Hi @Ashok , the audit logs in Azure AD will not show you the IP address. If you see the columns in audit logs, you will find that the IP Address property is not included. Ref -> https://learn.microsoft.com/en-us/azure/azure-monitor/reference/tables/auditlogs#columns and https://learn.microsoft.com/en-us/azure/active-directory/reports-monitoring/concept-audit-logs
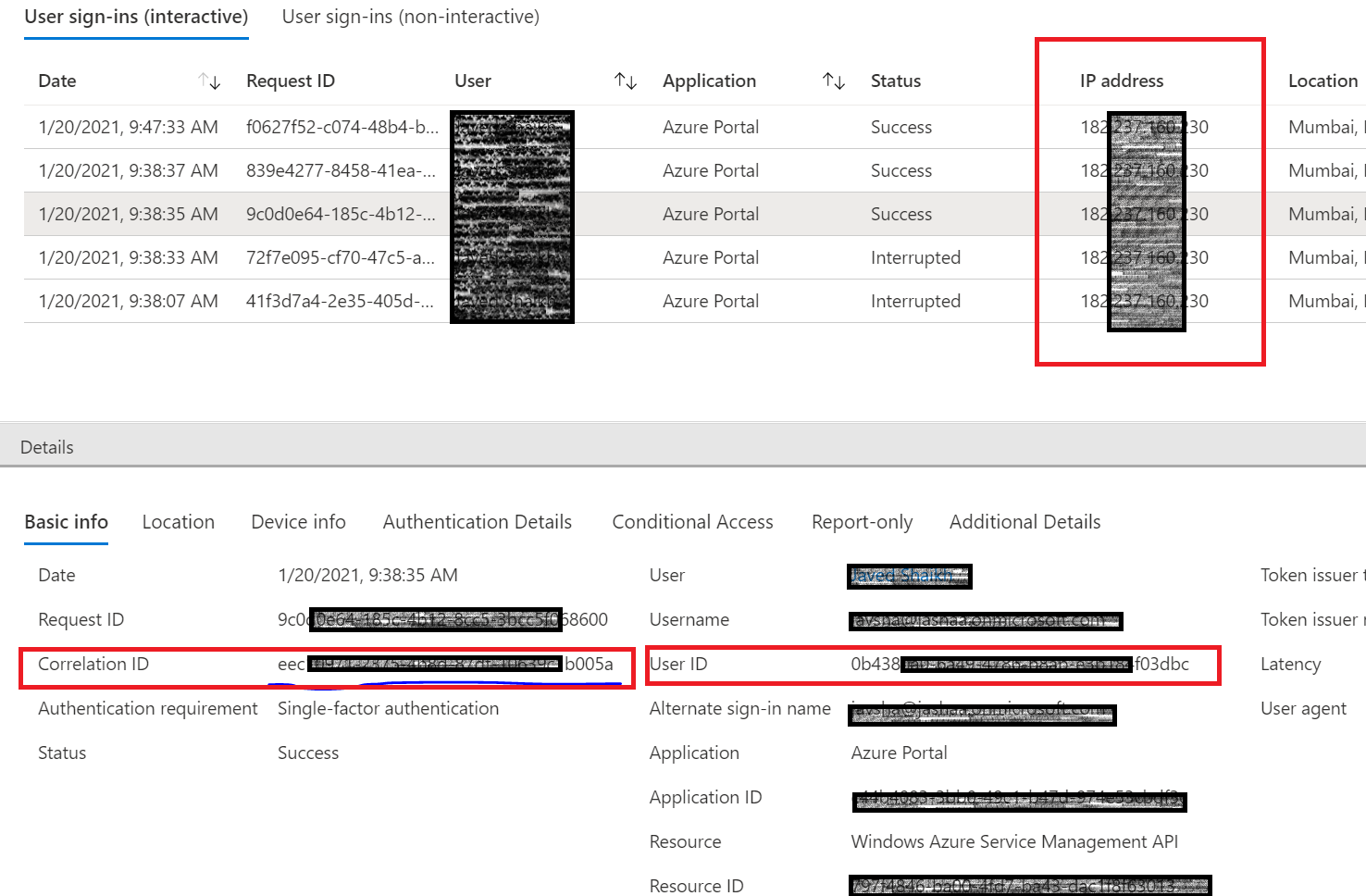
IP Address is included as a property in the columns of sign-in logs in Azure AD. Ref -> https://learn.microsoft.com/en-us/azure/active-directory/reports-monitoring/concept-sign-ins
So to get IP Address of the user whenever there is a password reset activity, you can correlate between the audit logs and the sign in logs. Please ref the correlation id from the audit logs for the SSPR activity and filter it in the sign in logs, from where you could get the IP address of the user.
