Hi @Jarod Kurland ,
Thanks for reaching out.
This can be achieved using multi-tenancy. Both the applications need to register as multi-tenant application.
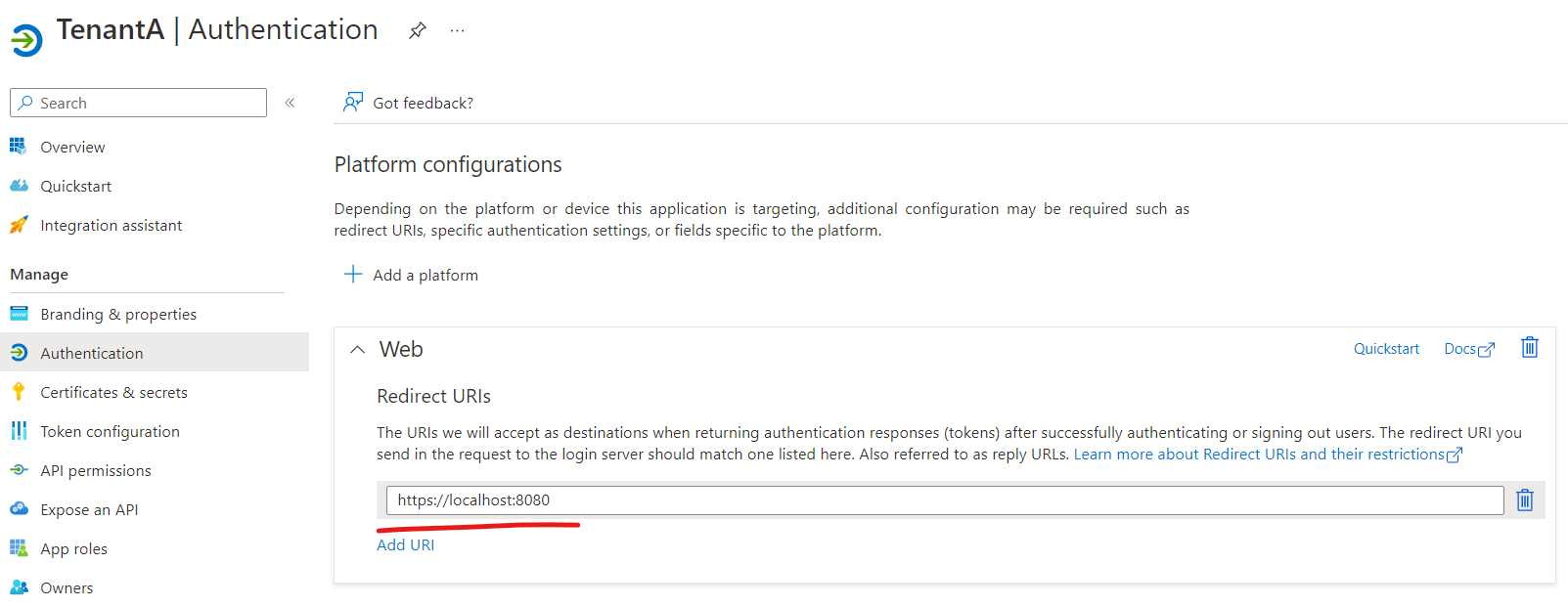
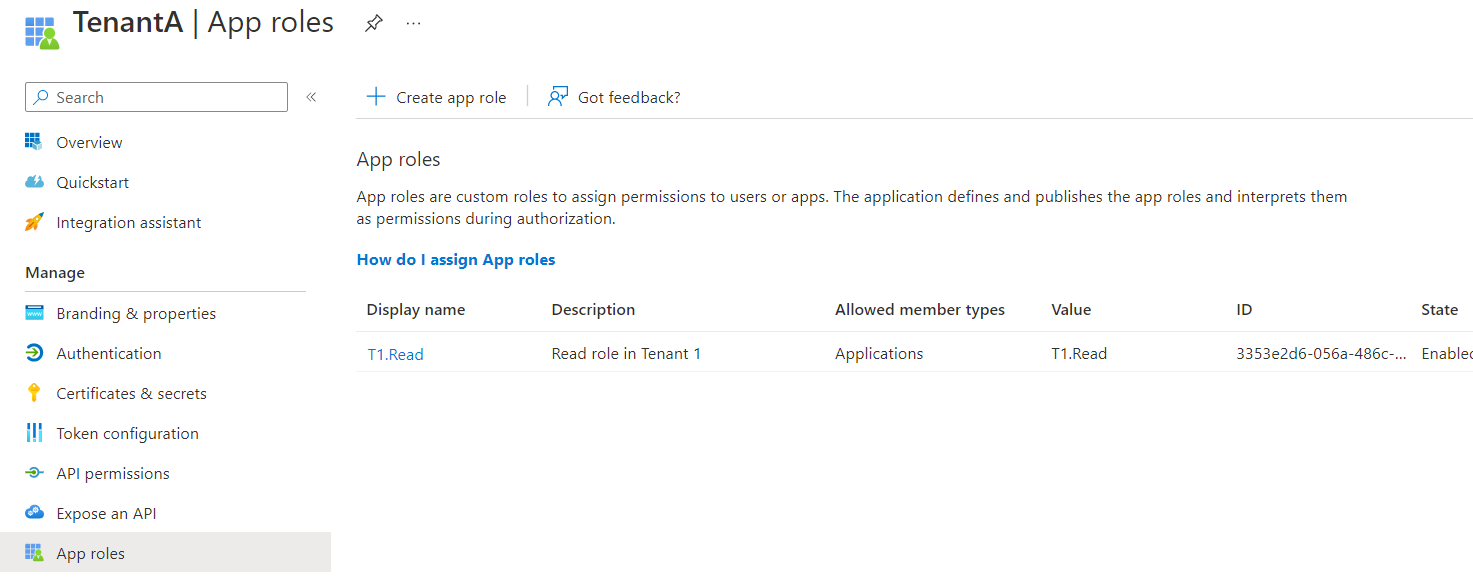
