Enable Trusted launch on existing Azure Gen2 VMs
Applies to: ✔️ Linux VM ✔️ Windows VM ✔️ Generation 2 VM
Azure Virtual Machines supports enabling Azure Trusted launch on existing Azure Generation 2 virtual machines (VM) by upgrading to the Trusted launch security type.
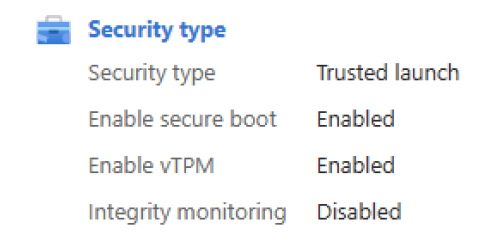
Trusted launch is a way to enable foundational compute security on Azure Generation 2 VMs and protects against advanced and persistent attack techniques like boot kits and rootkits. It does so by combining infrastructure technologies like Secure Boot, virtual Trusted Platform Module (vTPM), and boot integrity monitoring on your VM.
Important
Support for enabling Trusted launch on existing Azure Generation 1 VMs is currently in preview. Refer to Upgrade existing Azure Gen1 VMs and enable Trusted launch.
Prerequisites
Azure VM is configured with:
- Trusted launch supported size family.
- Trusted launch supported operating system (OS) version. For custom OS images or disks, the base image should be Trusted launch capable.
- Azure VM isn't using features currently not supported with Trusted launch.
- Azure Backup, if enabled, for VMs should be configured with the Enhanced Backup policy. The Trusted launch security type can't be enabled for VMs configured with Standard policy backup protection.
- Existing Azure VM backup can be migrated from the Standard to the Enhanced policy. Follow the steps in Migrate Azure VM backups from Standard to Enhanced policy (preview).
Best practices
- Enable Trusted launch on a test Generation 2 VM and determine if any changes are required to meet the prerequisites before you enable Trusted launch on Generation 2 VMs associated with production workloads.
- Create restore points for Azure Generation 2 VMs associated with production workloads before you enable the Trusted launch security type. You can use the restore points to re-create the disks and Generation 2 VM with the previous well-known state.
Enable Trusted launch on an existing VM
Note
- After you enable Trusted launch, currently VMs can't be rolled back to the Standard security type (non-Trusted launch configuration).
- vTPM is enabled by default.
- We recommend that you enable Secure Boot, if you aren't using custom unsigned kernel or drivers. It's not enabled by default. Secure Boot preserves boot integrity and enables foundational security for VMs.
Enable Trusted launch on an existing Azure Generation 2 VM by using the Azure portal.
Sign in to the Azure portal.
Confirm that the VM generation is V2 and select Stop for the VM.
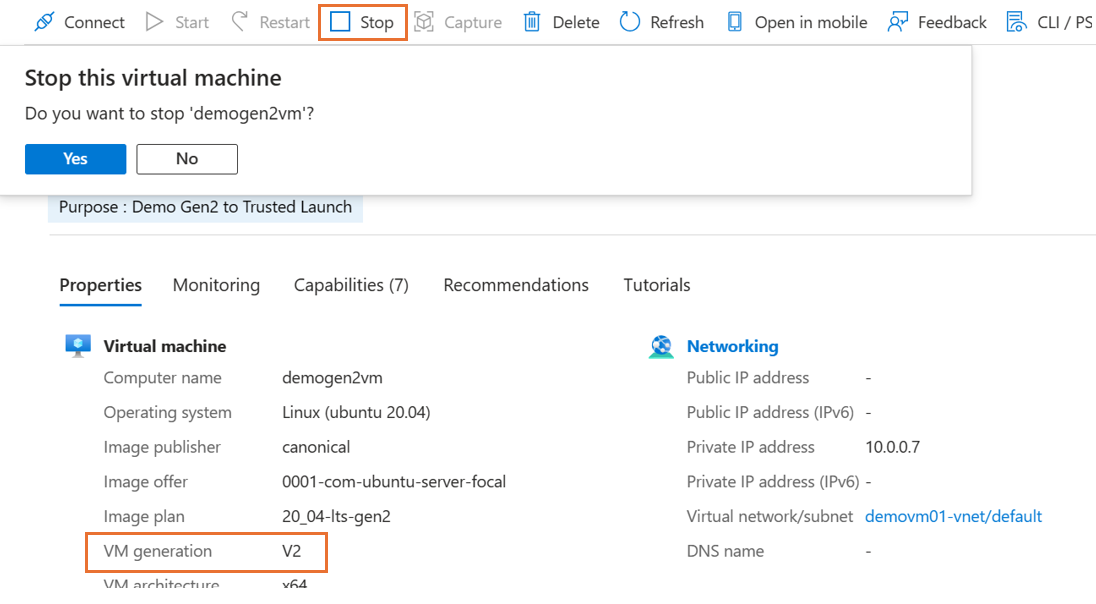
On the Overview page in the VM properties, under Security type, select Standard. The Configuration page for the VM opens.
