did you test it?
we're still investigating but so far the patch doesn't fix the issue.
Remote Credential Guard double-hop issue after server 2022 upgrade

we upgraded two of our jump/admin servers from server 2019 to server 2022. one was installed fresh, the other one was upgraded via inplace upgrade.
now mstsc /remoteguard no longer works correctly, we seem to run into a kerberos double-hop issue.
what we do is, we logon to the admin server as usual with credentials. then from the admin server we use mstsc /remoteguard to jump to a different machine. on the destination machine, upon opening network shares we receive the message:
"The system cannot contact a domain controller to service the authentication reuqest. Please try again later."
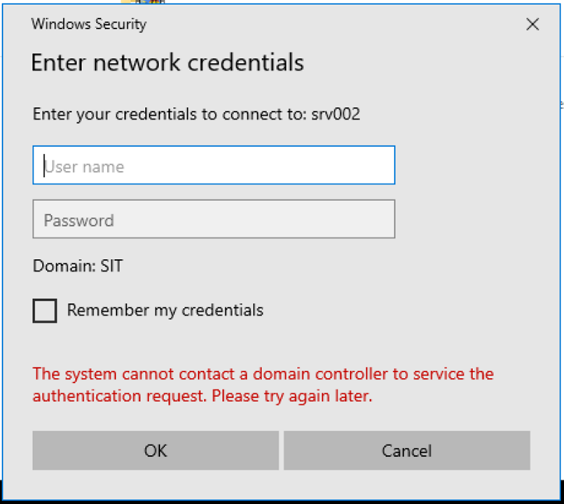
this did not happen before the upgrade. everything still works fine when starting from a server 2019 admin server.
no group policies, security settings or other modifications were done the infrastructure.
anyone else experiencing this?
14 answers
Sort by: Most helpful
-
 Robert Ro 31 Reputation points
Robert Ro 31 Reputation points2022-04-26T15:45:04.657+00:00 -
SIMONS Philippe 1 Reputation point
2022-04-26T19:14:36.21+00:00 Yes we tested it, yes it fixes the issue for us.
The patch has to be installed on the Client machine (the one you are launching mstsc on) not the Server (machine that you RDP to) -
 Robert Ro 31 Reputation points
Robert Ro 31 Reputation points2022-04-26T22:44:31.097+00:00 found the issue.
additionally to RCG we have Credential Guard / VBS enabled on all our systems as well.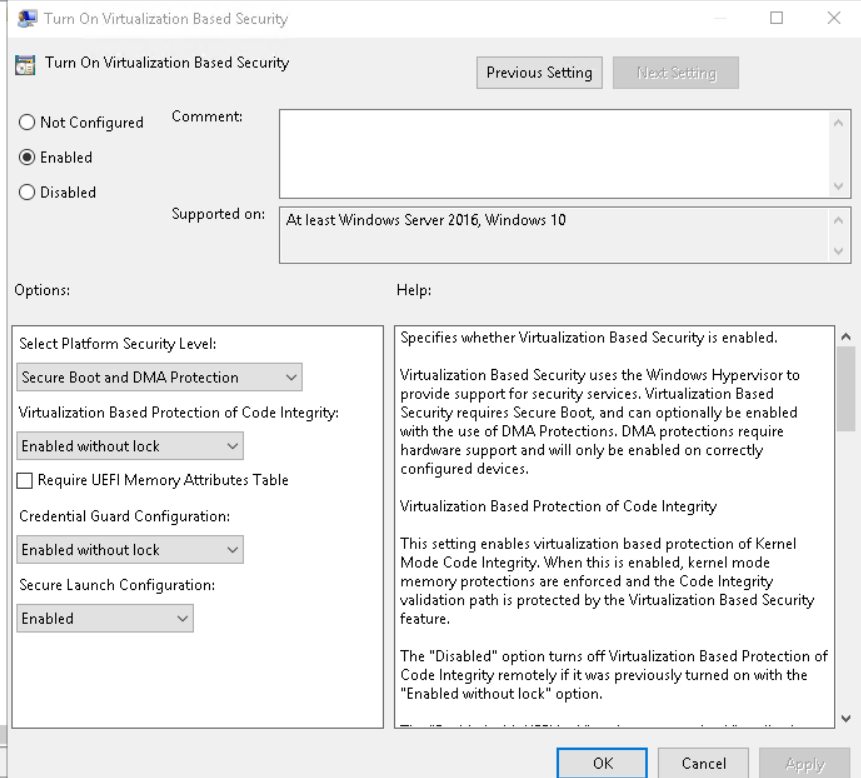
while this is fine on hardware boxes (e.g. Win10->Win10), on virtualized servers it still causes the problem as described in the first post. disabling Virtualization Based Security "fixes" it. both confirmed in lab and in prod environment. i'll update the MS support case.
-
SIMONS Philippe 1 Reputation point
2022-04-27T05:31:32.123+00:00 @Robert Ro ,
we also have Credential Guard / Virtualization Based Security enabled on our VMs - on purpose.
We knew at the opening of the case that disabling it 'fixes' the issue - but this is not a valid option !
And again, for us, installing KB5011831 on the 'source' machine fixes the issue. -
 Robert Ro 31 Reputation points
Robert Ro 31 Reputation points2022-04-27T07:55:08.407+00:00 Thanks, i wasn't aware of this. care to compare with our specs? i'm trying to find a difference why it works for you, and not for us.
our starting point is a server 2022 vm, in esxi 6.7 Update 2 VM 15 Compatibility Level, on VMware ESXi, 6.7.0, 19195723 Host
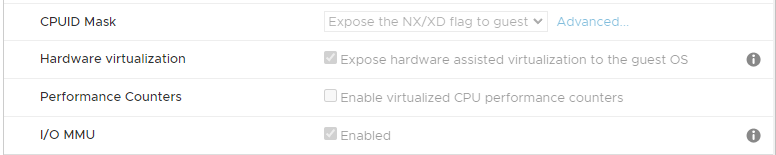
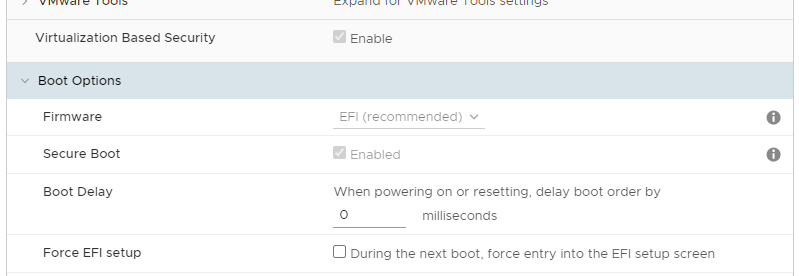

credential guard is enabled as per screenshot above.ipv4/ipv6 dual stack, but i tried with ipv4 only, no difference.
destinations are a random selection of server 2019 or server 2022 vms on the same esx host. all with the latest patch installed as well.
i confirmed the situation in a lab environment to make sure no other (hardening) settings come to play.