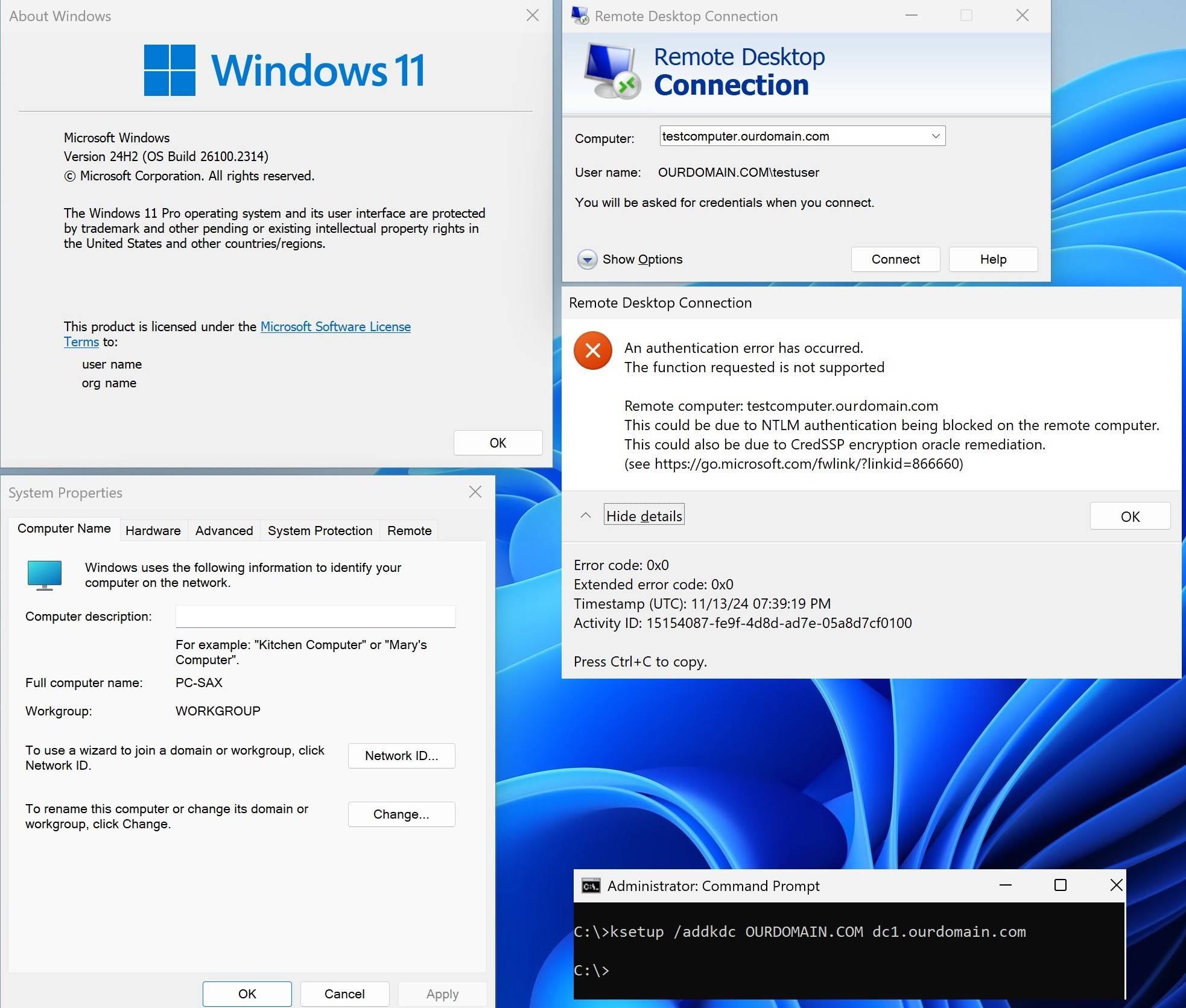
Two new "observations":
- The January 2025 Windows Update did not correct the bug.
- While I have several Windows 24H2 clients (at home), where RDP into my (business) domain-joined RDP servers IS possible, I have only one client, that cannot RDP into my domain on 24H2 (while it works fine on 23H2, as said before).
Now the new observation is, that even with the client, that has a problem to RDP into the domain, I CAN RDP to one server (Windows 10 22H2), whilst RDP fails to two other servers (Windows server 2019 & Windows 11 24H2). That means, the obvious bug in 24H2 needs an additional "condition" of the RDP server to prevent login.
Now I found that the one server, where it works, has the setting "require devices to use Network Local Authentication to connect (recommended)" DEACTIVATED, whilst the two servers, where RDP fails, have it ACTIVATED. Now it might be possible, that deactivating this setting could be a workaround until Microsoft fixes the problem. Unfortunately, I downgraded to 23H2 before testing and for some unknown reason, my computer doesn't offer an upgrade to 24H2 any more, so I can't test at the moment.