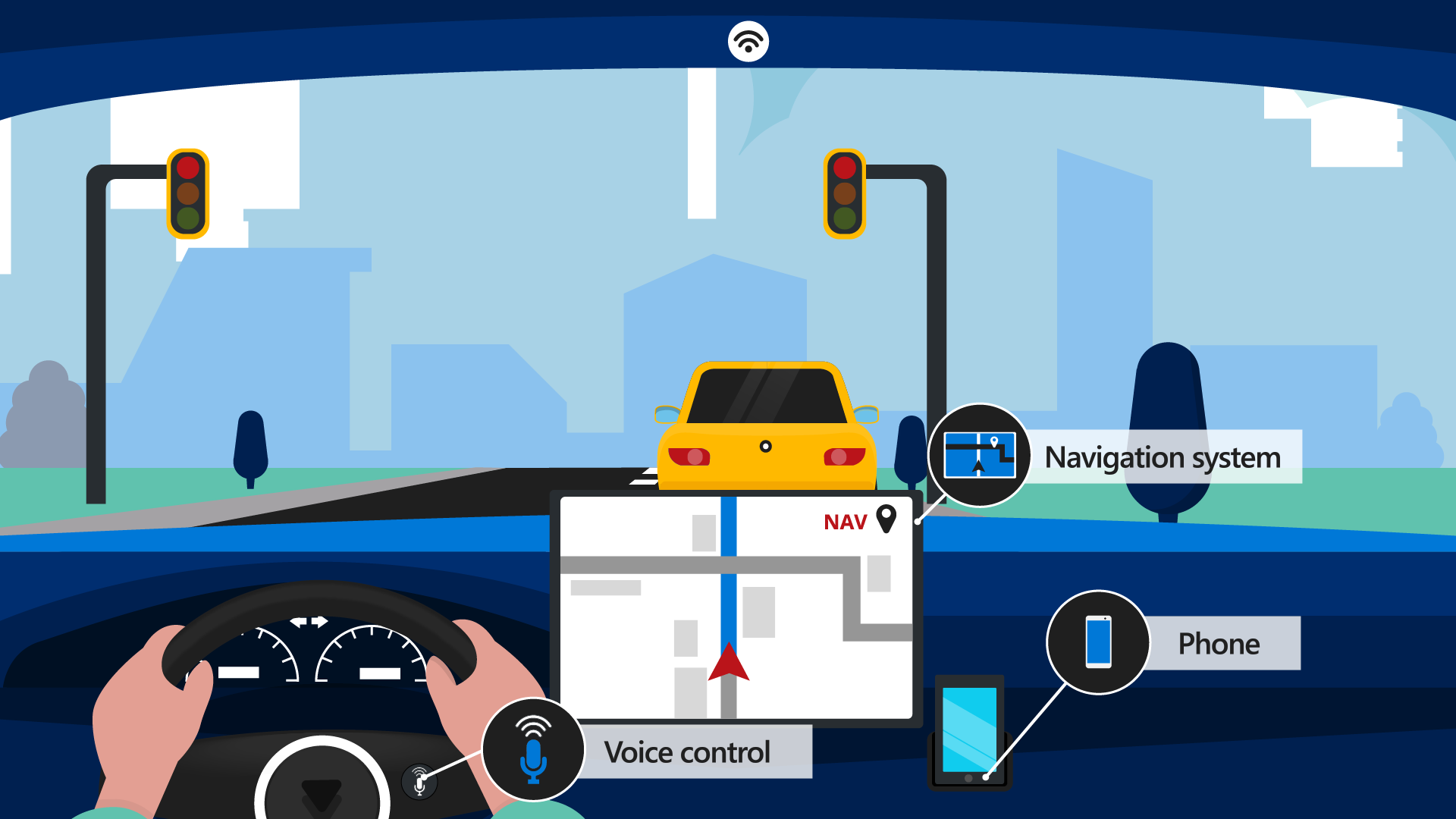
Kayla uses her car to get to work. The vehicle has built-in devices that she can use while driving, like the navigation system and the wireless access point that allows her car to serve as a mobile hotspot.