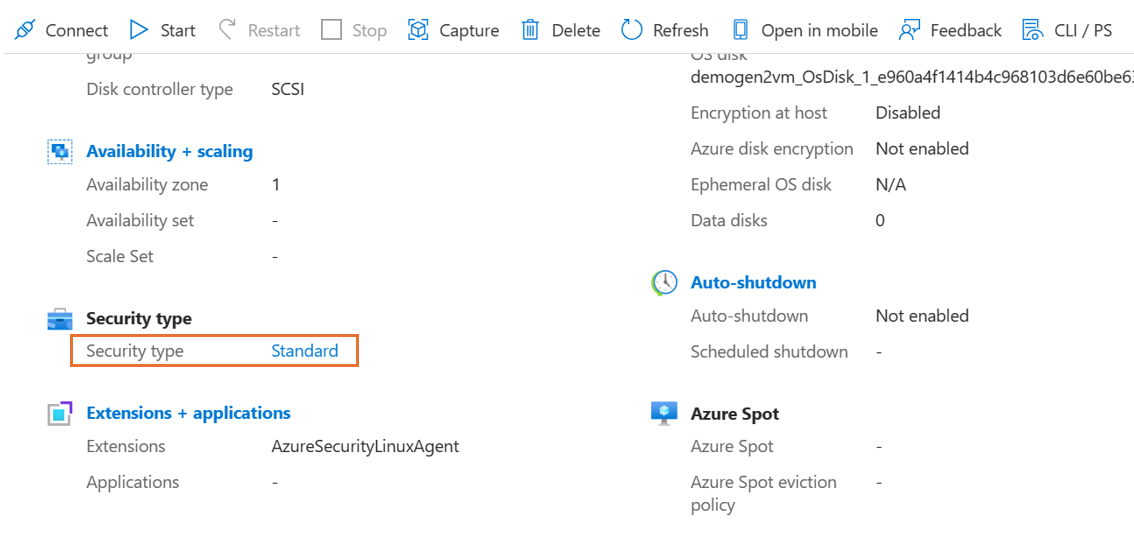
On the Configuration page, under the Security type section, select the Security type dropdown list.
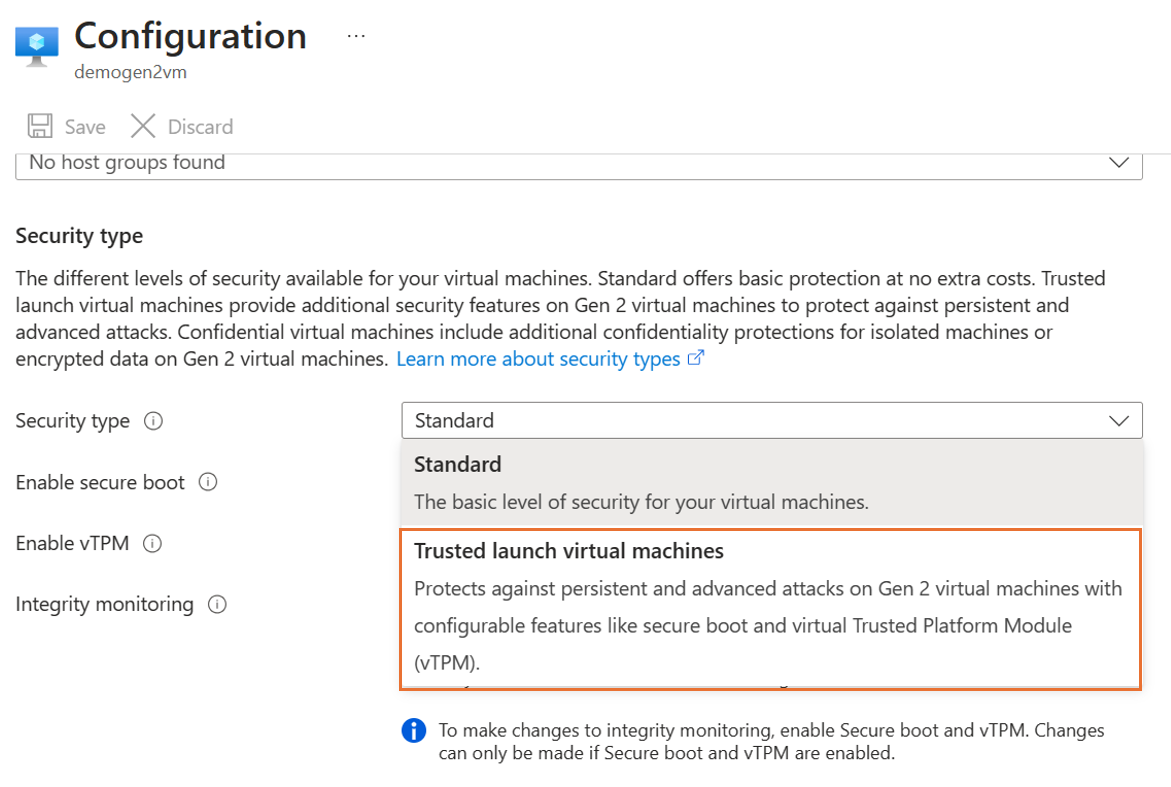
Under the dropdown list, select Trusted launch. Select checkboxes to enable Secure Boot and vTPM. After you make the changes, select Save.
Note
- Generation 2 VMs created by using Azure Compute Gallery (ACG), Managed image, or an OS