Hello,
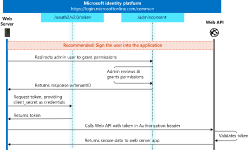
I'm currently working with another organization that is using Azure to host and secure their web applications, and we would like to integrate my web application (self-hosted, not in Azure) with their web API (hosted with Azure, behind Application Proxy). The other organization has registered an application on my behalf in their tenancy, and provided me with the client ID and client secret. We require for my server to access their server (machine to machine) with no human intervention or use of a user account (no SSO logins, no MFA, etc.). My server runs Node.JS, but so far our tests have been using Bash and cURL.
The current flow I am attempting is as follows (with identifiable details changed):
1. Request an OAuth access token using the Client Credentials Grant:
TOKEN=$(curl https://login.microsoftonline.com/${TENANT_ID}/oauth2/token \
\--header "Content-Type: application/x-www-form-urlencoded" \
\--data "grant_type=client_credentials" \
\--data "client_id=${CLIENT_ID}" \
\--data "client_secret=${CLIENT_SECRET}" \
\--data "scope=openid profile email" | jq -r .access_token)
2. Attempt to access the Azure Web App, including the access token under the Authorization header as a Bearer token:
curl https://${AZURE_APP_URL}/api/add-user \
\--header "Content-Type: application/json" \
\--header "Accept: application/json" \
\--header "Authorization: Bearer ${TOKEN}" \
\--data '{"user": "mary.sue", "email": "mary.sue@example.com"}' \
\--verbose
Step 1 is successful, however Step 2 responds with 302 Found and a redirect to the Microsoft single sign-on webpage (https://login.microsoftonline.com/${TENANT_ID}/oauth2/authorize). We haven't found a way to get past the Application Proxy. Is it possible to pass the Application Proxy using an access token? If so, what's the proper way to do it?
Thank you!