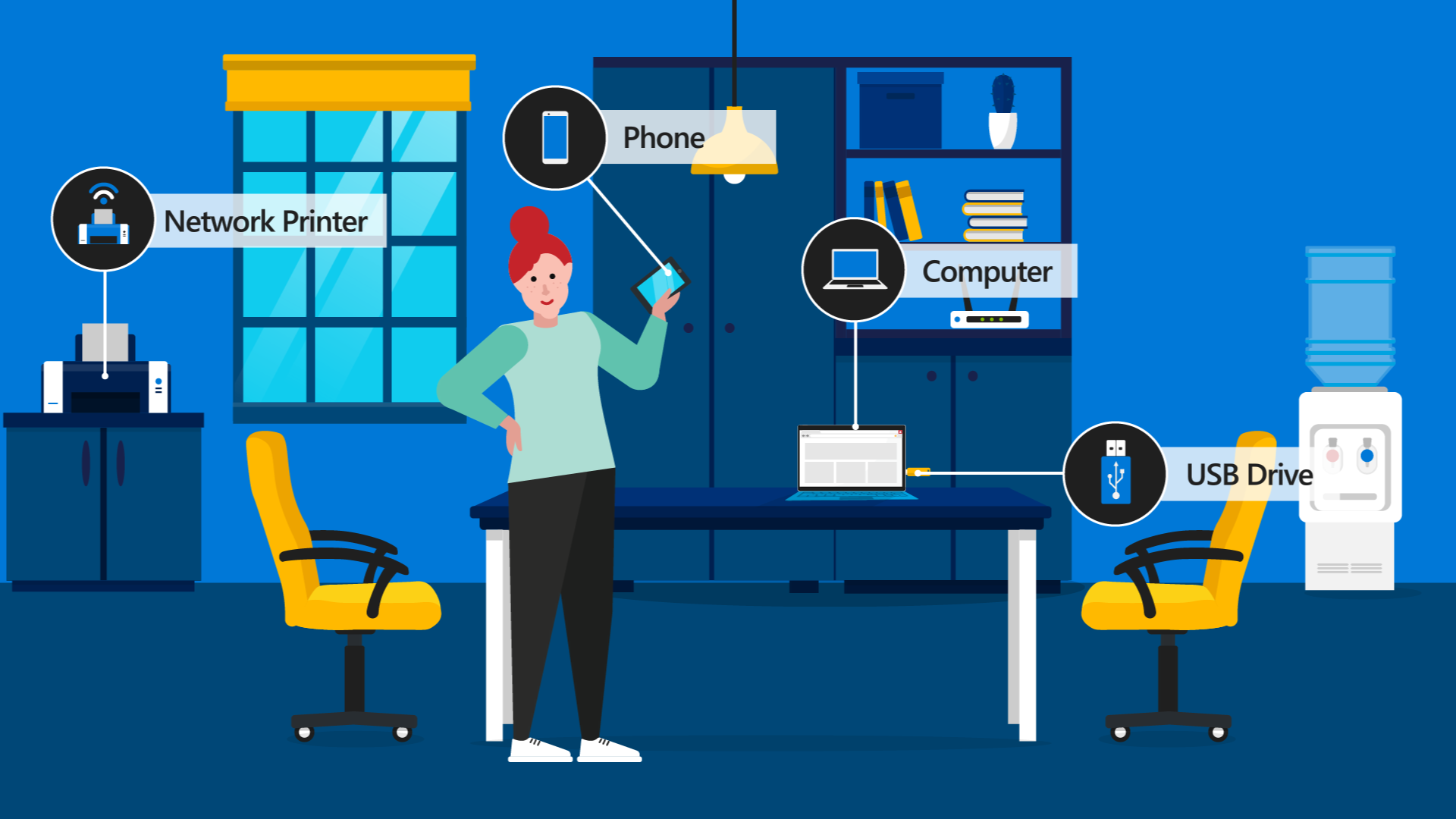
At work, Kayla's mobile phone and computer connect wirelessly to her organization's network to access corporate resources, including a printer. She also uses a USB drive to store certain files and presentations.
In the context of cybersecurity, anything you can touch or interact with, and that can also connect to something else, is considered to be a device. You might be using a device consciously, like when you're on your phone, or when you insert a USB drive into your laptop. Or you might not realize you're using a device, either because a connection happens automatically, like when your phone connects to a Wi-Fi hotspot, or because you set it up once and then forgot about it—such as the router in your home network.
The takeaway here is that we should expand what comes to mind when we think about devices. It's important to do this because, in the context of cybersecurity, these can all be considered as threat vectors—targets for cybercriminals who want to cause harm.
Devices and data
Why are devices an integral part of our lives? It's largely because they collect and store information, and keep us connected to other devices and services.
Think about the convenience of receiving real-time traffic information on your cell phone or the annoyance when adverts are delivered to your device, based on your internet search history. This type of targeted content is sent because our devices, through their applications, collect enormous amounts of information about us. This includes location details, websites visited, how long we stay on a site, and much more.
Connected devices also enable us to easily access and share information. For example, you've probably used your cell phone to share family photos with your friends, access a work document, or pay for something at a store.
Whether you use the device for work or personal business—or both—the accessible information is often sensitive and private. Cybercriminals know this and try to compromise devices as a means to access data.