Hello @Tobias Schmidt
Thanks for posting your query on Microsoft Q&A. As per B2C Token lifetime behavior if your application had been granted the offline_access scope. The default is 14 days. The minimum (inclusive) is one day. The maximum (inclusive) 90 days.
However Single-page applications using the authorization code flow with PKCE always have a refresh token lifetime of 24 hours while mobile apps, desktop apps, and web apps do not experience this limitation.
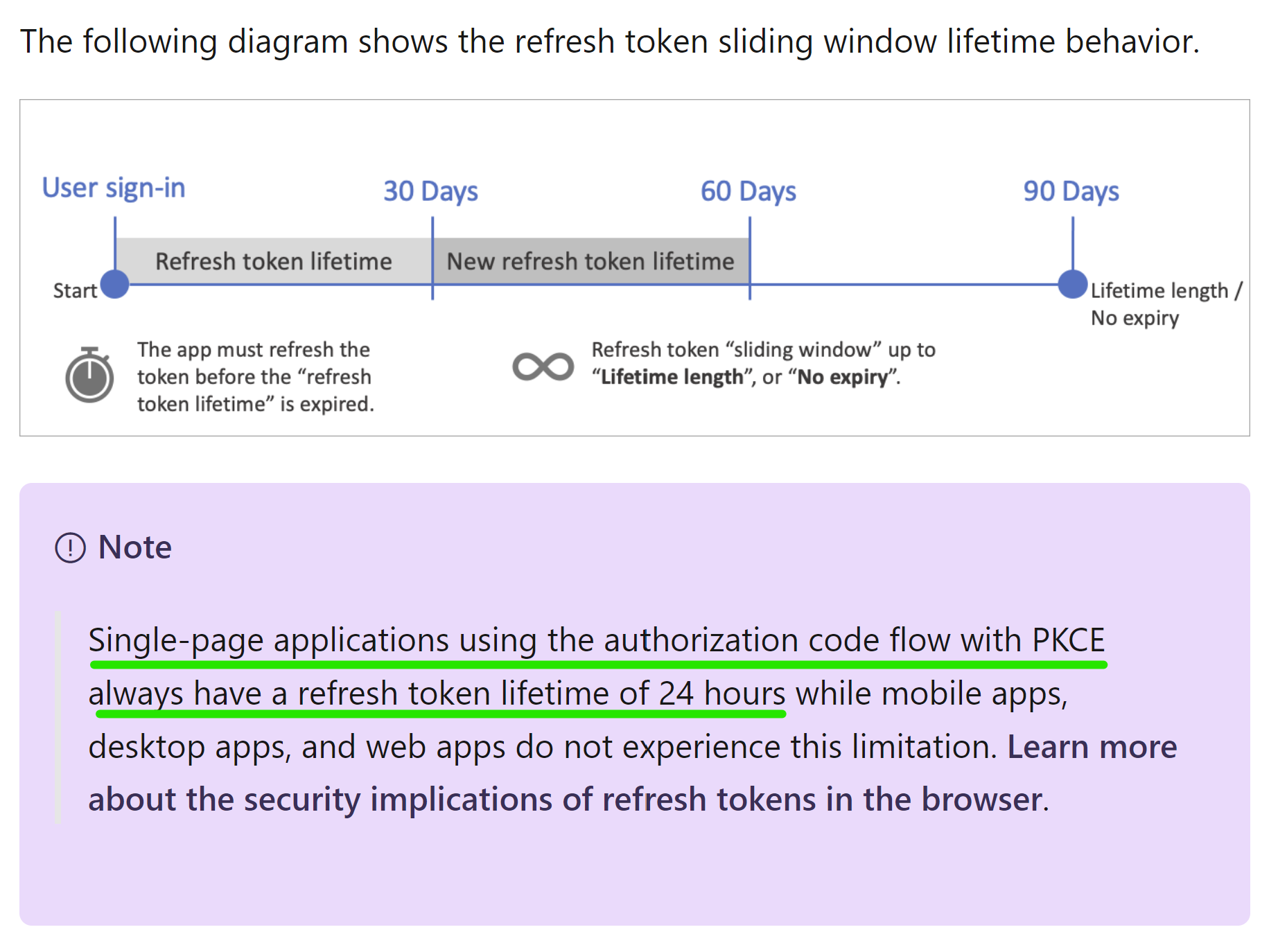
As per: https://learn.microsoft.com/en-us/azure/active-directory/develop/reference-third-party-cookies-spas#overview-of-the-solution Refresh tokens issued through the authorization code flow to spa redirect URIs have a 24-hour lifetime rather than a 90-day lifetime.
Yes, this the behavior emitted. As per https://learn.microsoft.com/en-us/azure/active-directory-b2c/tutorial-register-spa#authorization-code-flow-with-pkce :
OAuth 2.0 Authorization code flow (with PKCE) allows the application to exchange an authorization code for ID tokens to represent the authenticated user and Access tokens needed to call protected APIs. In addition, it returns Refresh tokens that provide long-term access to resources on behalf of users without requiring interaction with those users.
Please do let me know if you have any further queries in the comments section.
Thanks,
Akshay Kaushik
Please "Accept the answer" and "Upvote" if the suggestion works as per your business need. This will help us and others in the community as well
