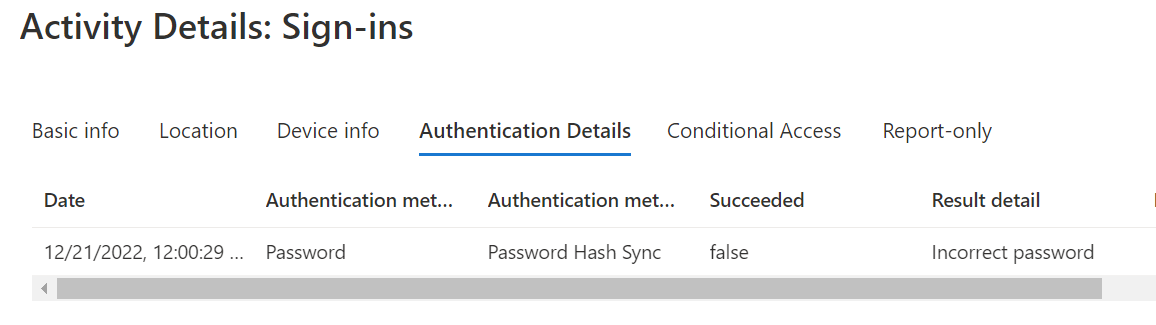
Hello @DutchIvan ,
I would suggest to use the trusted location IP address ranges. Make a policy to block access for location and exclude the trusted IP named location from the same.
This would block any request from non-trusted IP ranges.
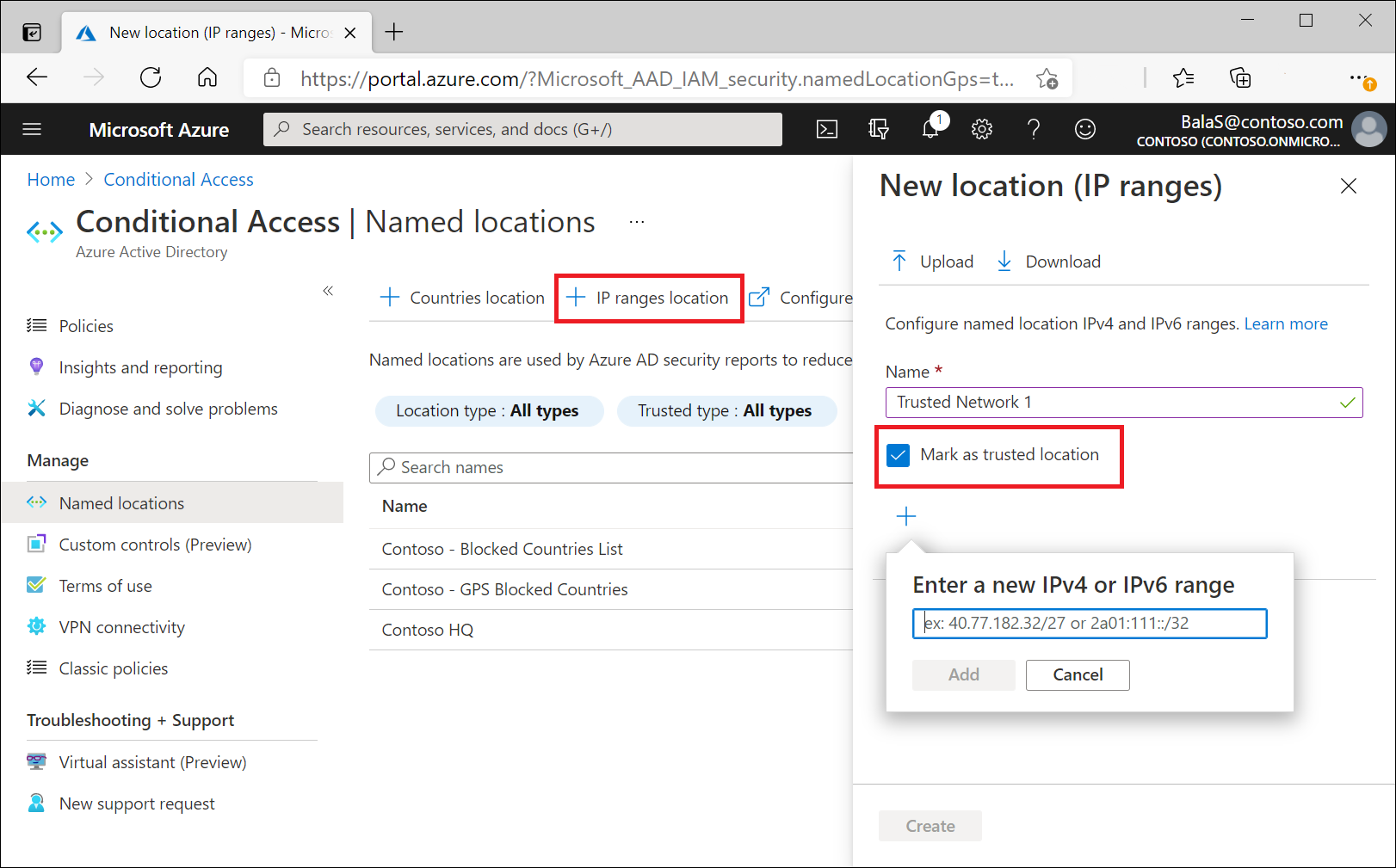
Named locations defined by IPv4/IPv6 address ranges are subject to the following limitations:
- Configure up to 195 named locations
- Configure up to 2000 IP ranges per named location
- Both IPv4 and IPv6 ranges are supported
- Private IP ranges can't be configured
- The number of IP addresses contained in a range is limited. Only CIDR masks greater than /8 are allowed when defining an IP range.
