Hi @Paul Stevenson ,
Thanks for reaching out.
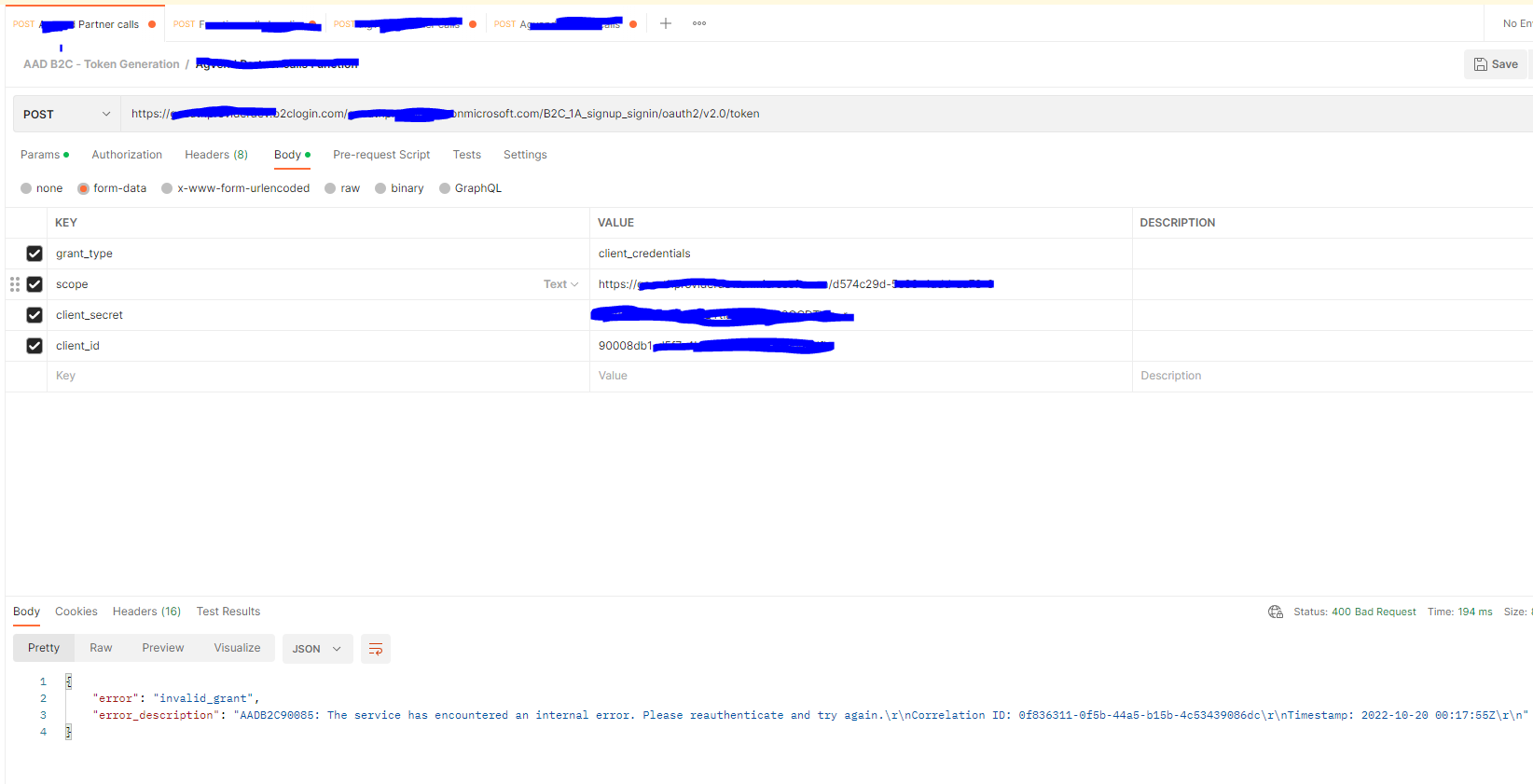
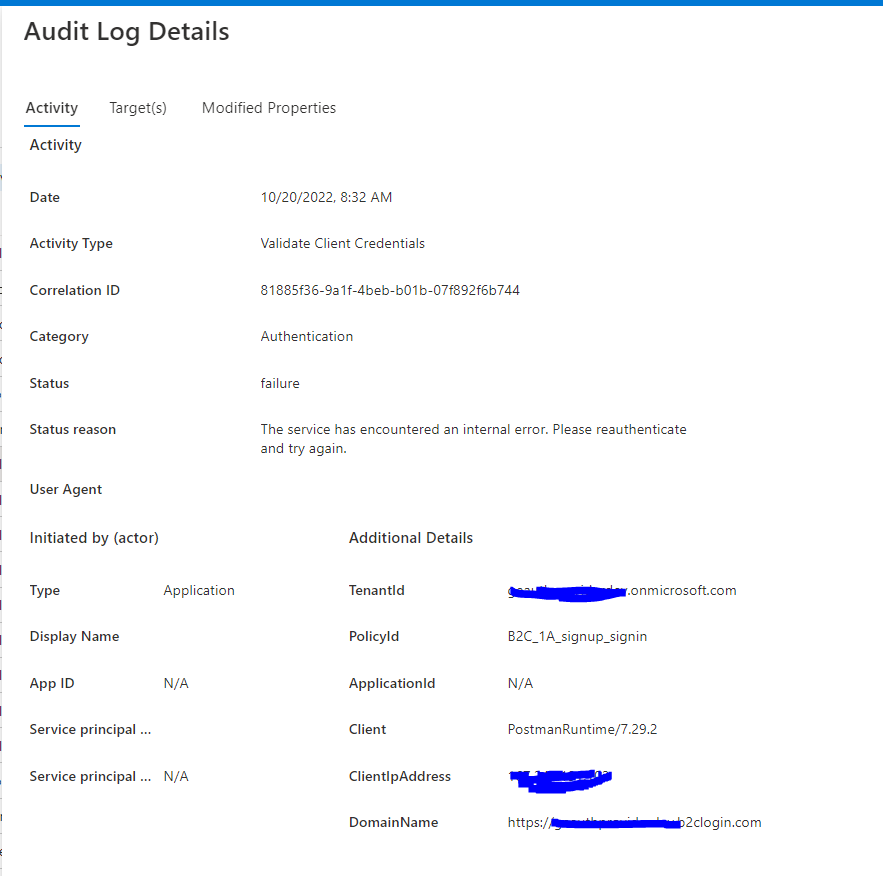
The error you are getting is due to configuration is not correct while setting up client credential flow in Azure AD B2C.
