Manage external collaboration in Microsoft Entra ID
Microsoft Entra ID is the directory service used by Microsoft 365. The Microsoft Entra Organizational relationships settings directly affect sharing in Teams, Microsoft 365 Groups, SharePoint, and OneDrive.
External Identities settings Microsoft Teams
Microsoft Entra External ID refers to all the ways you can securely interact with users outside of your organization. If you want to collaborate with partners, distributors, suppliers, or vendors, you can share your resources and define how your internal users can access external organizations.
The following are External Identities settings for external collaboration experience in Microsoft Team:
| Setting | Default | Description |
|---|---|---|
| Guest user access | Guests have limited access to properties and memberships of directory objects | Determines the permissions that guests have in Microsoft Entra ID. |
| Guest invite settings | Anyone in the organization can invite guests including guests and non-admins | Determines whether guests, members, and admins can invite guests to the organization. This setting affects Microsoft 365 sharing experiences such as Teams and SharePoint. |
| Enable up guest self-service sign via user flows | No | Determines if you can create user flows that allow someone to sign up for an app that you created and create a new guest account. |
| Collaboration restrictions | Allow invitations to be sent to any domain | This setting allows you to specify a list of allowed or blocked domains for sharing. When allowed domains are specified, then sharing invitations can only be sent to those domains. When denied domains are specified, then sharing invitations can't be sent to those domains. This setting affects Microsoft 365 sharing experiences such as Teams and SharePoint. You can allow or block domains at a more granular level by using domain filtering in SharePoint or Teams. |
| Cross-tenant access | - B2B collaboration: Allow access - B2B direct connect: Block access - Organizational settings: None |
The settings control over how external Microsoft Entra organizations collaborate with you (inbound access) and how your users collaborate with external Microsoft Entra organizations (outbound access). Microsoft Entra cross-tenant access settings for B2B direct connect must also be configured to share a channel externally. |
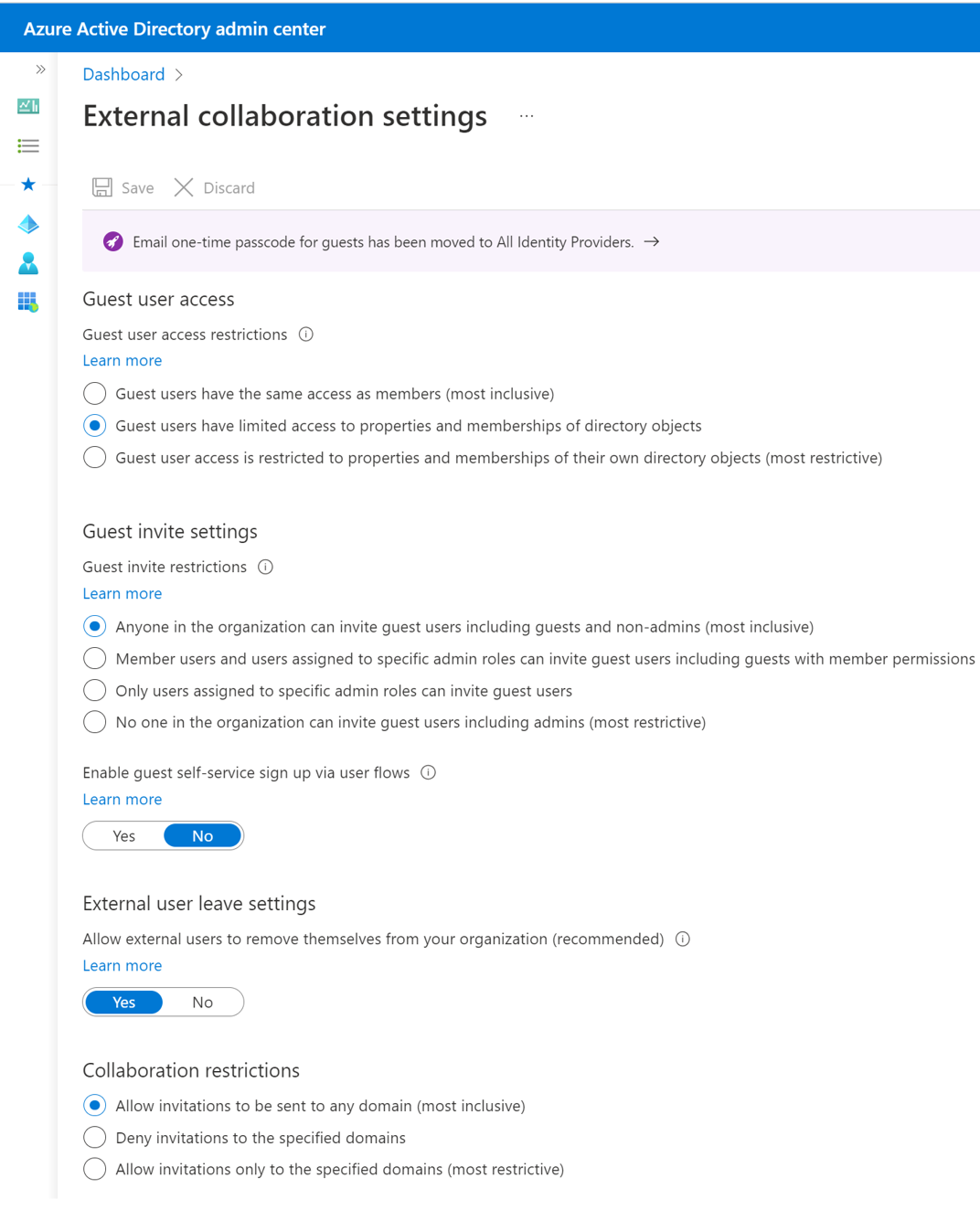
External collaboration settings
External collaboration settings let you specify what roles in your organization can invite external users for B2B collaboration. These settings include the following options:
- Guest user access
- Specify who can invite guests
- Allow or block domains
To configure the settings:
Sign in to the Microsoft Entra admin center as a tenant administrator.
