Hello @K Roja
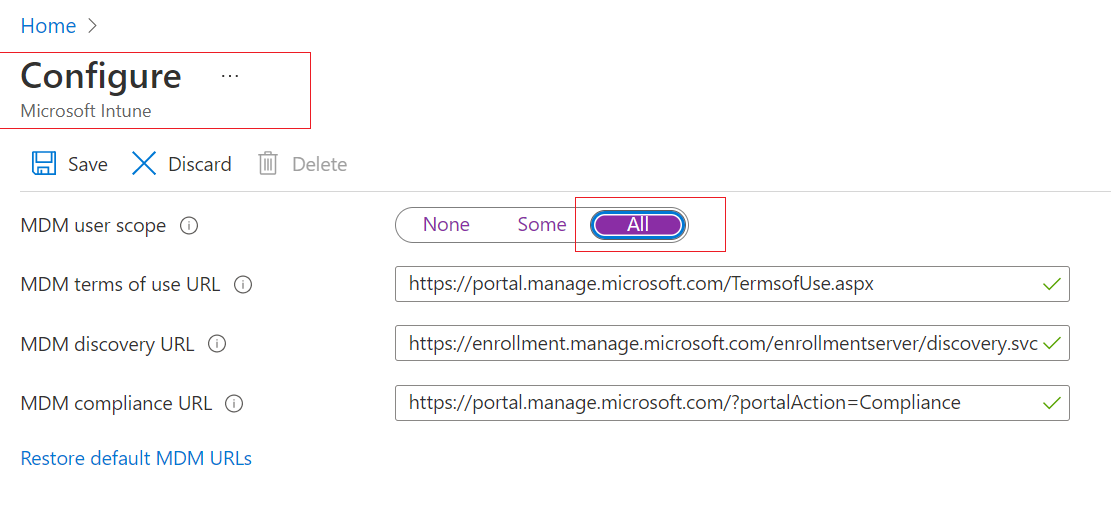
I have reviewed the request and found that as of now we do not have any PowerShell command to edit Mobility (MDM and MAM) settings available in Azure Portal.
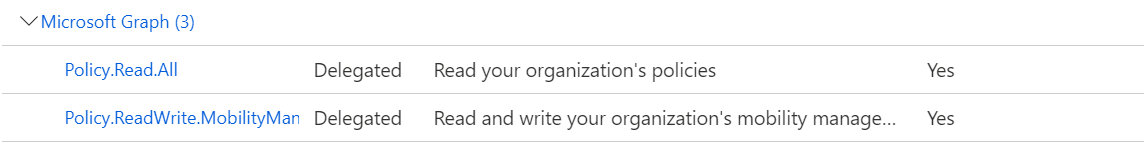
With respect to Microsoft Graph you can try below API queries to achieve this:
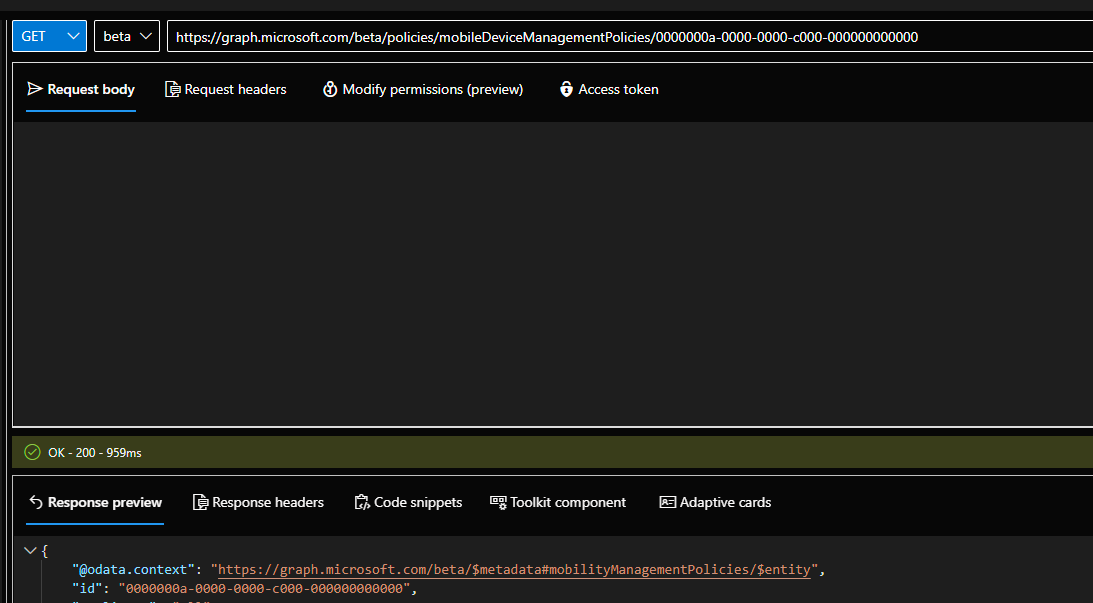
- GET https://graph.microsoft.com/beta/policies/mobileDeviceManagementPolicies/0000000a-0000-0000-c000-000000000000