disk can't be upgraded to Trusted launch by using the portal. Ensure that the OS version is supported for Trusted launch. Use PowerShell, the Azure CLI, or an Azure Resource Manager template (ARM template) to run the upgrade.
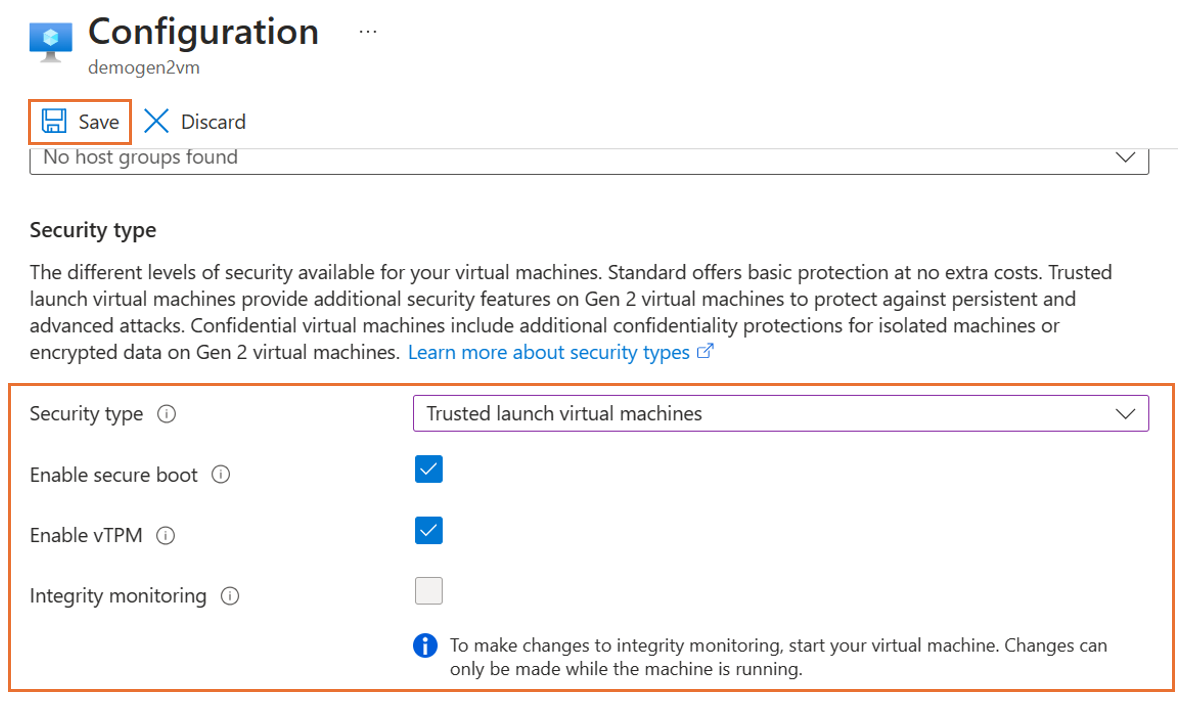
After the update successfully finishes, close the Configuration page. On the Overview page in the VM properties, confirm the Security type settings.