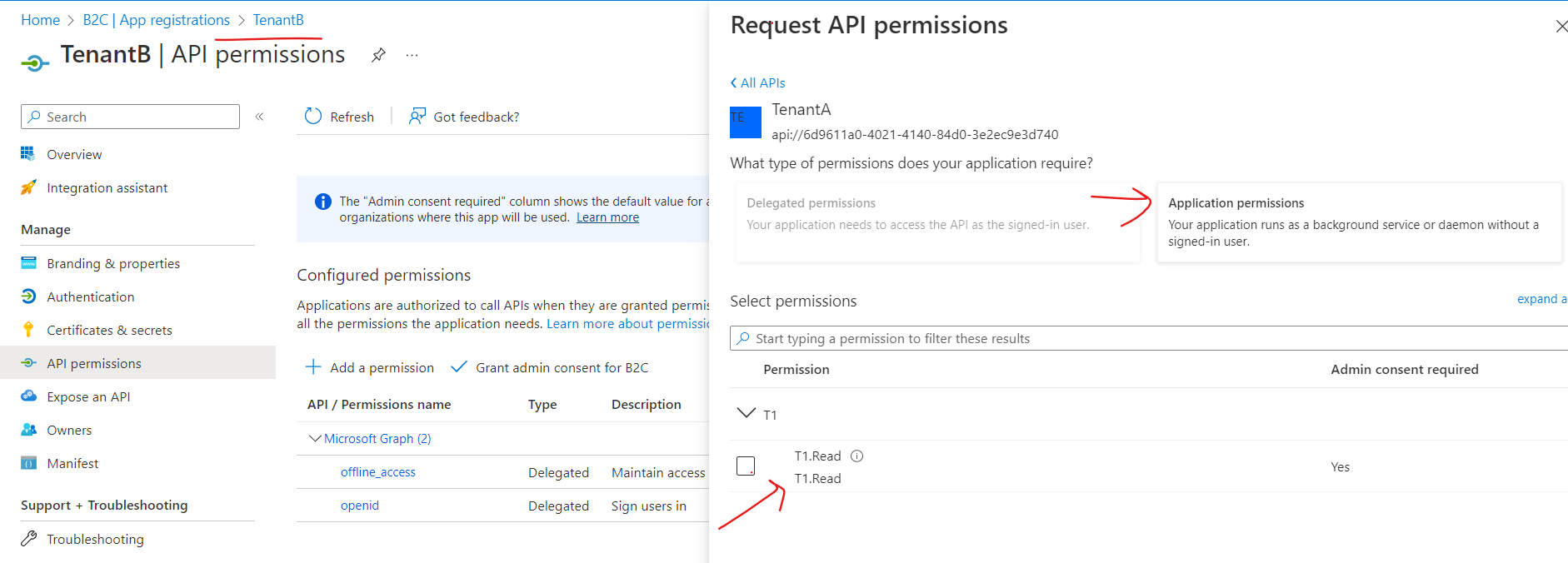
In Tenant A - Create an app registration as multi-tenant application in tenant A (eg: TenantA) and expose it as an API (api://app-id) and add the app roles in the application.
