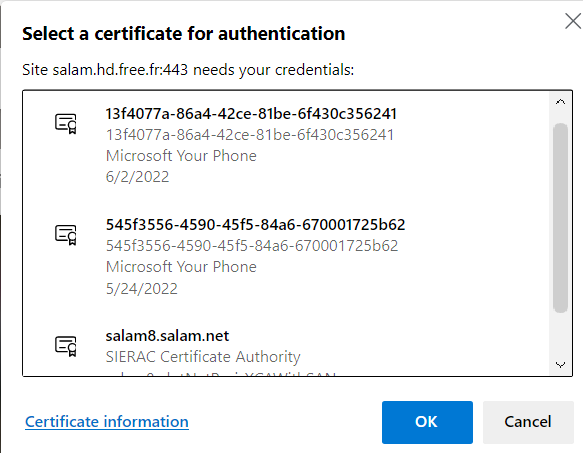
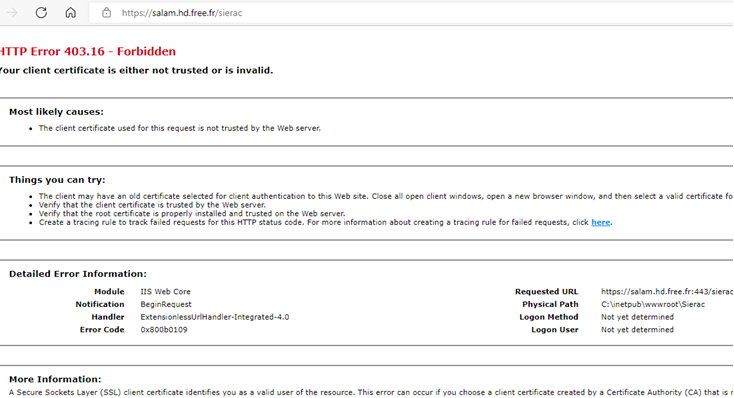
Hi @Salam ELIAS ,
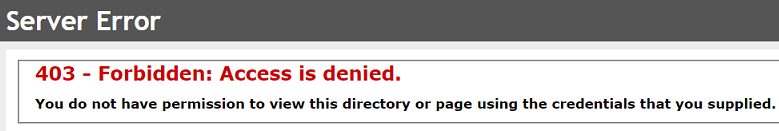
I try to check the logs and found that it is showing the 403.16 error code.
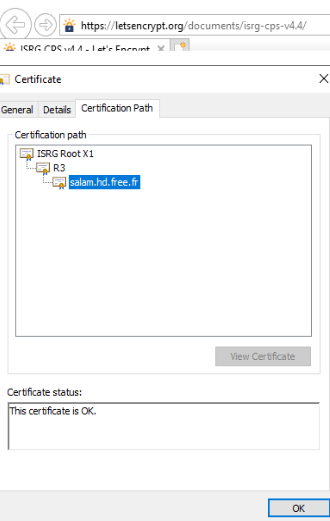
Based on my research and official docs, it looks like the issue could be related to the certificates.
Have you made any changes in certificates recently?
Below are some possible causes that could generate 403.16 error.
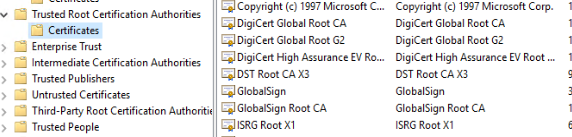
- Root certificate isn't in Trusted Root Certification Authorities Certificate store
- Non-self-signed certificates are in Trusted Root Certification Authorities Certificate store
Resolution for cause 1
- On the IIS Web server, select Start, type mmc.exe in the Start Search box, right-click mmc.exe, and then select Run as administrator.
- On the File menu, select Add/Remove Snap-in.
- Under Available snap-ins, select Certificates, and then select Add.
- Select Computer account, and then select Next.
- Select Local computer, select Finish, and then select Close.
- To exit the wizard, select OK.
- Expand Certificates, expand Trusted Root Certification Authorities, right-click Certificates, point to All Tasks, and then select Import.
- In the Certificate Import Wizard, select Next.
- In the File name box, type the location of the root certificate of the certification authority, and then select Next.
- Select Next, and then select Finish.
Resolution for cause 2
Move any non-self-signed certificated out of the Trusted Root Certification Authorities Certificate store and into the Intermediate Certification Authorities Certificate store.
For more information, please refer to HTTP Error 403.16 when you try to access a website that's hosted on IIS
Further, you could try to enable detailed errors. Select your site-> Error pages-> Edit feature settings-> Select Detailed errors and click OK. It will show you more information about this error.
Best Regards,
Deepak
----------
If the answer is the right solution, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.