I tried to reproduce the issue and got same error due to incorrect scope.
Steps to set up client credential flow :
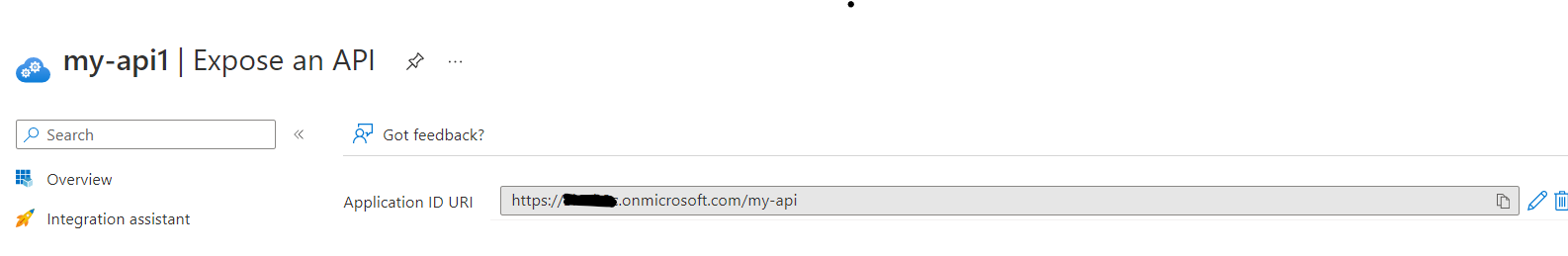
- Register App2 and expose the scopes by setting the application id URI.
