Microsoft Entra on-premises application provisioning to SCIM-enabled apps
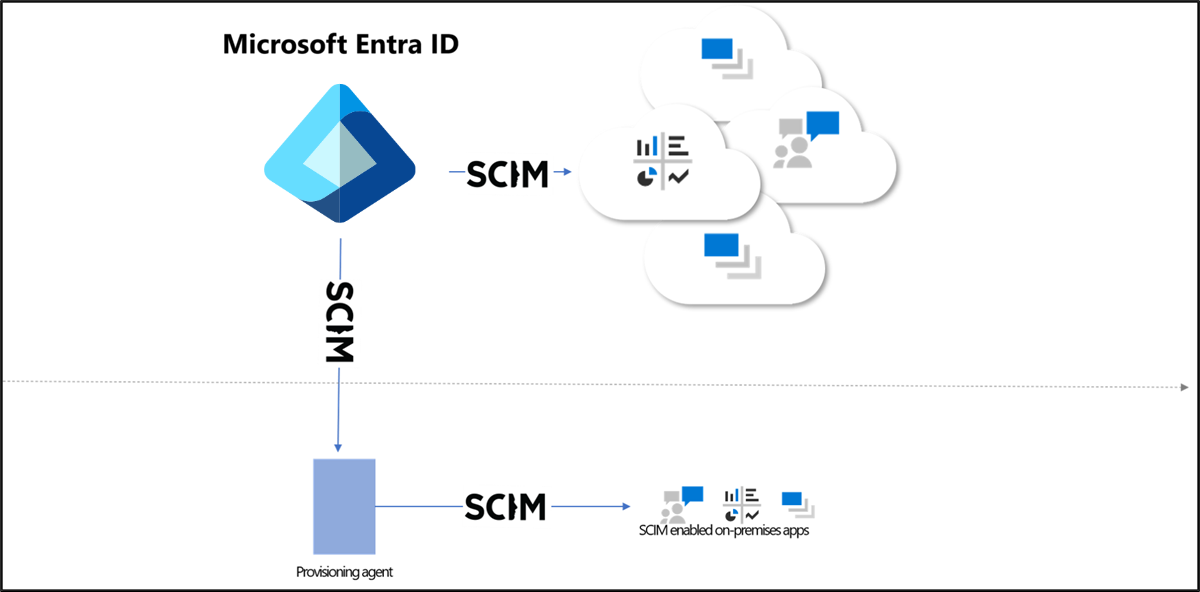
The Microsoft Entra provisioning service supports a SCIM 2.0 client that can be used to automatically provision users into cloud or on-premises applications. This article outlines how you can use the Microsoft Entra provisioning service to provision users into an on-premises application that's SCIM enabled. If you want to provision users into non-SCIM on-premises applications that use SQL as a data store, see the Microsoft Entra ECMA Connector Host Generic SQL Connector tutorial. If you want to provision users into cloud apps such as DropBox and Atlassian, review the app-specific tutorials.
Prerequisites
- A Microsoft Entra tenant with Microsoft Entra ID P1 or Premium P2 (or EMS E3 or E5). Using this feature requires Microsoft Entra ID P1 licenses. To find the right license for your requirements, see Compare generally available features of Microsoft Entra ID.
- Administrator role for installing the agent. This task is a one-time effort and should be an Azure account that's at least a Hybrid Identity Administrator.
- Administrators must be at least an Application Administrator, Cloud Application Administrator, or a custom role with permissions.
- A computer with at least 3 GB of RAM, to host a provisioning agent. The computer should have Windows Server 2016 or a later version of Windows Server, with connectivity to the target application, and with outbound connectivity to login.microsoftonline.com, other Microsoft Online Services and Azure domains. An example is a Windows Server 2016 virtual machine hosted in Azure IaaS or behind a proxy.
- Ensure your SCIM implementation meets the Microsoft Entra SCIM requirements. Microsoft Entra ID offers open-source reference code that developers can use to bootstrap their SCIM implementation, as described in Tutorial: Develop a sample SCIM endpoint in Microsoft Entra ID.
- Support the /schemas endpoint to reduce configuration required in the Azure portal.
