There has been a fair amount of discussion about this, but they were for older servers (we have 2019), and the steps to check some things like ANSI Edit have changed.
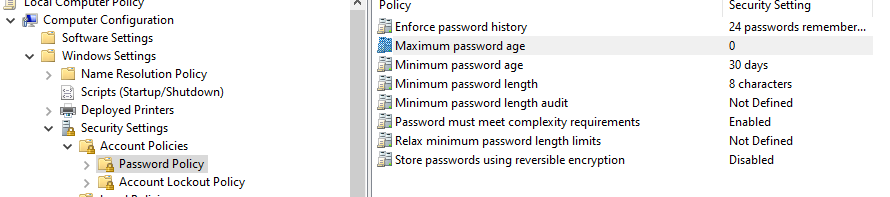
I have a GPO set up to have passwords never expire on the DC (Server 2019).
We are also using Azure AD Connect, which also has the box checked for password to never expire, though that shouldn't matter since the AD GP should override it.
I haven't tracked exactly how long it is, but our passwords still expire.
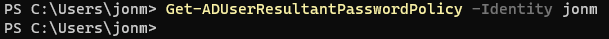
It was suggested to run Get-ADFineGrainedPasswordPolicy -Filter {Name -like "*"} | FT Name, Precedence, MaxPasswordAge, MinPasswordLength -A to see what it shows in case there is a FGPP set up, but it just says loading and then goes to a prompt, so guessing this means there isn't one.
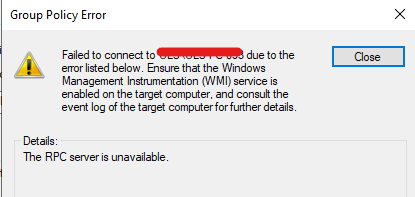
I tried looking through ANSI Edit on the DC, but couldn't find anything about passwords, so I am not sure why our systems are still being asked to reset their passwords.
Not that it matters any, but all systems are running Windows 10 Business.
This is the GP on my desktop.
If I run Get-ADUser -filter {Enabled -eq $True -and PasswordNeverExpires -eq $False} –Properties "DisplayName", "msDS-UserPasswordExpiryTimeComputed" |
Select-Object -Property "Displayname",@{Name="ExpiryDate";Expression={[datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed")}} it shows that everyone's passwords expire after 90 days.