@LHIND, CARSTEN Thank you for reaching out to Microsoft Q&A. I understand that you want to limit access to your Storage Account to the managed identity. Please correct me otherwise.
The following roles permit a security principal to access data in a storage account.
- Storage Blob Data Owner: Full access to Blob storage containers and data. This access permits the security principal to set the owner an item, and to modify the ACLs of all items.
- Storage Blob Data Contributor: Read, write, and delete access to Blob storage containers and blobs. This access does not permit the security principal to set the ownership of an item, but it can modify the ACL of items that are owned by the security principal.
- Storage Blob Data Reader: Read and list Blob storage containers and blobs.
Note- Roles such as Owner, Contributor, Reader, and Storage Account Contributor permit a security principal to manage a storage account, but do not provide access to the data within that account. However, these roles (excluding Reader) can obtain access to the storage keys, which can be used in various client tools to access the data.
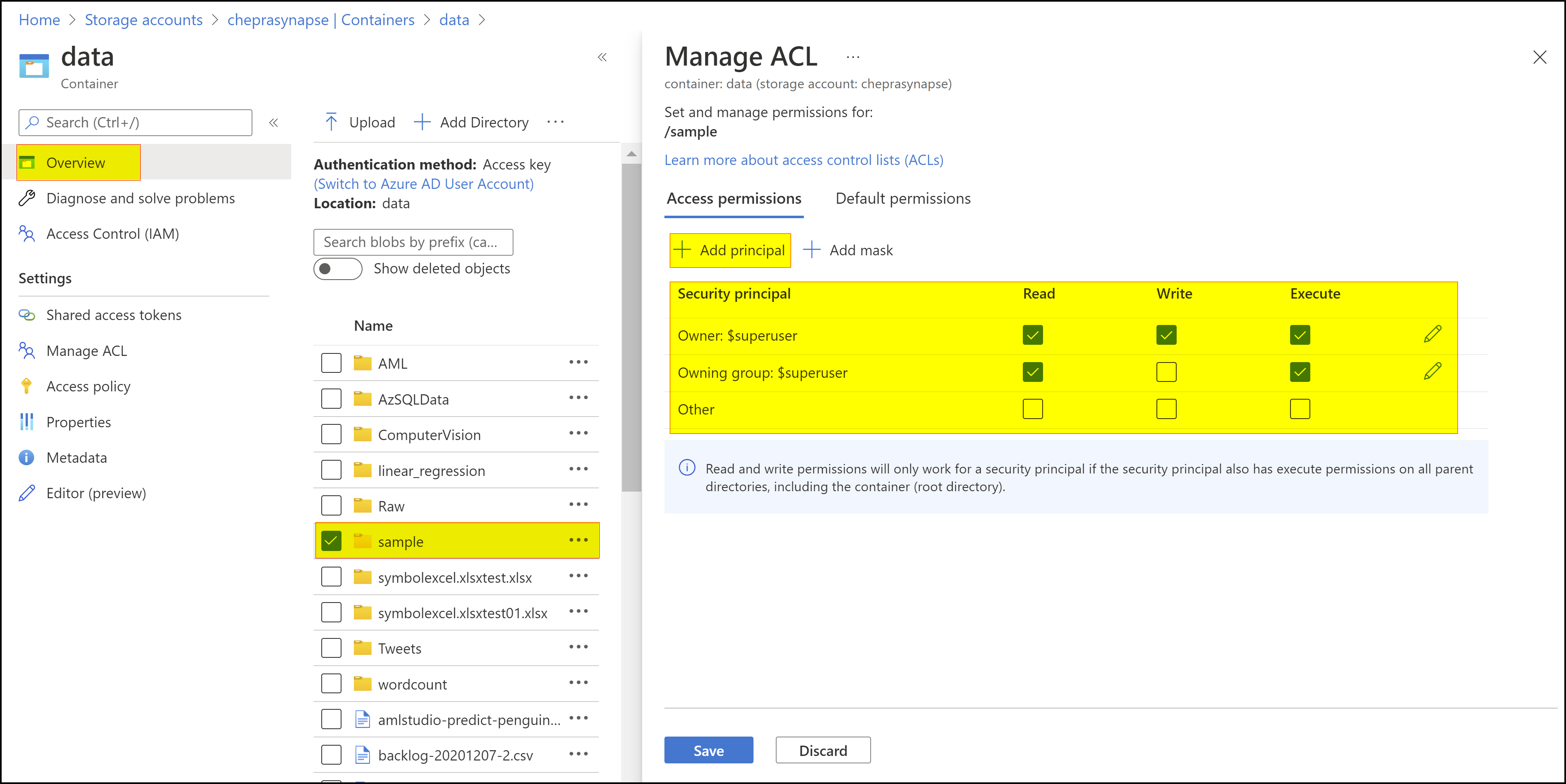
You can also use ACLs with ADLS Gen2 in combination with Azure Roles for the security principal. You can check out the Permissions table: Combining Azure RBAC and ACL to see how this can work. Hope this helps.
Please let us know if you have any more questions and we will be glad to assist you further. Thank you!
Remember:
Please accept an answer if correct. Original posters help the community find answers faster by identifying the correct answer. Here is how.
Want a reminder to come back and check responses? Here is how to subscribe to a notification.

 or upvote
or upvote