2.Update manifest to define app roles
{
"allowedMemberTypes": [
"Application"
],
"description": "B2CRole",
"displayName": "B2CRole",
"id": "1fb805ae-3118-4e7c-b5e0-032c289eaf44",
"isEnabled": true,
"lang": null,
"origin": "Application",
"value": "B2CRole"
},
{
"allowedMemberTypes": [
"Application"
],
"description": "B2C",
"displayName": "B2C",
"id": "7316bf0a-f704-4bd4-9d9d-baf2d6f7719e",
"isEnabled": true,
"lang": null,
"origin": "Application",
"value": "B2C"
}],
3.Register the app1 and update the app's accessTokenAcceptedVersion is set to 2
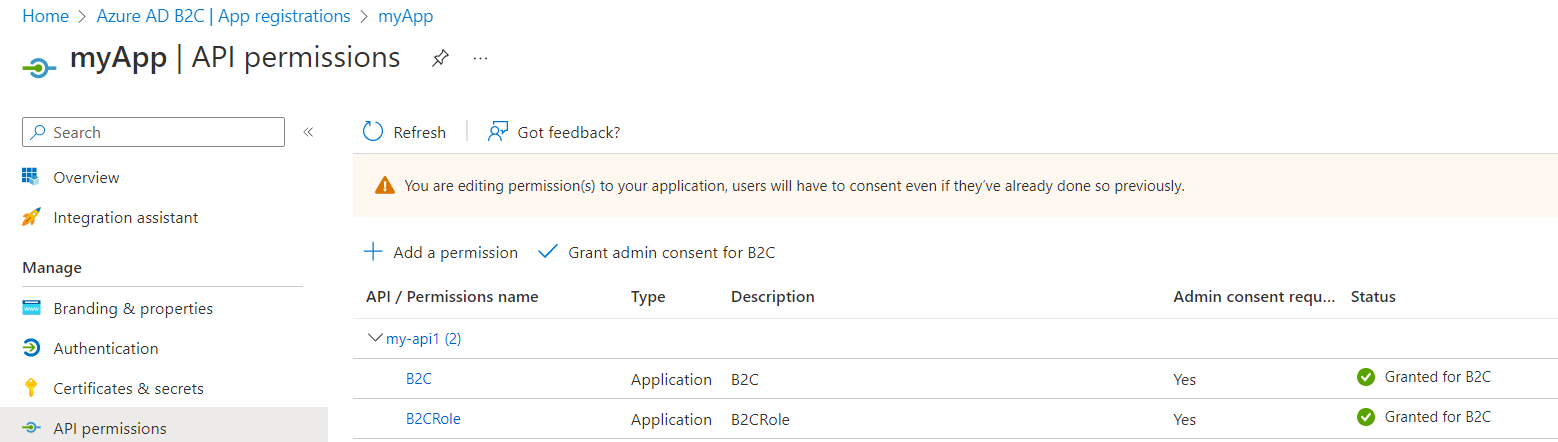
4.Grant the app(app1) permission for API(app2).
5.Request the access token . Make sure to pass correct scope. e.g https://<tenantName>.onmicrosoft.com/api/.default
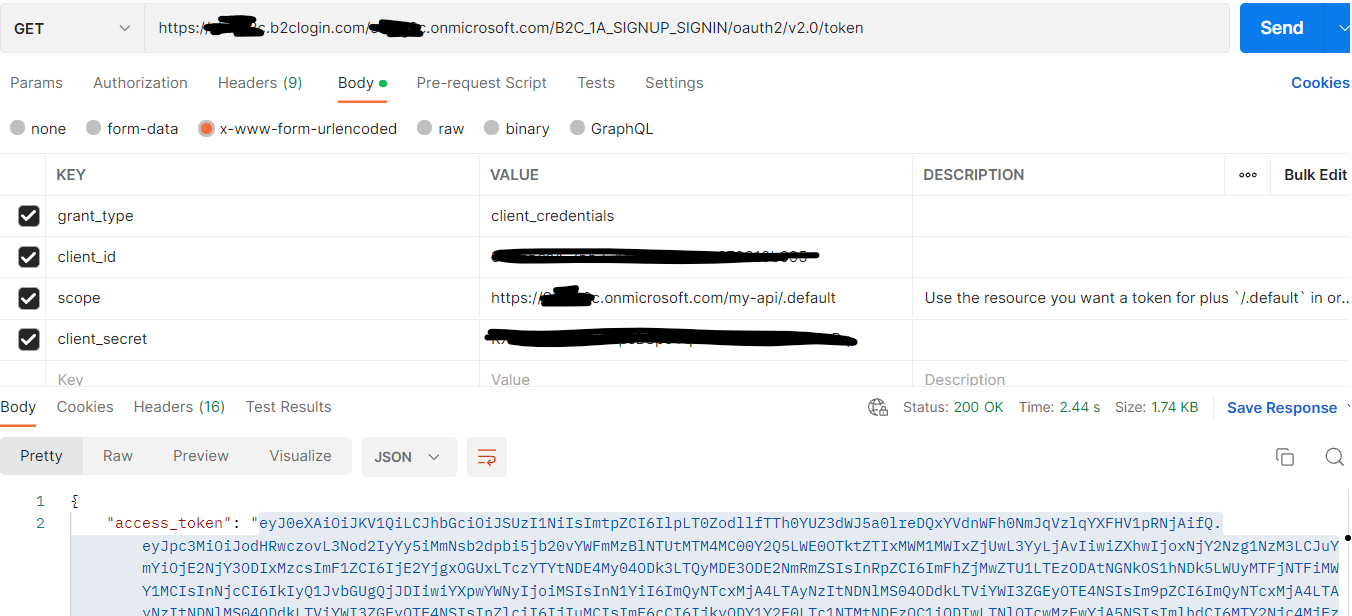
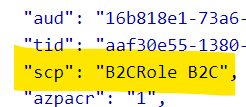
6.Decode the token using jwt.ms to see the scopes.
Hope this will help.
Thanks,
Shweta
Please remember to "Accept Answer" if answer helped you.