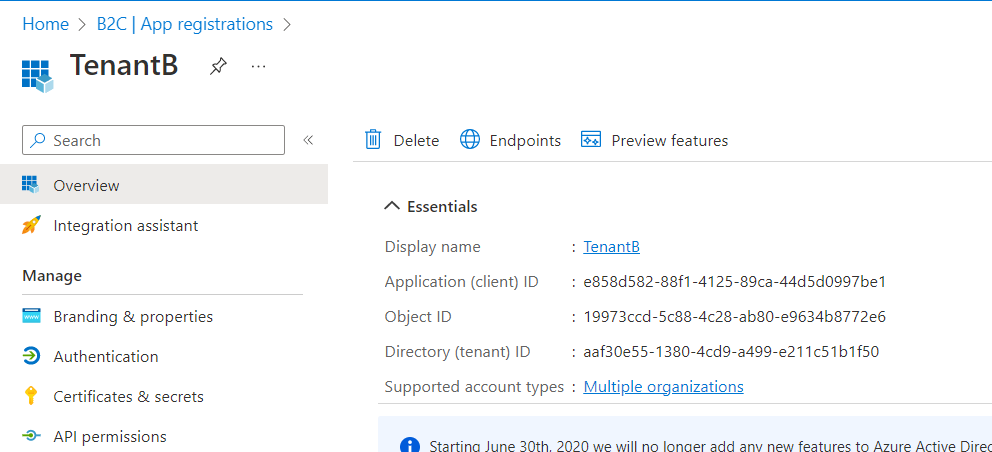
In Tenant B - Create an app registration as multi-tenant application in tenant B and note the client-id of the application.
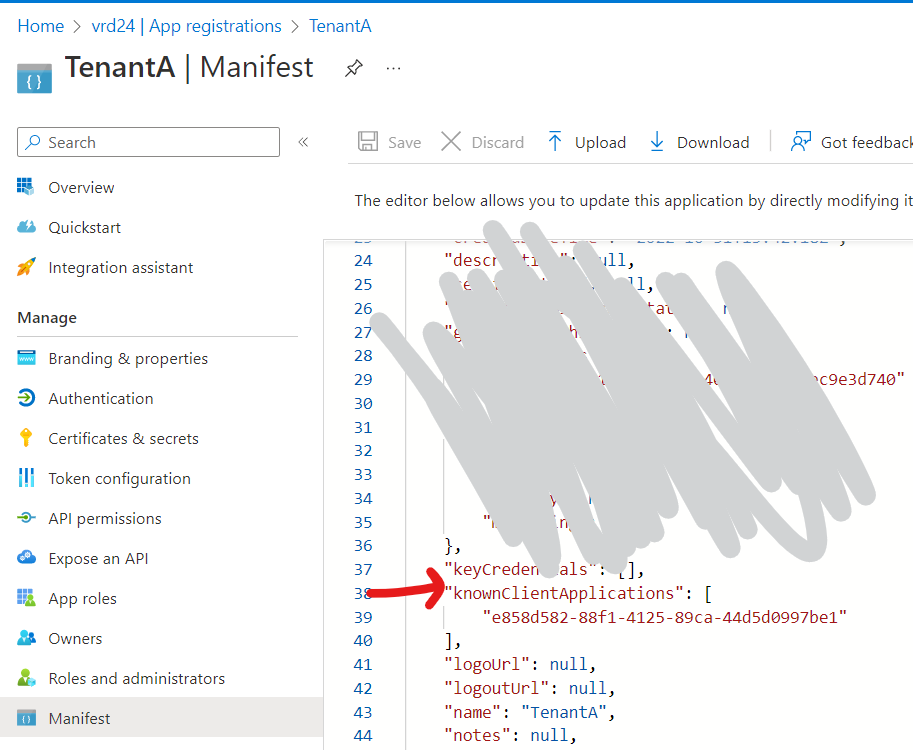
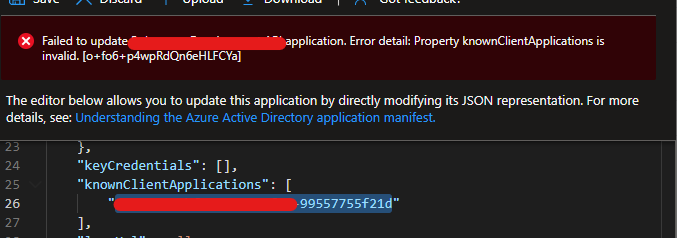
The client id of application in Tenant B need to be added in known client application in the manifest of application registered in tenant A.
and need to consent application and permission in Tenant B to create the service principal using https://login.microsoftonline.com/common/adminconsent?client_id=<clientIdOfTenantA>&redirect_uri=<redirectURIOfTenantA>
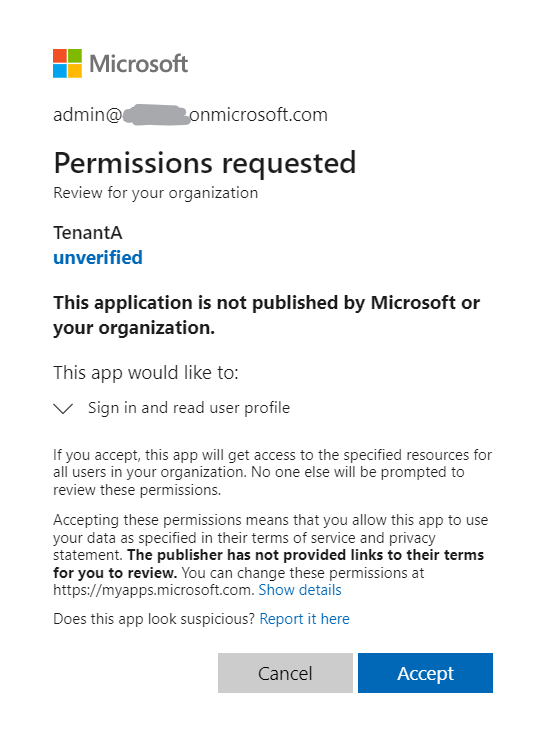
In Tenant B, service principal of Tenant A has been created under Enterprise applications as:
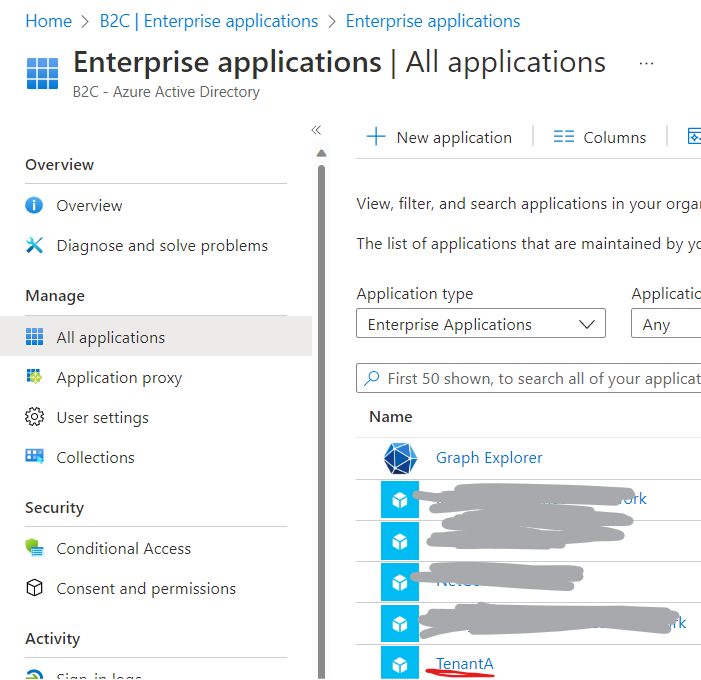
Now tenant A is available in Tenant B. You can go ahead and make the API exposed in tenant A to the tenant B.
Hope this will help.
Thanks,
Shweta
----------------------------------------
Please remember to "Accept Answer" if answer helped you.
 ]
]