Hello @demo test
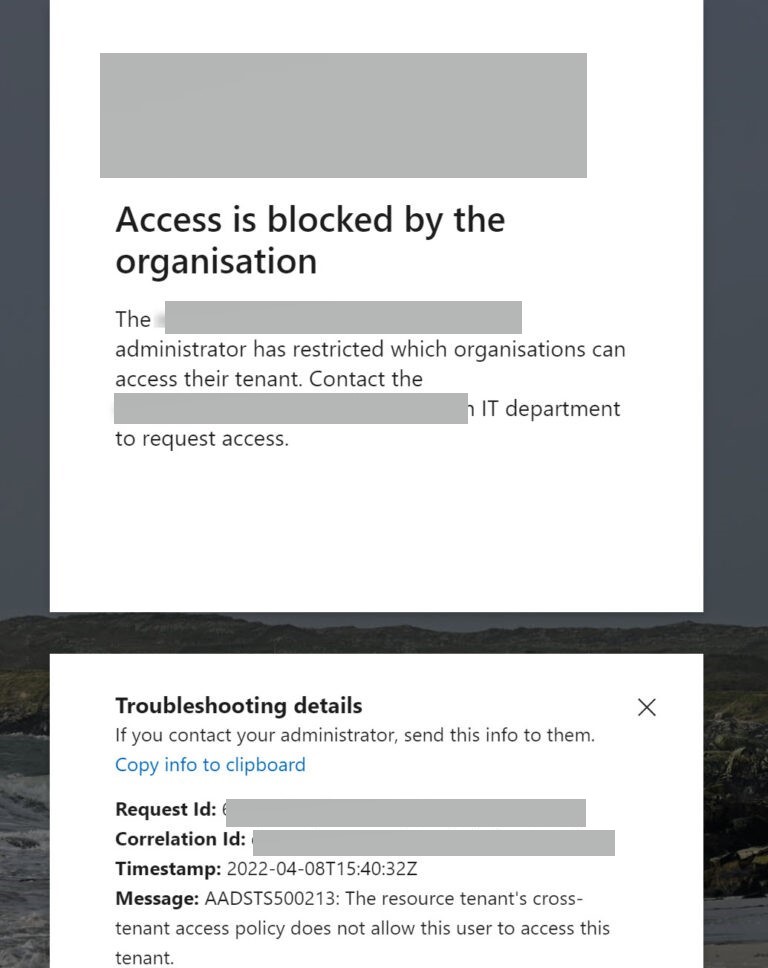
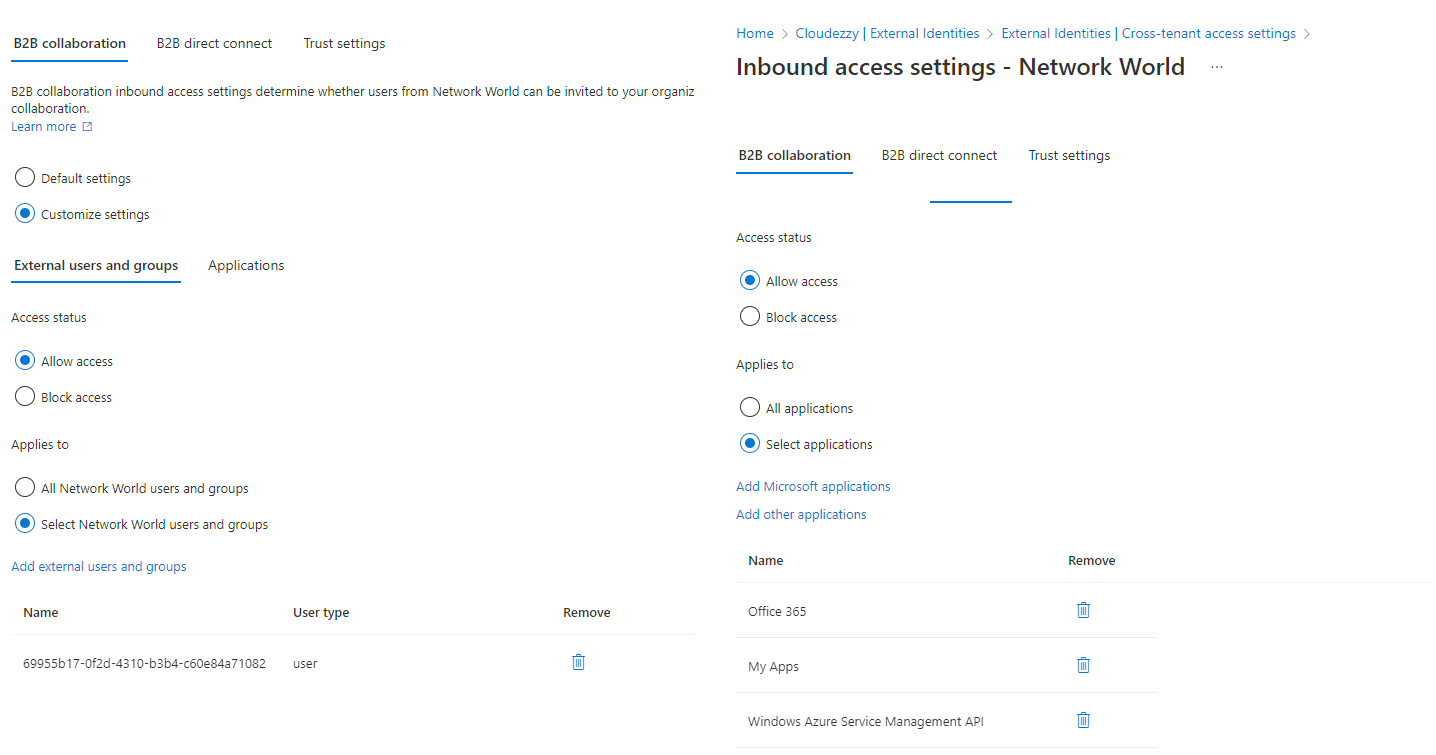
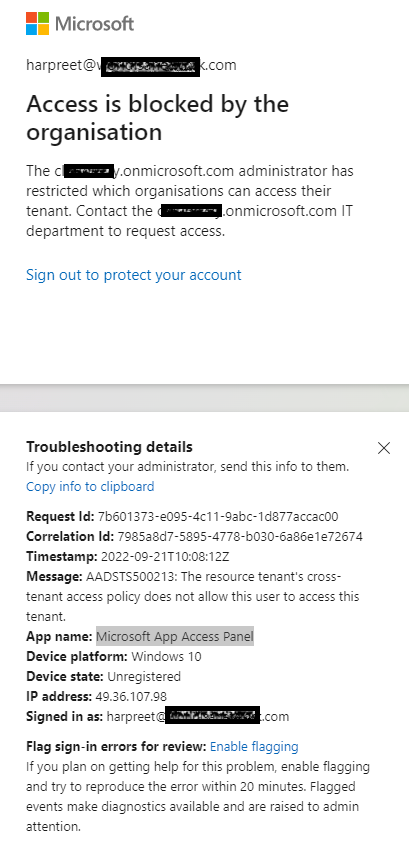
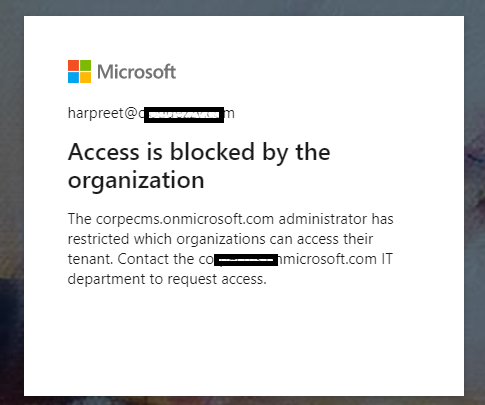
Thank you for being patient while I was testing this in my lab tenant. I have managed to reproduce the issue and can confirm that error you are facing might be due to resource tenant having a restrictive inbound setting for users and applications. I would request you to please check the Cross-Tenant access settings or B2B collaboration settings on resource tenant to validate if there are any blocks. Below is the screenshot of the error which I was able to reproduce by blocking user and application access on resource tenant.
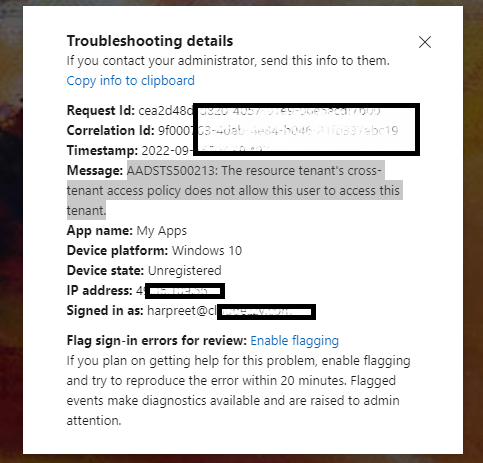
You can refer following article for more information: Manage external access with inbound and outbound settings
Additionally, in my test repro I found below details which can be helpful to you in future:
- Inbound block on resource tenant would result in error AADSTS500213: The resource tenant's cross-tenant access policy does not allow this user to access this tenant. This block occurred due to the resource tenant's cross-tenant access policy. Contact that tenant's administrator to ensure that these users are allowed access.
- Outbound block on home tenant would result in error AADSTS500212: The user's administrator has set an outbound access policy that does not allow access to the resource tenant. The user's administrator must update their cross-tenant access policy to allow access to the resource tenant.
I hope this helps you identify and fix the issue.
----------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.