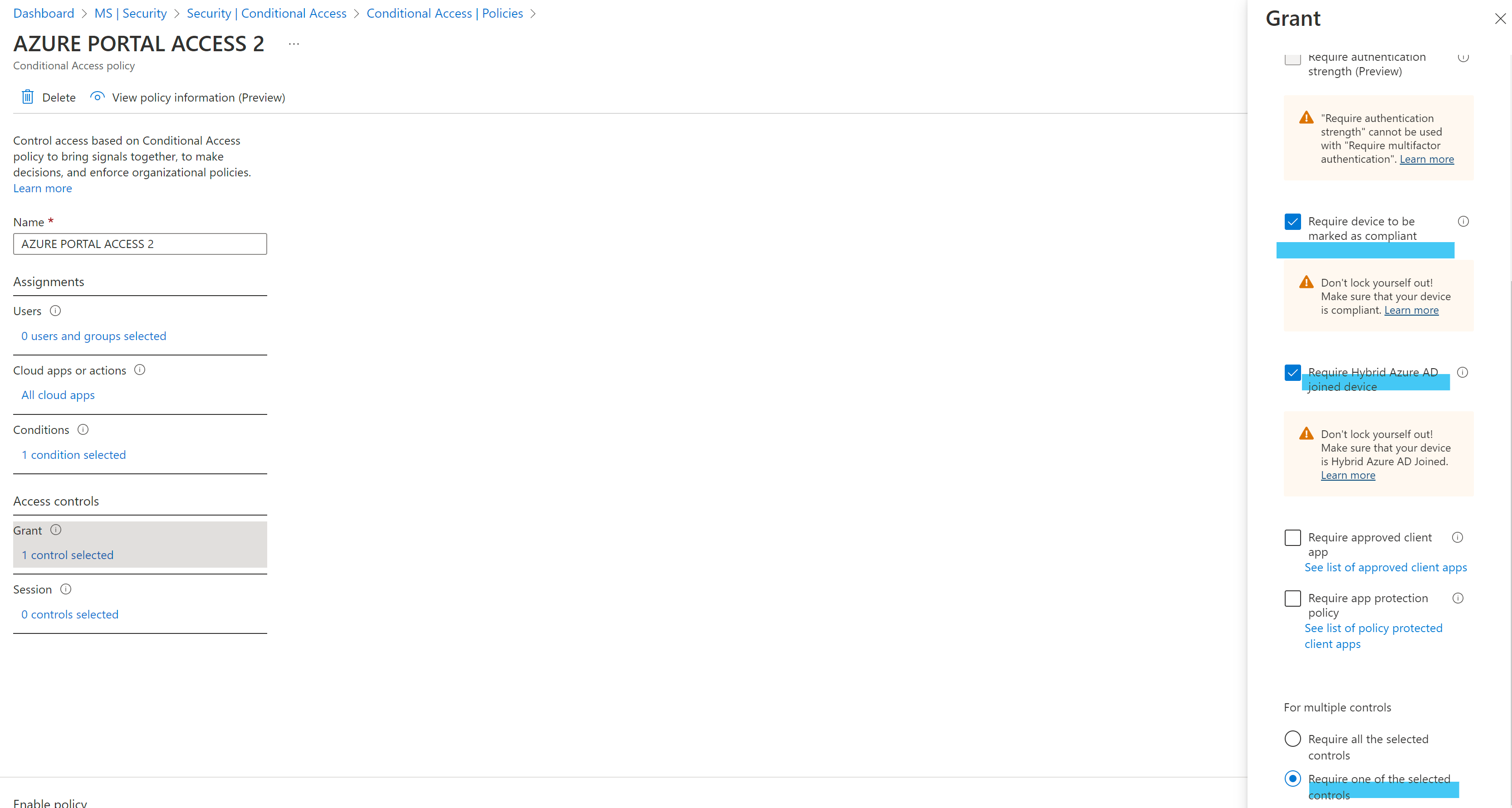
Apart from this if the devices are hybrid AD joined you could use Require Hybrid Azure AD joined device and for mobile devices you could use Require device to be marked as compliant if you are using MEM( Intune). This would immediately block access from devices not meeting the criteria.
Please do let me know if you have any queries in the comments section.
Thanks,
Akshay Kaushik
Please "Accept the answer", "Upvote" and rate your experience if the suggestion works as per your business need. This will help us and others in the community as well.