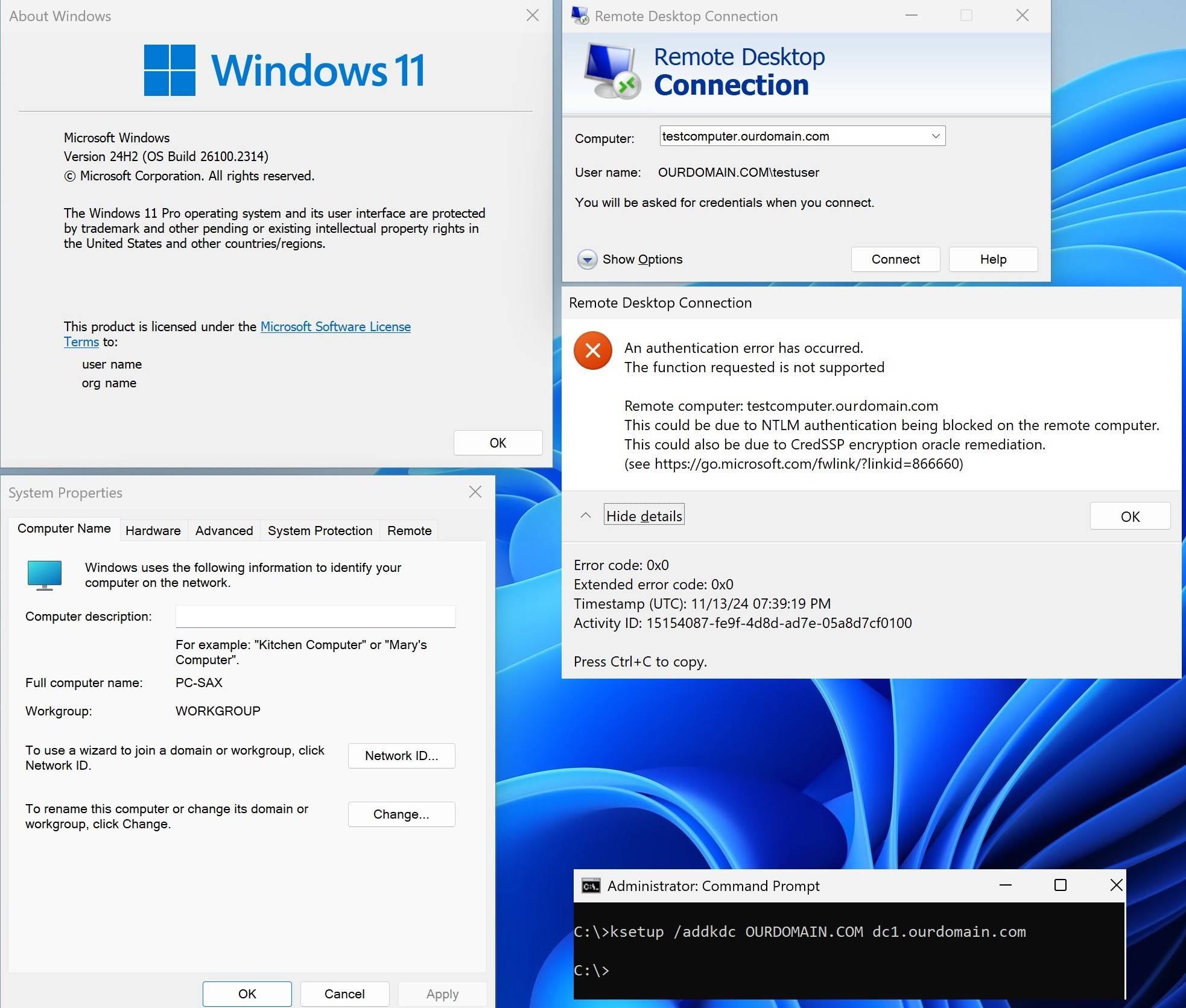
After update to latest Win 11 24H2 RDP kerberos authentication from non-domain PC to domain joined PC stop working:
Error message:
An authentication error has occurred.
The function requested is not supported.
Remote Computer : computer.ourdomain.com
This cloud be due to NTLM authentication being blocked on the remote computer.
This could also be due to CredSSP encryption oracle remediation.
Error code: 0x0
Extended error code: 0x0
Setup - Non-domain computer:
( home office users BYOD device with Win11 Pro updated to 24H2 )
1, ksetup /addkdc OURDOMAIN.COM dc1.ourdomain.com
2, reboot
3, Dialed VPN to company internal network
4, mstsc - RDP Connection from nondomain (BYOD) to company domain joined computer:
Computer: testcomputer.ourdomain.com
User name: OURDOMAIN.COM\testuser
5, Error (attached screenshot)
Setup – Domain computer:
Domain computer has Kerberos Authentication and valid RDP certificate.
GPO settings:
Set client connection encryption lever = High Level
Require use of specific security layer for remote (RDP) connections: Security Layer = SSL
Require user authentication for remote connections by using Network Level Authentication = Enable
This setup work until fully updated 23H2, after upgrade to 24H2, mstsc (RDP) stop working with the same setup.
As a workaround, NLA can be turned off in the GPO for domain computers, but this is a security degradation.
or as admin run before RDP command: klist add_bind OURDOAMIN.COM dc1.ourdomain.com but for this has user no rights.
The funny thing is that for example tested from MacOs (non-joined) RDP authenticated with kerberos works.
MacOS has for example this settings:
/etc/krb5.conf
[libdefaults]
default_realm = OURDOAMIN.COM
[realms]
OURDOMAIN.COM = {
kdc = dc1.ourdomain.com
}