Install and configure the Microsoft Entra Connect Provisioning Agent
- Sign in to the Microsoft Entra admin center as at least an Application Administrator.
- Browse to Identity > Applications > Enterprise applications.
- Search for the On-premises SCIM app application, give the app a name, and select Create to add it to your tenant.
- From the menu, navigate to the Provisioning page of your application.
- Select Get started.
- On the Provisioning page, change the mode to Automatic.
- Under On-premises Connectivity, select Download and install, and select Accept terms & download.
- Leave the portal and open the provisioning agent installer, agree to the terms of service, and select Install.
- Wait for the Microsoft Entra provisioning agent configuration wizard and then select Next.
- In the Select Extension step, select On-premises application provisioning and then select Next.
- The provisioning agent will use the operating system's web browser to display a popup window for you to authenticate to Microsoft Entra ID, and potentially also your organization's identity provider. If you are using Internet Explorer as the browser on Windows Server, then you may need to add Microsoft web sites to your browser's trusted site list to allow JavaScript to run correctly.
- Provide credentials for a Microsoft Entra administrator when you're prompted to authorize. The user is required to have at least the Hybrid Identity Administrator role.
- Select Confirm to confirm the setting. Once installation is successful, you can select Exit, and also close the Provisioning Agent Package installer.
Configure the connection via the provisioning agent
Sign in to the Microsoft Entra admin center as at least an Application Administrator.
Browse to Identity > Applications > Enterprise applications.
Search for the application created earlier.
From the menu, navigate to the Provisioning page of your application.
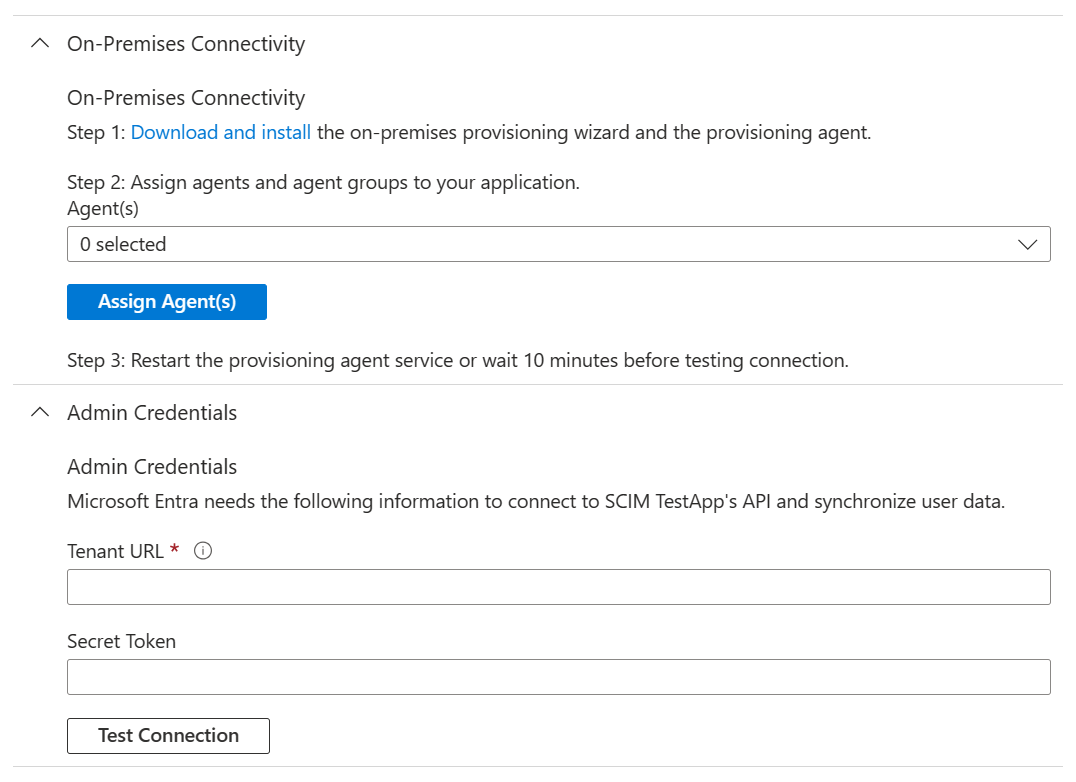
In the portal, on the On-Premises Connectivity section, select the agent that you deployed and select Assign Agent(s).
