Hello,
Let me try to summarize the facts:
1, We have been using only Kerberos authentication for a long time.
2, NTLM we have GPOs disabled for domain computers - also for a long time (using GPO MSFT Security Baselines - Computer).
3, We have not made any changes on the domain controller side, domain computers and GPO policies, firewalls etc.
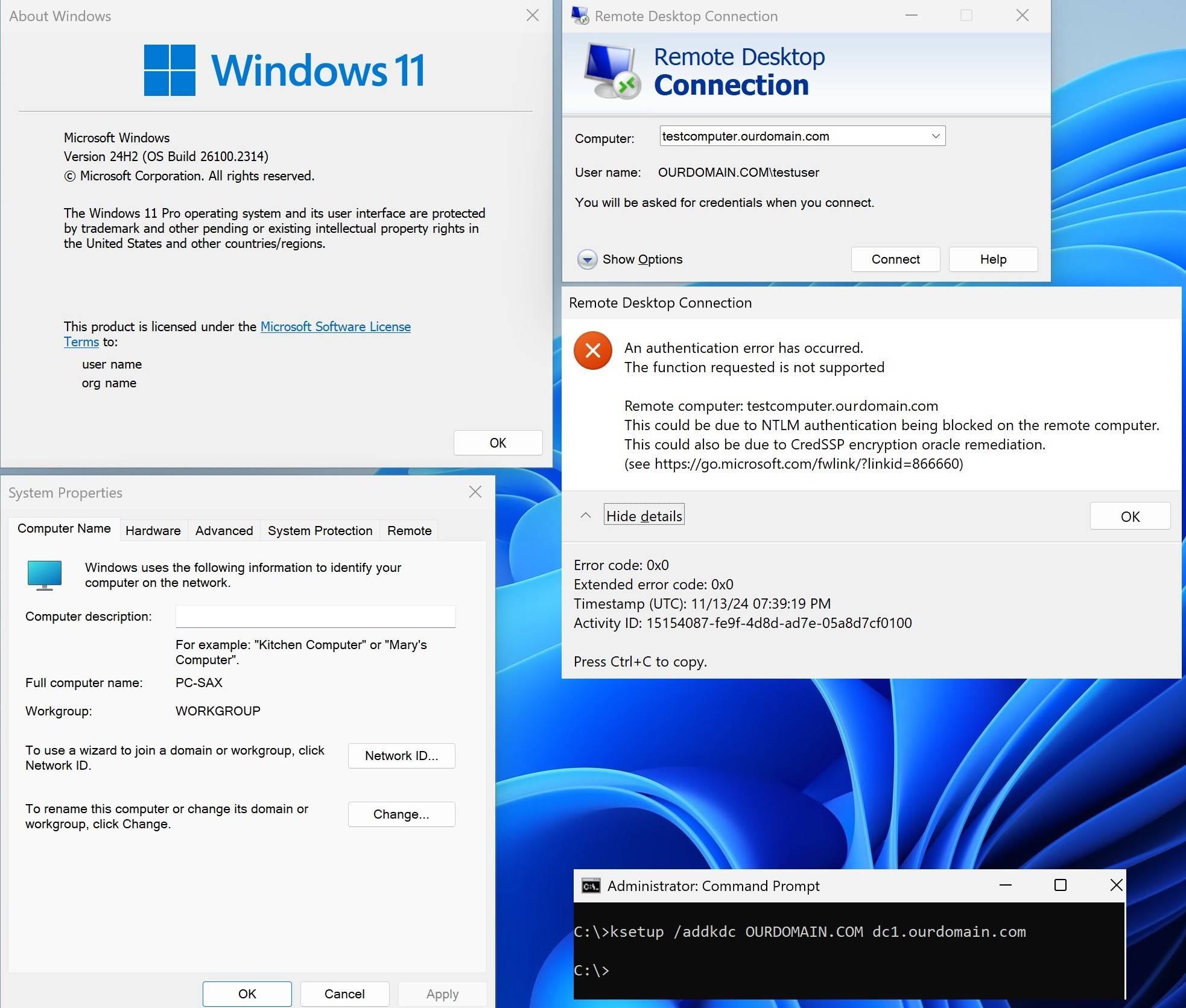
4, Managed laptops or BYOD can success fully establish Kerberos authentication to their computer by RDP connection until managed laptops or BOYD was on Win 11 23H2.
5,
Test A:
Client (Managed laptops or BYOD) = with Win11 23H2
Target (Domain PC) = with Win11 24H2
RDP kerberos authentication Works!
Test B:
Client (Managed laptops or BYOD) = with Win11 24H2
Target (Domain PC) = with Win11 24H2
RDP kerberos authentication FAILED - not working.
