Azure Confidential Computing
Microsoft Cloud for Sovereignty enables customers to configure and protect their data and resources in ways that help them comply with their specific regulatory, security, and sovereignty requirements. This process ensures that customer data isn't accessible to parties outside the customer’s control, even to cloud providers, administrators, or users. When you combine Azure Confidential Computing (ACC) with Microsoft Cloud for Sovereignty, they provide control over access to customer workloads.
Confidential computing is an industry term defined by the Confidential Computing Consortium (CCC), a foundation dedicated to defining and accelerating the adoption of confidential computing. The CCC defines confidential computing as the protection of data in use by performing computations in a hardware-based Trusted Execution Environment (TEE).
A TEE is an environment that enforces the execution of only authorized code. Any code outside that environment can't read or tamper with any data in the TEE. The confidential computing threat model aims to remove or reduce the ability of a cloud provider operator and other actors in the tenant's domain to access code and data while being executed.
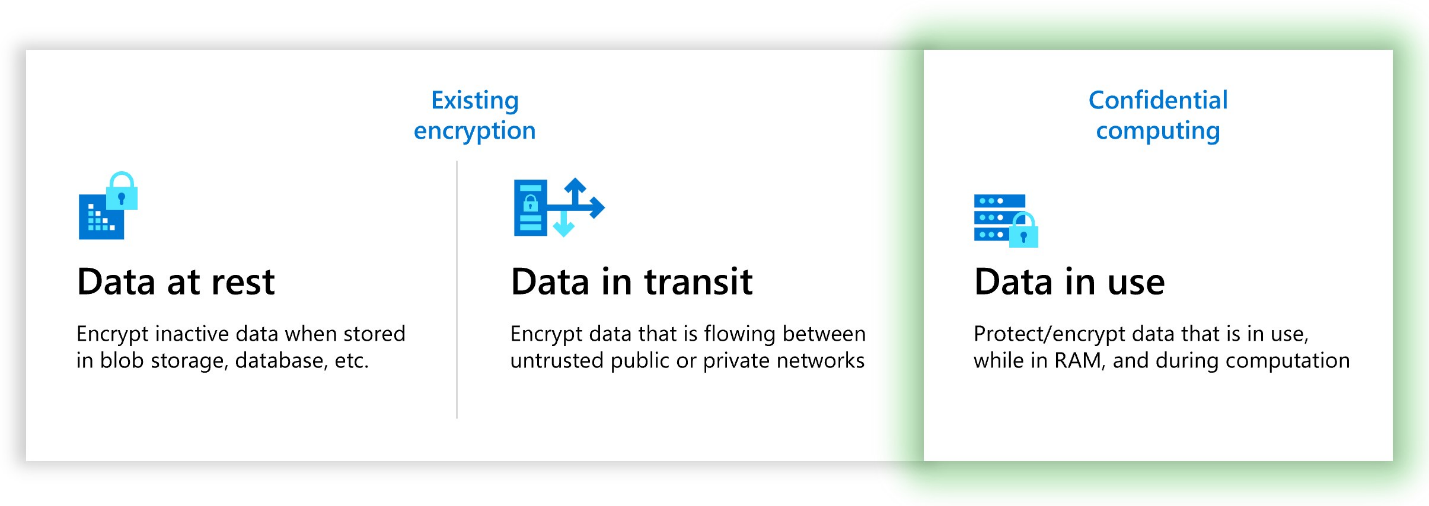
When used with data encryption at rest and in transit, confidential computing eliminates the single largest barrier of encryption - encryption while in use. It protects sensitive or highly regulated data sets and application workloads in a secure public cloud platform. Confidential computing extends beyond generic data protection. TEEs also help protect proprietary business logic, analytics functions, machine learning algorithms, or entire applications.
ACC reduces the need for trust across various aspects of the compute cloud infrastructure. Azure confidential computing minimizes trust in both the system processes, such as the host OS kernel and the hypervisor, and human operators that include the VM admin and the host administrator. In combination with existing solutions, which protect data at rest, such as Microsoft Data Encryption and in transit such as TLS or IPsec, data is now protected while in use because the memory itself remains encrypted, i.e complete protection across the data lifecycle.
With the guardrails and compliance enforcement of Microsoft Cloud for Sovereignty, ACC provides enhanced protection of sovereign, sensitive or highly regulated data and workloads within the scalability, flexibility, availability, and powerful services of the Azure Public Cloud platform. For more on the benefits of Azure Confidential Computing, see Azure confidential computing products.