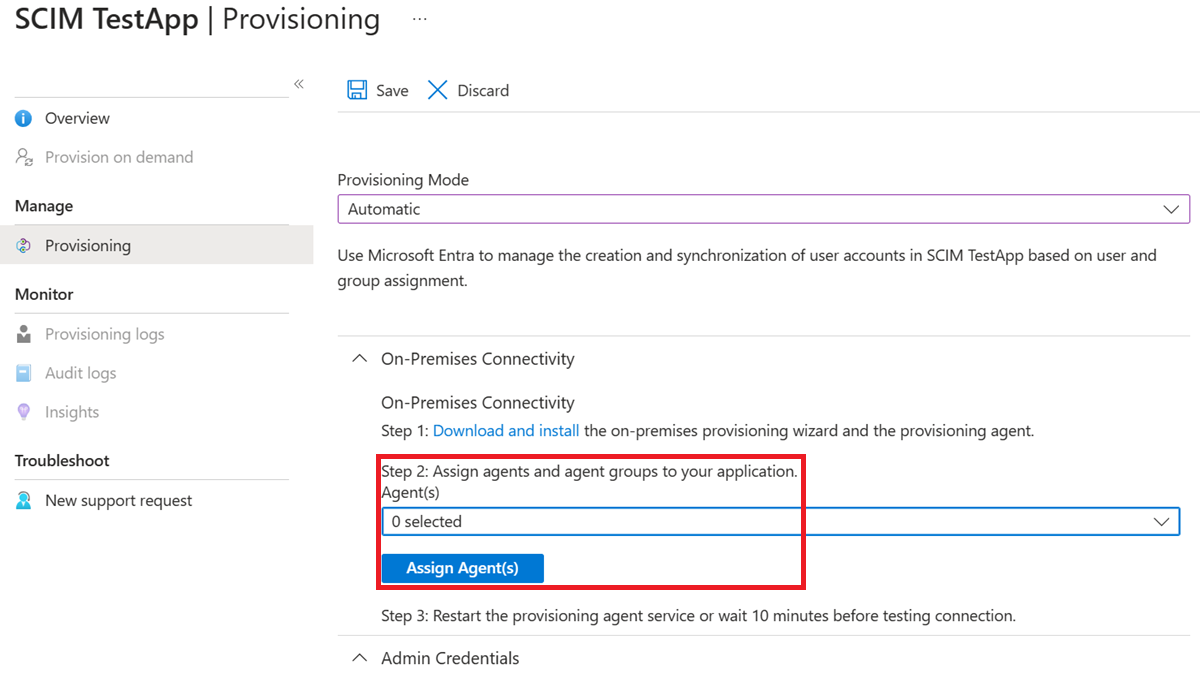
Restart the provisioning agent service or wait 10 minutes before testing connection.
In the Tenant URL field, enter the URL of the application's SCIM endpoint. Example:
https://api.contoso.com/scim/Copy the required OAuth bearer token for the SCIM endpoint into the Secret Token field.
Select Test Connection to have Microsoft Entra ID attempt to connect to the SCIM endpoint. If the attempt fails, error information is displayed.
Once the attempt to connect to the application succeeds, then select Save to save the admin credentials.
Keep this browser window open, as you complete the next step of configuration using the configuration wizard.
Provisioning to SCIM-enabled application
Once the agent is installed, no further configuration is necessary on-premises, and all provisioning configurations are then managed from the portal. Repeat the below steps for every on-premises application being provisioned via SCIM.
- Configure any attribute mappings or scoping rules required for your application.
- Add users to scope by assigning users and groups to the application.
- Test provisioning a few users on demand.
- Add more users into scope by assigning them to your application.
- Go to the Provisioning pane, and select Start provisioning.
- Monitor using the provisioning logs.
The following video provides an overview of on-premises provisioning.