Test C:
Client (Managed laptops or BYOD) = with MacOS
Target (Domain PC) = with Win11 24H2
RDP kerberos authentication Works too!
NOTE: MacOS has similar settings to Windows (ksetup /addkdc)
/etc/krb5.conf
[libdefaults]
default_realm = OURDOAMIN.COM
[realms]
OURDOMAIN.COM = {
kdc = dc1.ourdomain.com
}
This allows us to rule out incorrect settings, e.g. firewall, DNS forwarding, etc.
The problem is only between the latest versions of Windows 11 from 24H2 to 24H2.
If I enable debug log
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters
Registry Value: LogLevel
Value Type: REG_DWORD
Value Data: 0x1
The logos are not telling because they are exactly the same even though RDP works or not
RDP kerberos auth. working combination (23H2 -> 23H2, 23H2 -> 24H2)
RDP kerberos auth not working combination (24H2 -> 24H2, 24H2 -> 23H2)
Logs PC-BOYD from 24H2 to 24H2 - RDP Kerberos not working
A Kerberos error message was received:
on logon session PC-BYOD\testuser
Client Time:
Server Time: 5:47:23.0000 12/20/2024 Z
Error Code: 0x19 KDC_ERR_PREAUTH_REQUIRED
Extended Error:
Client Realm:
Client Name:
Server Realm: OURDOMAIN.COM
Server Name: krbtgt/OURDOMAIN.COM
Target Name: krbtgt/******@OURDOMAIN.COM
Error Text:
File: onecore\ds\security\protocols\kerberos\client2\logonapi.cxx
Line: 10a7
Error Data is in record data.
A Kerberos error message was received:
on logon session PC-BYOD\testuser
Client Time:
Server Time: 5:47:23.0000 12/20/2024 Z
Error Code: 0x34 KRB_ERR_RESPONSE_TOO_BIG
Extended Error:
Client Realm:
Client Name:
Server Realm: OURDOMAIN.COM
Server Name: krbtgt/OURDOMAIN.COM
Target Name: krbtgt/******@OURDOMAIN.COM
Error Text:
File: onecore\ds\security\protocols\kerberos\client2\logonapi.cxx
Line: 10a7
Error Data is in record data.
A Kerberos error message was received:
on logon session
Client Time:
Server Time: 5:47:23.0000 12/20/2024 Z
Error Code: 0x34 KRB_ERR_RESPONSE_TOO_BIG
Extended Error:
Client Realm:
Client Name:
Server Realm: OURDOMAIN.COM
Server Name: TERMSRV/pc-n3z.OURDOMAIN.COM
Target Name: TERMSRV/pc-n3z.******@OURDOMAIN.COM
Error Text:
File: onecore\ds\security\protocols\kerberos\client2\kerbtick.cxx
Line: 135a
Error Data is in record data.
Logs NB-MANAGED from 23H2 to 23H2 - RDP kerberos auth Working
A Kerberos error message was received:
on logon session NB-MANAGED\Test
Client Time:
Server Time: 7:33:40.0000 12/20/2024 Z
Error Code: 0x19 KDC_ERR_PREAUTH_REQUIRED
Extended Error:
Client Realm:
Client Name:
Server Realm: OURDOMAIN.COM
Server Name: krbtgt/OURDOMAIN.COM
Target Name: krbtgt/******@OURDOMAIN.COM
Error Text:
File: onecore\ds\security\protocols\kerberos\client2\logonapi.cxx
Line: e35
Error Data is in record data.
A Kerberos error message was received:
on logon session NB-MANAGED\Test
Client Time:
Server Time: 7:33:40.0000 12/20/2024 Z
Error Code: 0x34 KRB_ERR_RESPONSE_TOO_BIG
Extended Error:
Client Realm:
Client Name:
Server Realm: OURDOMAIN.COM
Server Name: krbtgt/OURDOMAIN.COM
Target Name: krbtgt/******@OURDOMAIN.COM
Error Text:
File: onecore\ds\security\protocols\kerberos\client2\logonapi.cxx
Line: e35
Error Data is in record data.
A Kerberos error message was received:
on logon session
Client Time:
Server Time: 7:33:40.0000 12/20/2024 Z
Error Code: 0x34 KRB_ERR_RESPONSE_TOO_BIG
Extended Error:
Client Realm:
Client Name:
Server Realm: OURDOMAIN.COM
Server Name: TERMSRV/pc-5q0.OURDOMAIN.COM
Target Name: TERMSRV/pc-5q0.******@OURDOMAIN.COM
Error Text:
File: onecore\ds\security\protocols\kerberos\client2\kerbtick.cxx
Line: 1300
Error Data is in record data.
It is possible that this is a bug in version 24H2.
But your development team should know what is technologically new and find out the cause of this behavior.
I have exhausted all possibilities.