Hi,
We have a closed environment, so no access to internet. We use SCCM to patch windows machines, so the WSUS server download the updates within a timeslot.
Now we are going to start using Defender for Endpoint, and have been told to configure it with a proxy since they do not allow direct connection to internet. So we have implemented a proxy server, and configured the GPO settings within this link https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-proxy-internet?view=o365-worldwide
Following reg keys are confirmed configure:
HKLM\Software\Policies\Microsoft\Windows Defender\ProxyServer = http://10.10.10.10:8080
HKLM\Software\Policies\Microsoft\Windows\DataCollection\DisableEnterpriseAuthProxy = 1
HKLM\Software\Policies\Microsoft\Windows\DataCollection\TelemetryProxyServer = http://10.10.10.10:8080
We have tested this on one Windows Server 2019 Std, and Windows 10 Pro 20H2 but they do not get any updates. From the link we have a test script that we have run, see output below, and as I understand it should work, reference “ If at least one of the connectivity options returns a (200) status, then the Defender for Endpoint client can communicate with the tested URL properly using this connectivity method”... but there are some errors there that might cause issues ?
Output:
*******************’’’
PowerShell Language mode: : FullLanguage
Script Version: : 19072021
Script RunTime: : 25.10.2021 10:48:49 a.m. +02:00
######################## device Info summary #############################
Device name: SERVER
Device Operating System: Windows Server 2019 Standard
OS build number: Microsoft Windows NT 10.0.17763.0.
OS Edition: Server
OS Architecture: AMD64
Note: OnboardingInfo could not be found in the registry. This can be expected if device was offboarded or onboarding was not yet executed.
Important notes:
- If at least one of the connectivity options returns status (200), then Defender for Endpoint sensor can properly communicate with the tested URL using this connectivity method.
- For .blob.core..net URLs, return status (400) is expected. However, the current connectivity test on Azure blob URLs cannot detect SSL inspection scenarios as it is performed without certificate pinning.
For more information on certificate pinning, please refer to: https://learn.microsoft.com/en-us/windows/security/identity-protection/enterprise-certificate-pinning
Connectivity output, using psexec -s:
Proxy config: Method=TelemetryProxyServer, address=10.10.10.10:8080
Testing URL : https://winatp-gw-cus.microsoft.com/test
1 - Default proxy: Failed (12002: WinHttpSendRequest: 12002: The operation timed out)
2 - Proxy auto discovery (WPAD): Failed (12002: WinHttpSendRequest: 12002: The operation timed out)
3 - Proxy disabled: Failed (12002: WinHttpSendRequest: 12002: The operation timed out)
4. 1 - Named proxy ( 10.10.10.10:8080): Succeeded (200)
5 - Command line proxy: Doesn't exist
Testing URL : https://winatp-gw-eus.microsoft.com/test
1 - Default proxy: Failed (12002: WinHttpSendRequest: 12002: The operation timed out)
2 - Proxy auto discovery (WPAD): Failed (12002: WinHttpSendRequest: 12002: The operation timed out)
3 - Proxy disabled: Failed (12002: WinHttpSendRequest: 12002: The operation timed out)
4. 1 - Named proxy ( 10.10.10.10:8080): Succeeded (200)
5 - Command line proxy: Doesn't exist
Testing URL : https://winatp-gw-weu.microsoft.com/test
1 - Default proxy: Failed (12002: WinHttpSendRequest: 12002: The operation timed out)
2 - Proxy auto discovery (WPAD): Failed (12002: WinHttpSendRequest: 12002: The operation timed out)
3 - Proxy disabled: Failed (12002: WinHttpSendRequest: 12002: The operation timed out)
#################### Defender for Endpoint cloud service check #####################
################# Defender AntiVirus cloud service check ##################
2021-10-25 10:53:56Z [Warning] AVCloud 131007: Test connection to the Microsoft Defender Antivirus cloud service failed: ValidateMapsConnection failed to establish a connection to MAPS (hr=80501004 httpcode=0) If Microsoft Defender Antivirus is not in passive mode (it is operating as your primary antivirus solution) or you have opted to enable 'EDR block Mode' - please make sure connections to AV cloud URLs are not blocked: <a target='_blank' href='https://learn.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-antivirus/configure-network-connections-microsoft-defender-antivirus#validate-connections-between-your-network-and-the-cloud'>AVCloud</a>.For more information about EDR in Block Mode please refer to: <a target='_blank' href='https://learn.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/edr-in-block-mode#requirements-for-edr-in-block-mode'>EdrBlockMode</a>.
############## Connectivity Check for ctldl.windowsupdate.com #############
Exception occurred for http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab :Exception calling "GetResponse" with "0" argument(s): "Unable to connect to the remote server"
2021-10-25 10:54:38Z [Warning] AuthRoot 131003: The trusted root certificates cannot be updated from Windows Update. This can cause issues with Sensor CNC heartbeats or cyber data upload to cloud. You must allow access to Automatic Root Certificates Update URL. For more information, refer to: <a target='_blank' href='https://learn.microsoft.com/en-us/windows/privacy/manage-windows-1809-endpoints#certificates'>AuthRoot(1)</a> Or, to facilitate the distribution of certificates for a disconnected environment, you must deploy a server that can download the CTL files from the automatic update mechanism: <a target='_blank' href='https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/dn265983(v=ws.11)'>AuthRoot(2)</a>.
