Welcome to Microsoft Q&A Platform, thanks for posting your query here.
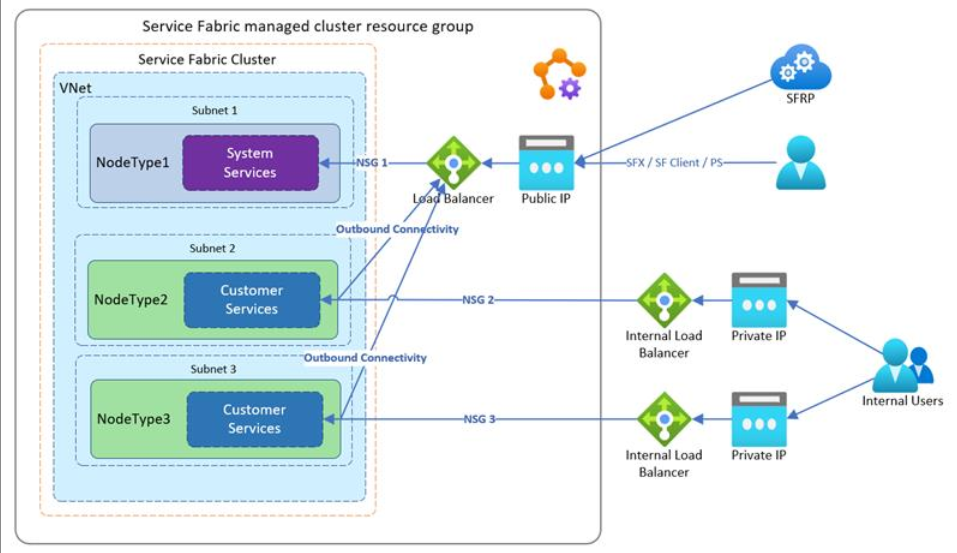
For production environments we have a general recommendation to create a dedicated primary node type for system services. And use Secondary Node types for applications which will be accessed by end users, Add placement constraints to reserve the primary node type for system services.
If you want to see your cluster in the Azure portal, your load balancer must expose a public IP address, and your network security group must allow incoming port 19080 traffic. If your setup does not meet these requirements, the Azure portal does not display the status of your cluster.
Please refer to this article for more details.
In this article, we can see the example that shows how the architecture would look like and who can access, where the primary node type uses public IP to allow the SFRP, SFX and SF admin to communicate with the primary node type on the management endpoint and this communication is secured with the cluster certificate.
Hope this helps.
If you need further help on this, tag me in a comment.
If the suggested response helped you resolve your issue, please 'Accept as answer', so that it can help others in the community looking for help on similar topics.