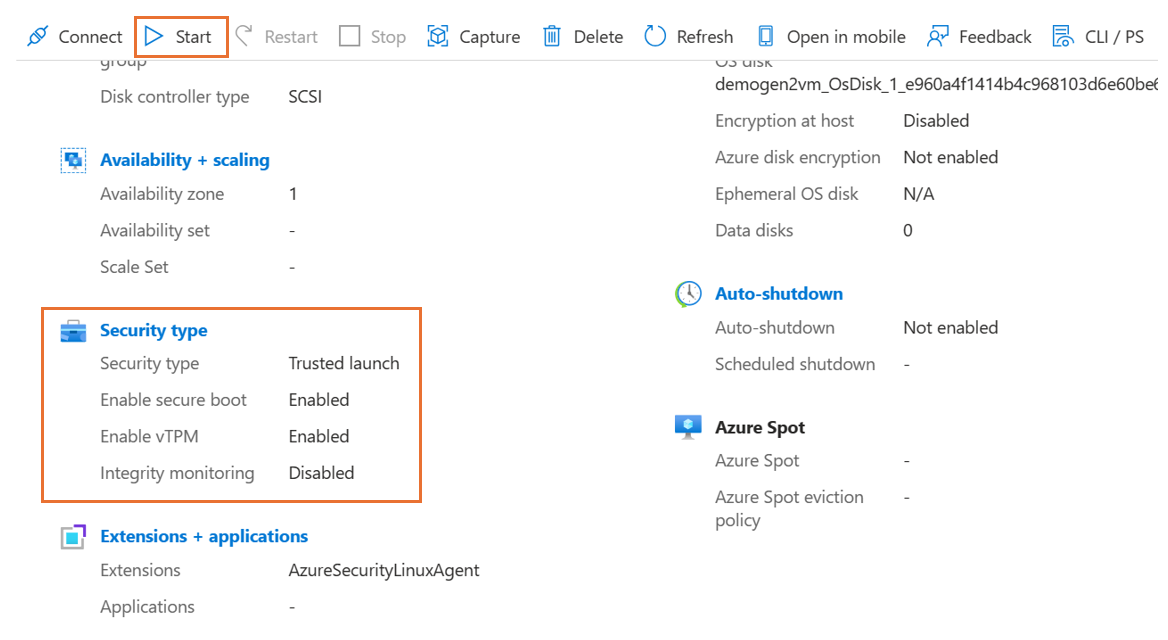
Start the upgraded Trusted launch VM. Verify that you can sign in to the VM by using either the Remote Desktop Protocol (RDP) for Windows VMs or the Secure Shell Protocol (SSH) for Linux VMs.
Azure Advisor Recommendation
Azure Advisor populates an Enable Trusted launch foundational excellence, and modern security for Existing Generation 2 VM(s) operational excellence recommendation for existing Generation 2 VMs to adopt Trusted launch, a higher security posture for Azure VMs at no extra cost to you. Ensure Generation 2 VM has all prerequisites to migrate to Trusted launch, follow all the best practices including validation of OS image, VM Size, and creating restore points. For the Advisor recommendation to be considered complete, follow the steps outlined in the Enable Trusted launch on an existing VM to upgrade the virtual machines security type and enable Trusted launch.
What if there is Generation 2 VMs, that doesn't fit the prerequisites for Trusted launch?
For a Generation 2 VM that doesn't meet the prerequisites to upgrade to Trusted launch, look how to fulfill the prerequisites. For example, If using a virtual machine size not supported, look for an equivalent Trusted launch supported size that supports Trusted launch.
Note
Please dismiss the recommendation if Gen2 virtual machine is configured with VM size families which are currently not supported with Trusted launch like MSv2-series.
Related content
- Refer to Deploy Trusted launch virtual machines for enabling Trusted launch on new virtual machine & scale set deployments.
- Refer to boot integrity monitoring for enabling boot integrity monitoring and monitor the health of the VM by using Microsoft Defender for Cloud.
- Learn more about Trusted launch and review frequently asked questions.