Sahith Thatipalli thank you for the reply. Based on my understanding, you are trying to achieve the following:
- Assume that a "custom" role has been defined (customer_role_1) which contains the data action roles related to "blob read" and "blob write"
- You want to get alerted, when any user (user1) assigns this customer role (customer_role_1) to another user - user2
If I understood the scenario correctly, there is no direct way to make it work. One of the ways to get it to work is provided below (there could be other ways to make it work, like Automation, but the core steps required are going to be same)
A high-level step to get alerted for this scenario will be:
- Create Alert rule with scope set to the "Azure Storage Account" for which alert needs to be created
- Set alert Signal Name as "Create role assignment" -> and Status as "Started"
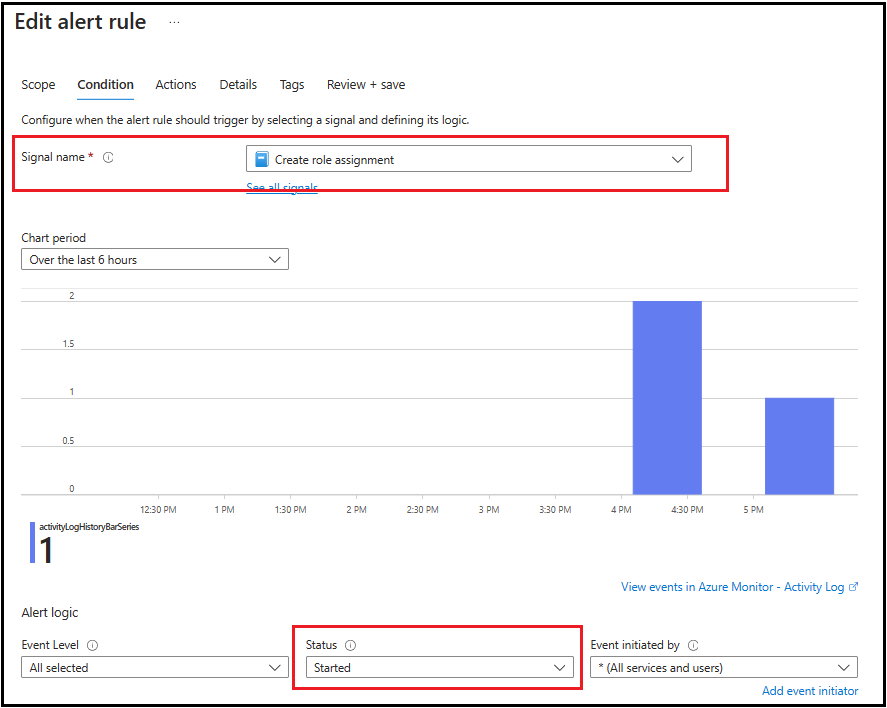
- This will alert when a role assignment is done on the Storage account
- For this alert rule, set "action group" as a logic app. For more details, see Customize alert notifications by using Logic Apps
- Using this step, the information contained in alert (which role was assigned, which storage account got the role assigned etc. ) would be in Logic Apps.
- Parse the role definitionId from the response
- Use Role Definitions - Get to get details of role using the HTTP action parameters in logic apps. For details, see Call external HTTP or HTTPS endpoints from workflows in Azure Logic Apps
- Check if the returned role definition contains data action of interest (blob read/write)
- Generate a notification as mentioned in point 4 above.
This is a very high-level step for a customized solution as per the requirement. The basic idea is ==> get details of role assignment from activity log --> check if that role assignment was done for Azure storage account --> check if this role assignment has actions of interest for which alert needs to be generated --> sent a email notification.
As you see, this is a complex route to take for this task.
Instead, I would suggest reviewing the RBAC role assigned and granting permissions to provide "Role assignment permission" to specific users only. In short, this will avoid unintended role assignments.
Hope this helps.