- Documentation Reference: https://learn.microsoft.com/en-us/graph/api/mobiledevicemanagementpolicies-get?view=graph-rest-beta&tabs=http
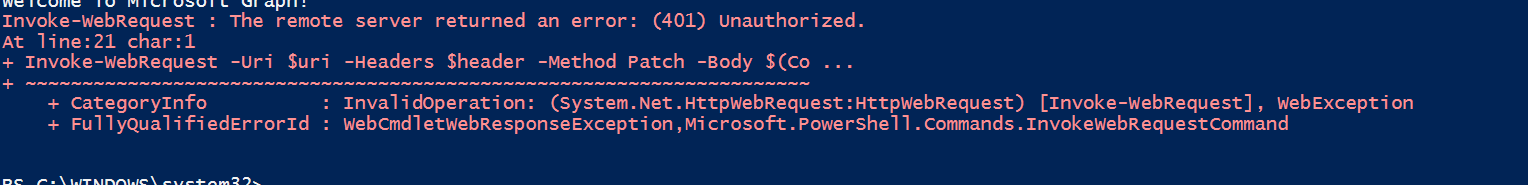
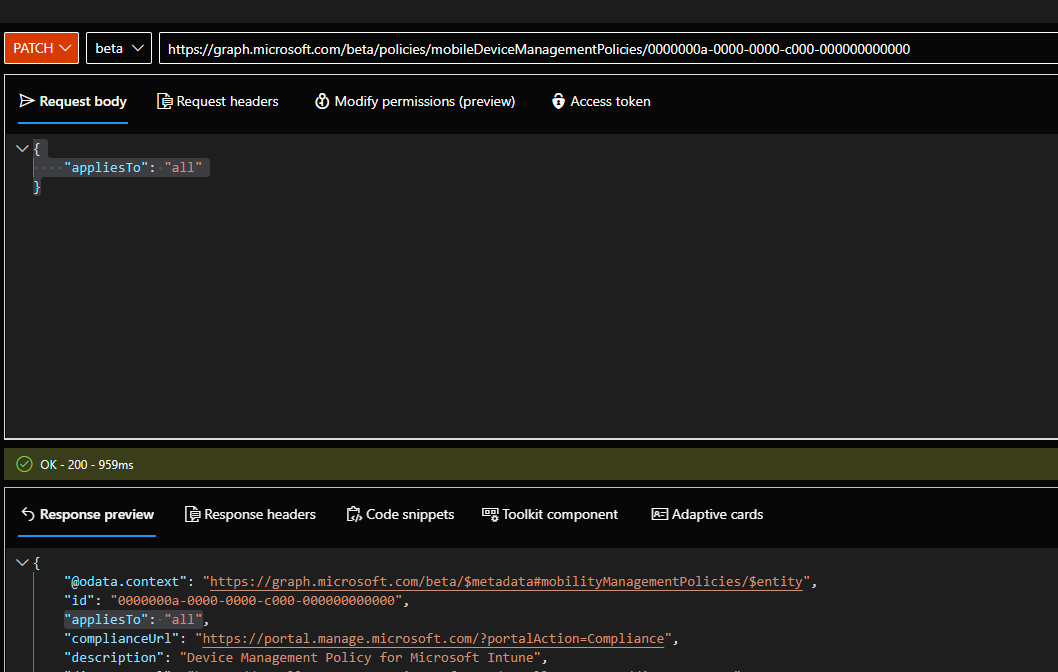
- PATCH https://graph.microsoft.com/beta/policies/mobileDeviceManagementPolicies/0000000a-0000-0000-c000-000000000000
- JSON Workload: { "appliesTo": "all" }
- Documentation Reference: https://learn.microsoft.com/en-us/graph/api/mobiledevicemanagementpolicies-update?view=graph-rest-beta&tabs=http
I hope this answers your question.
----------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.