Alternatively, you can match the Object Id in the Audit logs which should be the user id in the sign in logs along with the timestamp.
Audit Log :
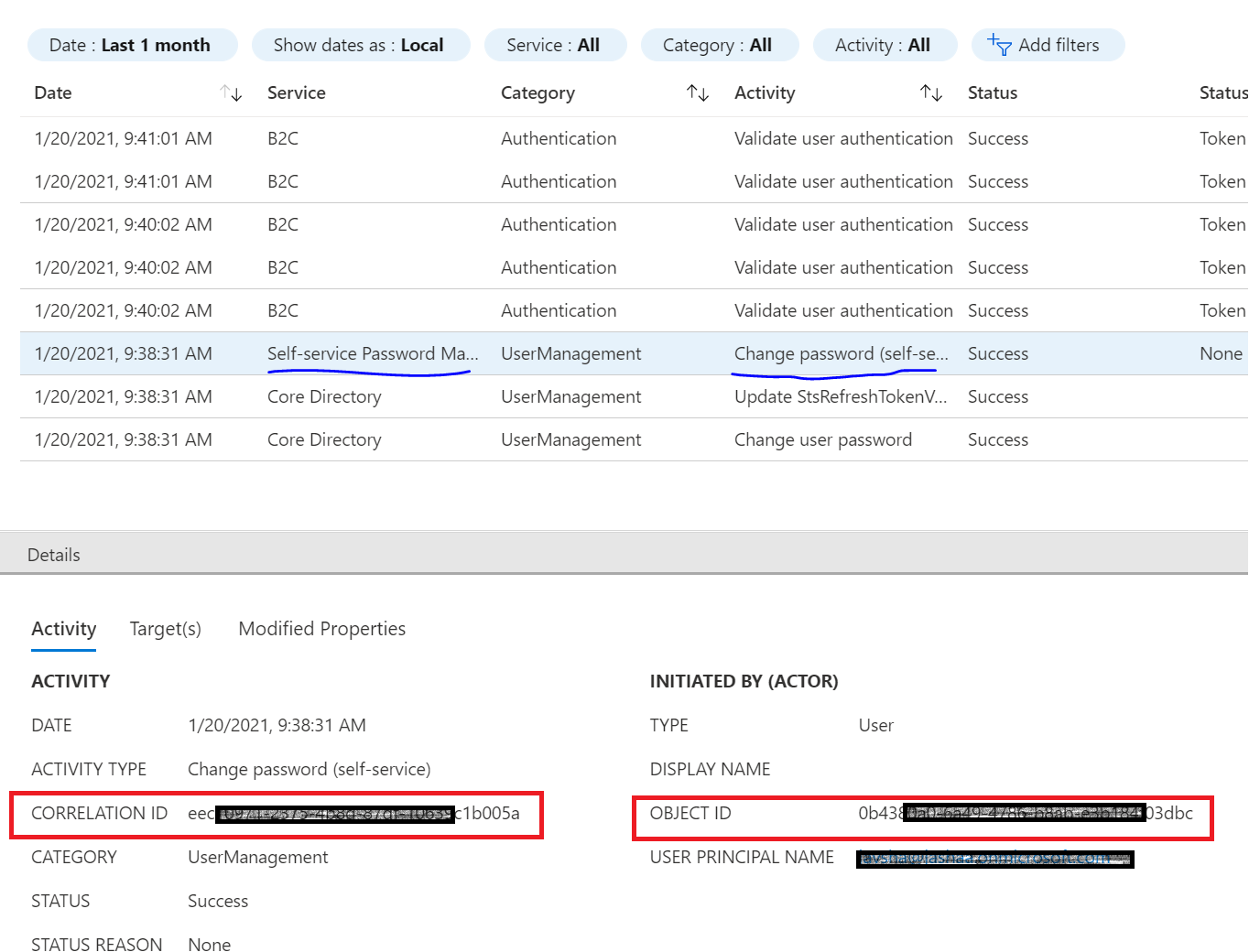
Sign in Log: