Hello @Peter Harris ,
Thanks for your time and patience, I was able to view this. I did review the settings you have posted and they look inline with Extension schema. However could you please validate the following:
- Your observed certificates URLs should be of the form https://myVaultName.vault.azure.net/secrets/myCertName
- The 'authenticationSettings' property is required for VMs with any user assigned identities. Even if you want to use a system-assigned identity, this is still required; otherwise the VM extension will not know which identity to use. Without this section, a VM with user-assigned identities will result in the Key Vault extension failing and being unable to download certificates. It specifies identity to use for authentication to Key Vault.
- If you specify the 'msiClientId', then the 'msiEndpoint' property is required. Usually the value should be set to http://169.254.169.254/metadata/identity/oauth2/token
Please follow steps as per give answer to renew the cert: https://learn.microsoft.com/en-us/answers/questions/304856/event-id1001-certificateservicesclient-lifecycle-s.html
Renew a machine cert manually via MMC.
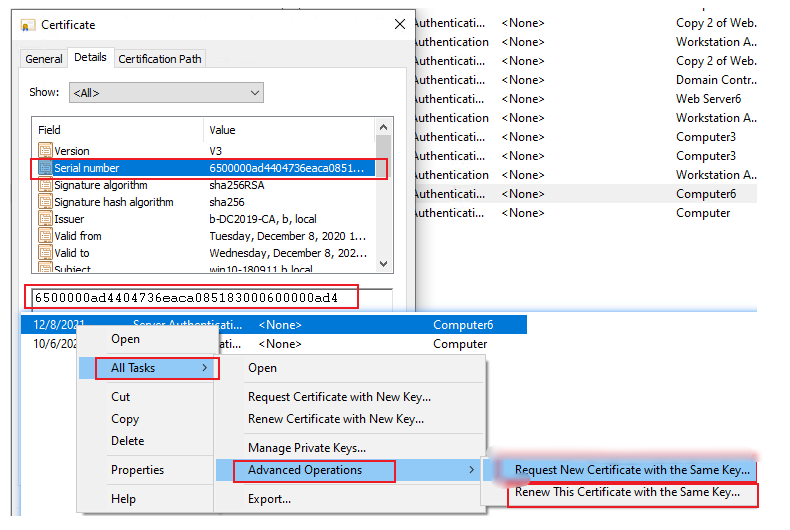
Let me know if you have any queries in the comments section.
Thanks,
Akshay Kaushik
Please "Accept the answer" and "Upvote" if the suggestion works as per your business need. This will help us and others in the community as well.