Sovereignty supported in Azure Confidential Computing
Data sovereignty ensures that customers uniquely control customer resources, such as VMs, and others can't access these resources. ACC helps customers achieve data sovereignty by providing confidentiality of the entire root of trust, from hardware to application. Azure DCasv5 and DCadsv5-series confidential virtual machines (CVMs) are hardware isolated VMs that protect data in memory from other VMs, hypervisor, and host management code. Even Azure engineers with administrative access to the VM host are unable to access customer data in memory. This series also offers OS disk pre-encryption before VM provisioning with different key management solutions.
Sovereignty is enhanced at every level by providing confidential computing environments for:
- Microsoft Azure Attestation, a remote attestation service that validates the trustworthiness of multiple TEEs and verifies the integrity of the binaries running inside the TEEs. This validation of the fundamental root of trust is essential to ensure the sovereignty of the data.
- Trusted launch brings hardened security features – secure boot, virtual trusted platform module, and boot integrity monitoring – that protect against boot kits, rootkits, and kernel-level malware.
- Trusted Hardware Identity Management, a service that manages cache management of certificates for all TEEs that reside in Azure and provides Trusted Computing Base (TCB) information to enforce a minimum baseline for attestation solutions.
Many customers use the Azure Kubernetes Service (AKS) to manage their container-based applications, and storage and networking components. To help meet sovereignty, confidentiality, and security requirements, customers can use Azure App-enclave aware containers that run on AKS. Confidential computing nodes on AKS use Intel SGX to create isolated enclave environments in the nodes between each container application. Azure is also previewing Confidential VM node pool support on AKS with AMD SEV-SNP VM components. AKS is the first to market in enabling confidential VM with AMD SEV-SNP node pools in Kubernetes, adding defense-in-depth to Azure's hardened security profile.
Confidential secrets management
Azure Key Vault (AKV) Managed HSM is a fully managed, highly available, single-tenant, standards-compliant cloud service that safeguards application cryptographic keys using FIPS 140-2 Level 3 validated Hardware Security Modules (HSM). AKV mHSM uses the same APIs as Azure Key Vault Standard and Premium and integrates with most Azure services to enable service encryption with Customer Managed Keys. Hardware protection ensures that only the customer can access the encryption keys. Even Azure engineers can't access them.
Secure Key Release (SKR) is a functionality of Azure Key Vault (AKV) Managed HSM and Premium offering that provides more access control. Secure key release enables the release of an HSM protected key from AKV to an attested Trusted Execution Environment (TEE), such as a secure enclave, VM based TEEs, etc. SKR adds another layer of protection to your data decryption/encryption keys where you can target an application + TEE runtime environment with known configuration to get access to the key material. The SKR policies defined at the time of exportable key creation govern access to these keys.
Confidential analytics services
Azure’s public sector and regulated industry customers have an urgent need for advanced analytics capabilities that help them comply with their sovereignty, privacy, and security requirements. Microsoft Cloud for Sovereignty helps these customers to use services such as:
- With Always Encrypted with secure enclaves in Azure SQL service, customers can run SQL queries directly inside a TEE, to help ensure that sensitive data is protected from malware and high privileged unauthorized users.
- Azure Databricks with Confidential Computing VM can help customers run their analytics, machine learning and other workloads in a privacy preserving way.
- The rapid growth of Internet of Things (IoT) opens new sovereignty risks because IoT Edge devices are outside the customer’s geographical control, and bad actors may physically access them, putting these devices at elevated risk for compromise. Confidential IoT Edge adds trust and integrity at the edge by protecting the access to data captured by and stored inside an IoT device, reducing the risk of tampering or compromise.
- Customers are encouraged to use Microsoft Azure Confidential Ledger (ACL) to manage sensitive data records. ACL runs exclusively on hardware-backed secure enclaves in a heavily monitored and isolated runtime environment, which protects sensitive data records and makes them immutable.
Adopt Confidential Computing within Microsoft Cloud for Sovereignty
Microsoft Cloud for Sovereignty customers can use the Sovereign Landing Zone to streamline the adoption of Microsoft confidential computing features within a compliant and sovereign environment.
For guidance on getting started with using ACC in the Sovereign Landing Zone (SLZ), see SLZ on GitHub.