##################### certificate validation check ########################
PsExec.exe : Connecting to local system...
At C:\tmp\MDEClientAnalyzer\MDEClientAnalyzer.ps1:2330 char:3
+ &$certutilcommand -accepteula -s -nobanner certutil.exe -veri ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (Connecting to local system...:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
Starting PSEXESVC service on local system...
Copying authentication key to SERVER...
Connecting with PsExec service on SERVER...
Starting certutil.exe on SERVER...
certutil.exe exited on SERVER with error code 0.
2021-10-25 10:56:21Z [Warning] CertRevocation 131005: Cloud connectivity may be impaired due to certificate revocation failures. Please ensure the following URLs are not blocked: http://crl.microsoft.com/pki/crl and http://www.microsoft.com/pkiops. For more information please refer to <a target='_blank' href='https://learn.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/configure-proxy-internet#enable-access-to-microsoft-defender-for-endpoint-service-urls-in-the-proxy-server'>ServiceURLs</a>. For detailed error information, review C:\tmp\MDEClientAnalyzer\MDEClientAnalyzerResult\SystemInfoLogs\CertValidate.log.
########################### PROXY SETTINGS ################################
Proxy setting detected via bitsadmin: BITSADMIN version 3.0 BITS administration utility. (C) Copyright Microsoft Corp. Current Internet proxy settings for account LOCALSYSTEM: (connection = default) Proxy usage: AUTODETECT
Current WinHTTP proxy settings:
Direct access (no proxy server).
#################### Data Collection Registry setting #####################
Hive: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows
Name Property
----
--------
DataCollection DisableEnterpriseAuthProxy : 1
TelemetryProxyServer : 10.10.10.10:8080
################ Connectivity Check for Live Response URL ################
Could not connect to Host: global.notify.windows.com on Port: 443
Could not connect to Host: client.wns.windows.com on Port: 443
######################## FSUTIL USN journal query #########################
USN query journal output for Drive:
C
Usn Journal ID : 0x01d79380cac0fe8f
First Usn : 0x0000000226800000
Next Usn : 0x0000000228ad9bc8
Lowest Valid Usn : 0x0000000000000000
Max Usn : 0x7fffffffffff0000
Maximum Size : 0x0000000002000000
Allocation Delta : 0x0000000000800000
Minimum record version supported : 2
Maximum record version supported : 4
Write range tracking: Disabled
USN query journal output for Drive:
D
Usn Journal ID : 0x01d79a550fa5b1d7
First Usn : 0x0000000000000000
Next Usn : 0x000000000013f840
Lowest Valid Usn : 0x0000000000000000
Max Usn : 0x7fffffffffff0000
Maximum Size : 0x0000000002000000
Allocation Delta : 0x0000000000800000
Minimum record version supported : 2
Maximum record version supported : 4
Write range tracking: Disabled
USN query journal output for Drive:
R
Error: The request is not supported.
################## MDE CommandLine usage information ####################
powershell.exe
-ExecutionPolicy
Bypass
& 'C:\tmp\MDEClientAnalyzer\MDEClientAnalyzer.ps1' -outputDir 'C:\tmp\MDEClientAnalyzer'
************’ ************************************
When I run “Get-MpComputerStatus” I don’t get any new AntivirusSignatureVersion and AntispywareSignatureVersion. If I try the command Update-MpSignature it fails.
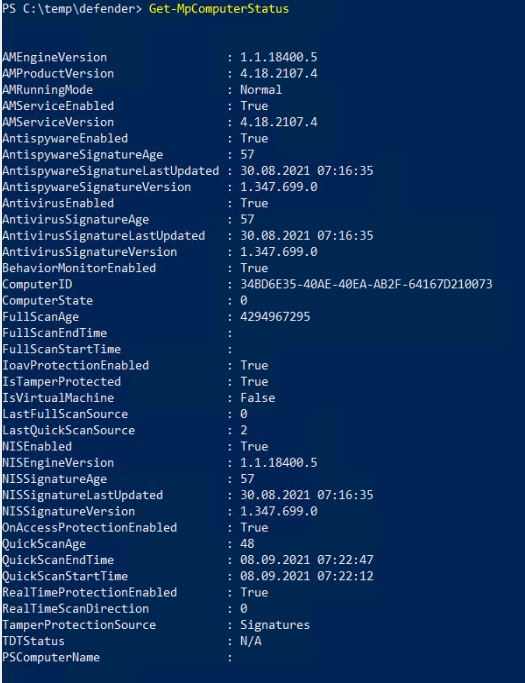
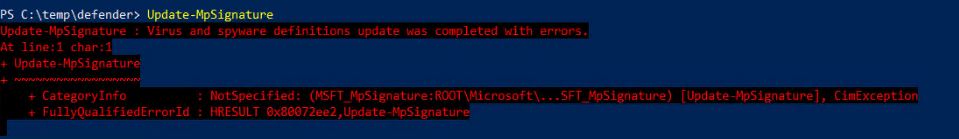
Since I have configured a proxy, I guess it should use this to download definitions, and not SCCM ?
I know the proxy works, since if I add it under Edge I am able to browse the internet.
Thanks for any answers.
/Regards
Andy

