Hello Christoph,
There are 4 types of ETW providers: MOF, Manifest/Crimson, WPP and TraceLogging. "IKEEXT Trace Provider" is a WPP provider (which is the most difficult type of event to interpret if the TMF information is not published/available). {e7ba355a-ec20-5993-dd3b-9215e4d8a23c} is the GUID of a TraceLogging provider added in Windows 11 (Microsoft.Windows.Networking.Ikeext) that delivers essentially the same information as "IKEEXT Trace Provider" but in an easier to interpret format.
I use tools that I developed myself to inspect the trace data; previously I recommended Microsoft Message Analyzer as the best publicly available tool to use, but this tool has now been decommissioned.
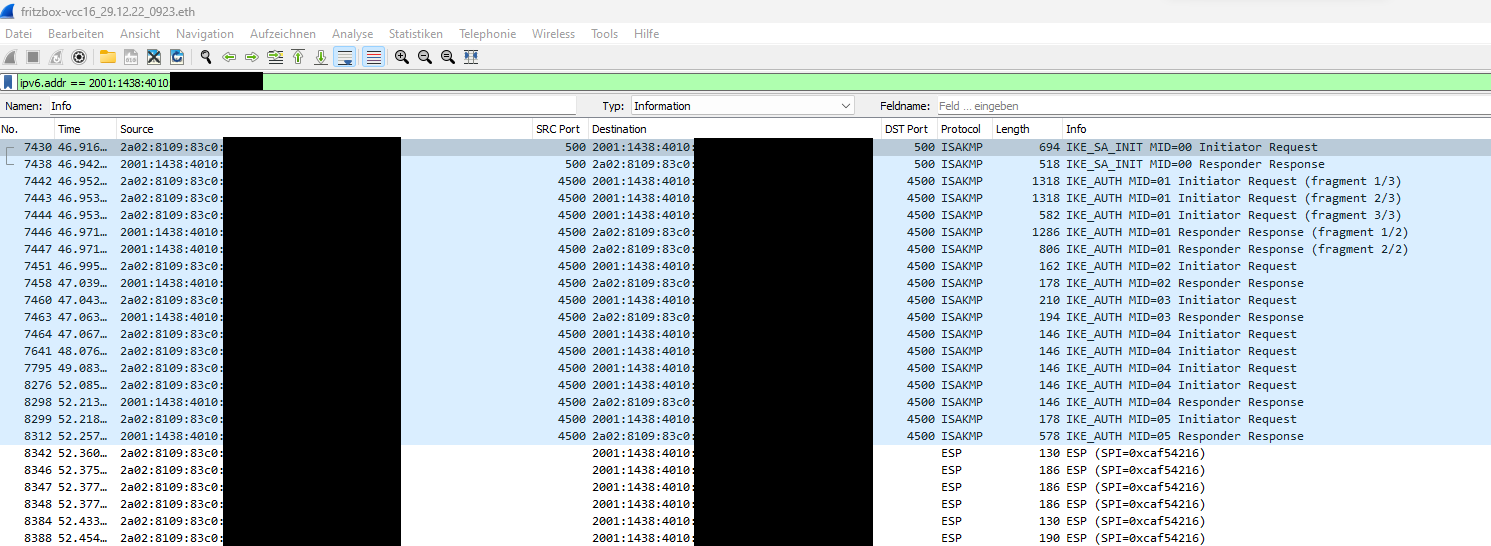
The "not working" trace shows that the initial IKEv2 packet is being transmitted and retransmitted, but no response is received:
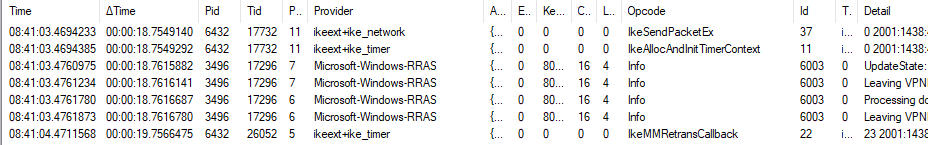

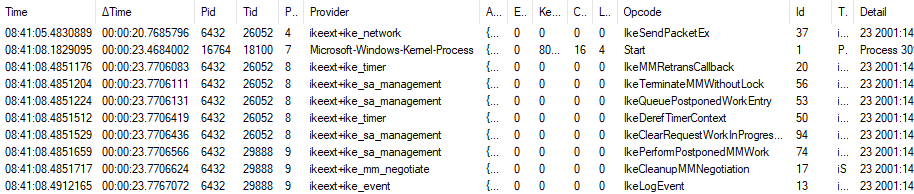
So the client appears to be working perfectly well; somewhere along the route between client and server either the initial request or the initial response is being lost (possibly due to NAT). You mentioned in your first message that you were able to make a capture on the "source network" (home network?) router? Can you share any more information about that (e.g. router type, tool used for capture) and are you sure that there was no trace of traffic using UDP port 500?
Gary