Hello @MS Techie
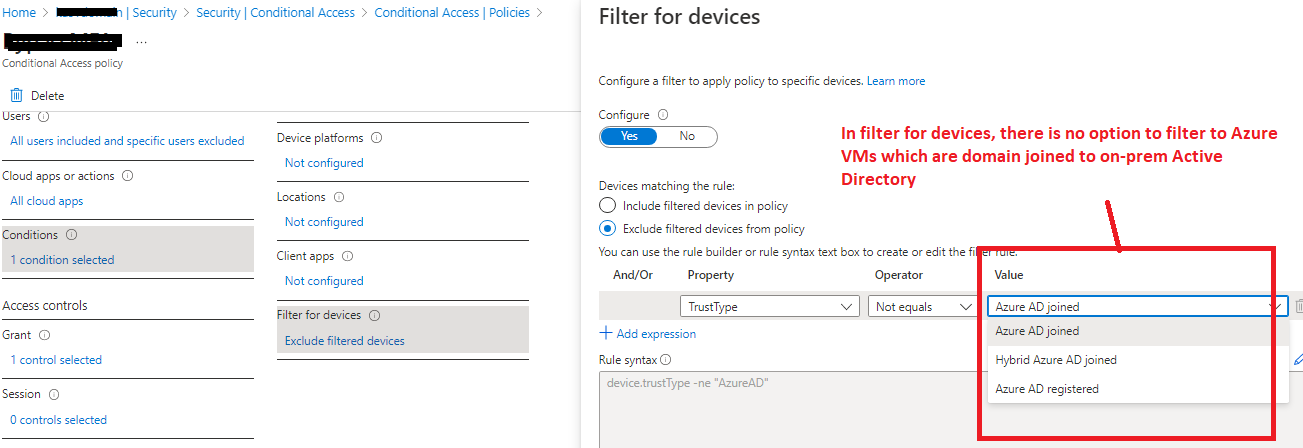
Thank you for reaching out. I would like to confirm that the filter for devices condition in Conditional Access evaluates policy based on device attributes of a registered device in Azure AD and uses device authentication to evaluate device filter rules. For a device that is unregistered or not registered with Azure AD, all device properties are considered as null values and the device attributes cannot be determined since the device does not exist in the directory.
The best way to target policies for unregistered devices is by using the negative operator since the configured filter rule would apply. If you were to use a positive operator, the filter rule would only apply when a device exists in the directory and the configured rule matches the attribute on the device. You can check out Filter for Devices documentation to get more information.
However, you need to be very careful when creating negative operator with Device TrustType Property. In your case if you create negative operator as shown in the screenshot, it will not exclude specific devices however would exclude all the devices which are not Azure AD Join from MFA. Easiest way I can think of is excluding IP's if these Azure VM's have static public IP's assigned.
I hope this helps and resolves your concern.
----------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.