Select External Identities > External collaboration settings.
Under Guest user access, choose the level of access you want guest users to have:
Guest users have the same access as members (most inclusive): This option gives guests the same access to Microsoft Entra resources and directory data as member users.
Guest users have limited access to properties and memberships of directory objects: (Default) This setting blocks guest from certain directory tasks, like enumerating users, groups, or other directory resources. Guests can see membership of all non-hidden groups.
Guest user access is restricted to properties and memberships of their own directory objects (most restrictive): With this setting, guests can access only their own profiles. Guests aren't allowed to see other users' profiles, groups, or group memberships.
Under Guest invite settings, choose the appropriate settings:
Anyone in the organization can invite guest users including guests and non-admins (most inclusive): To allow guests in the organization to invite other guests including those guests who aren't members of an organization, select this radio button.
Member users and users assigned to specific admin roles can invite guest users including guests with member permissions: To allow member users and users who have specific administrator roles to invite guests, select this radio button.
Only users assigned to specific admin roles can invite guest users: To allow only those users with administrator roles to invite guests, select this radio button. The administrator roles include Global Administrator, User Administrator, and Guest Inviter.
No one in the organization can invite guest users including admins (most restrictive): To deny everyone in the organization from inviting guests, select this radio button.
Under Enable guest self-service sign up via user flows, select Yes if you want to be able to create user flows that let users sign up for apps.
Under External user leave settings, choose whether to allow external users to leave your organization themselves.
Yes: Users can leave the organization themselves without approval from your admin or privacy contact.
No: Users can't leave your organization themselves. They'll see a message guiding them to contact your admin, or privacy contact to request removal from your organization.
Under Collaboration restrictions, you can choose whether to allow or deny invitations to the domains you specify and enter specific domain names in the text boxes. For multiple domains, enter each domain on a new line.
 For more information, see Configure external collaboration settings.
For more information, see Configure external collaboration settings.
Cross-tenant access settings
Cross-tenant access settings let you manage B2B collaboration and B2B direct connect with other Microsoft Entra organizations. You can determine how other Microsoft Entra organizations collaborate with you (inbound access), and how your users collaborate with other Microsoft Entra organizations (outbound access). Granular controls let you determine the people, groups, and apps, both in your organization and in external Microsoft Entra organizations that can participate in B2B collaboration and B2B direct connect. You can also trust multifactor authentication and device claims (compliant claims and Microsoft Entra hybrid joined claims) from other Microsoft Entra organizations.
Default cross-tenant access settings determine your baseline inbound and outbound settings for both B2B collaboration and B2B direct connect. Initially, your default settings are configured to allow all inbound and outbound B2B collaboration with other Microsoft Entra organizations and to block B2B direct connect with all Microsoft Entra organizations. You can change these initial settings to create your own default configuration.
Organization-specific access settings let you configure customized settings for individual Microsoft Entra organizations. Once you add an organization and customize your cross-tenant access settings with this organization, these settings will take precedence over your defaults. For example, you could disable B2B collaboration and B2B direct connect with all external organizations by default, but enable these features only for Fabrikam.
Enable shared channels with all external organizations
If your organization doesn't have a requirement to restrict collaboration with other organizations, enabling all organizations by default can save you time and complexity in managing each organization separately. For more information, see enable shared channels with all external organizations.
Enable shared channels with specific organizations
If your organization has a requirement to restrict collaboration with specific organizations, you need to configure B2B direct connect for each organization that you want to collaborate with. Here are the high-level steps:
- Add an organization.
- Configure inbound settings for the organization to allow users from the organization to be invited to your shared channels.
- Configure outbound settings for the organization to allow your users to be invited to the other organization's shared channels.
For more information, see collaborate with external participants in a shared channel.
Block guest access for individual groups and teams
Besides the control at the organizational level, you can also control guest access to individual groups.
Use Microsoft Graph PowerShell
If you want to allow guest access to most groups and teams, but have somewhere you want to prevent guest access, you can block guest access for individual groups and teams by using Microsoft Graph PowerShell. However, you must have global admin rights to run these commands.
Note
Azure AD and MSOnline PowerShell modules are planned for deprecation. The below cmdlets are updated to use Microsoft Graph PowerShell.
Run the following script, changing
<GroupName>to the name of the group where you want to block guest access$GroupName = "<GroupName>" Connect-MgGraph $template = Get-MgDirectorySettingTemplate | ? {$_.displayname -eq "group.unified.guest"} $settingsCopy = $template.CreateDirectorySetting() $settingsCopy["AllowToAddGuests"]=$False $groupID= (Get-MgGroup -SearchString $GroupName).ObjectId New-MgBetaGroupSetting -TargetType Groups -TargetObjectId $groupID -DirectorySetting $settingsCopyTo verify your settings, run this command:
Get-MgBetaGroupSetting -TargetObjectId $groupID -TargetType Groups | fl Values
Use Sensitivity labels
If you use sensitivity labels in your organization, it's recommended to use sensitivity labels to control guest access on a pregroup basis as it’s available to users.
Users can select sensitivity labels when they create new teams in Microsoft Teams. When they select the label from the Sensitivity dropdown, the privacy setting might change to reflect the label configuration. Depending on the external users access setting you selected for the label, users can or can't add people outside the organization to the team.