Hello @BigfootDivorcedMe03 ,
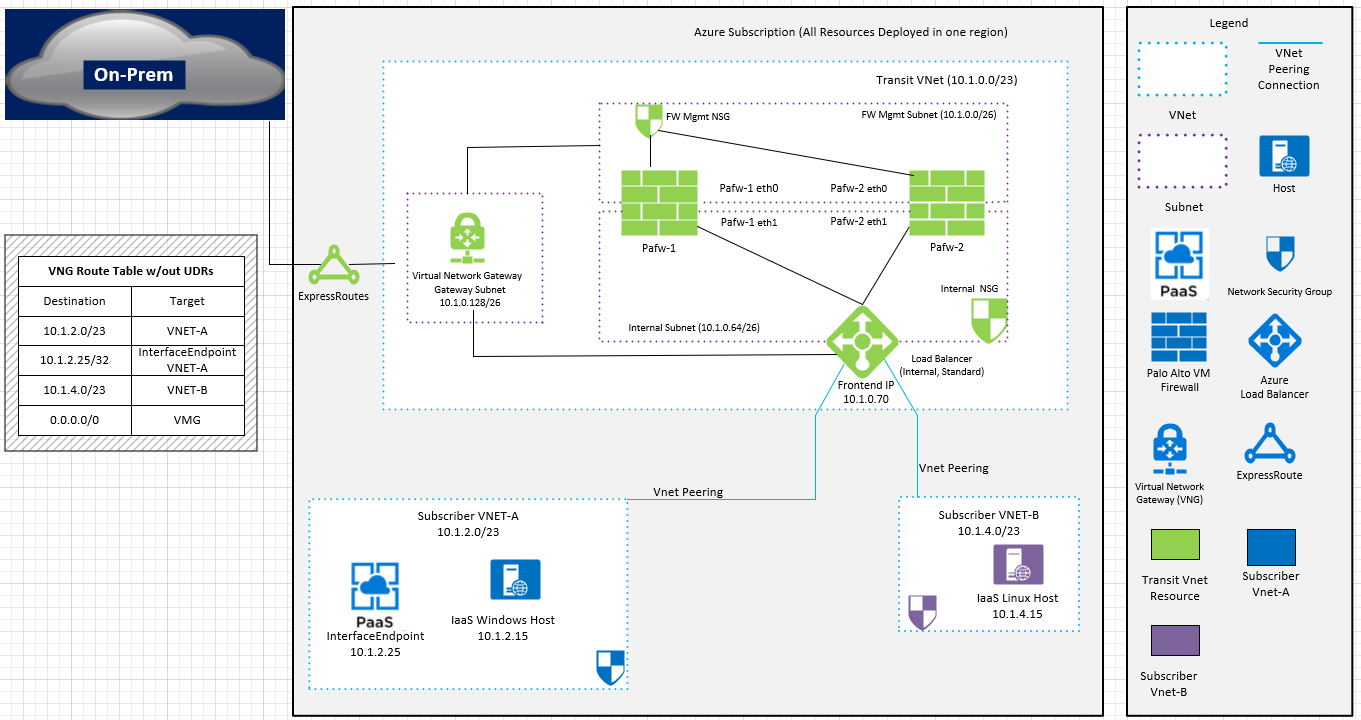
Yes, currently the only way to force the Private Endpoint traffic to firewall is to add UDR with /32 route. And hence, it is advised to use a dedicated Virtual Network for Private endpoints as shown in Scenario 1 of the below article as this configuration reduces administrative overhead and prevents running into the limit of 400 routes.
https://learn.microsoft.com/en-us/azure/private-link/inspect-traffic-with-azure-firewall
The resolution in your scenario would be the use of Public preview feature of UDR support in Private endpoints. This feature enables you to route traffic destined for a Private Endpoint over an NVA or Firewall without complex configuration of specific routes (UDR) on the subnets. This also enables you to easily scale on Private Endpoints without reaching any limit on UDRs while satisfying auditing and compliance requirements.
However, this preview version is provided without a service level agreement, and it's not recommended for production workloads. Certain features might not be supported or might have constrained capabilities.
Refer : https://learn.microsoft.com/en-us/azure/private-link/private-endpoint-overview#limitations
So, you can either opt for this Public preview of UDR support by registering the feature at the moment or can wait till it's GA with SLA agreement.
In case, you would like to try out the Public preview of UDR support, you can refer the below article:
https://azure.microsoft.com/en-us/updates/public-preview-of-private-link-udr-support/
NOTE: This feature will be available in the following regions:
UsEast2Euap, UsCentralEuap, WestCentralUS, WestUS, WestUS2, EastUS, EastUS2
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.