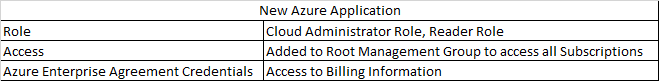
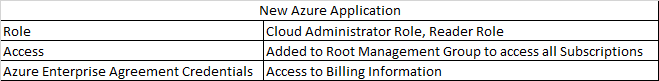
Thanks for reaching out.
There are three types of service accounts in Azure Active Directory.
a. Managed Identities
b. Service Principals
c. and User Based Service accounts.
These are those accounts that represent application, API or other service.
To create a service account in Azure Active Directory, you can follow these steps:
- Sign in to the Azure portal using your Azure account.
- In the left-hand menu, click on "Azure Active Directory".
- In the Azure Active Directory page, click on "App registrations" in the menu on the left.
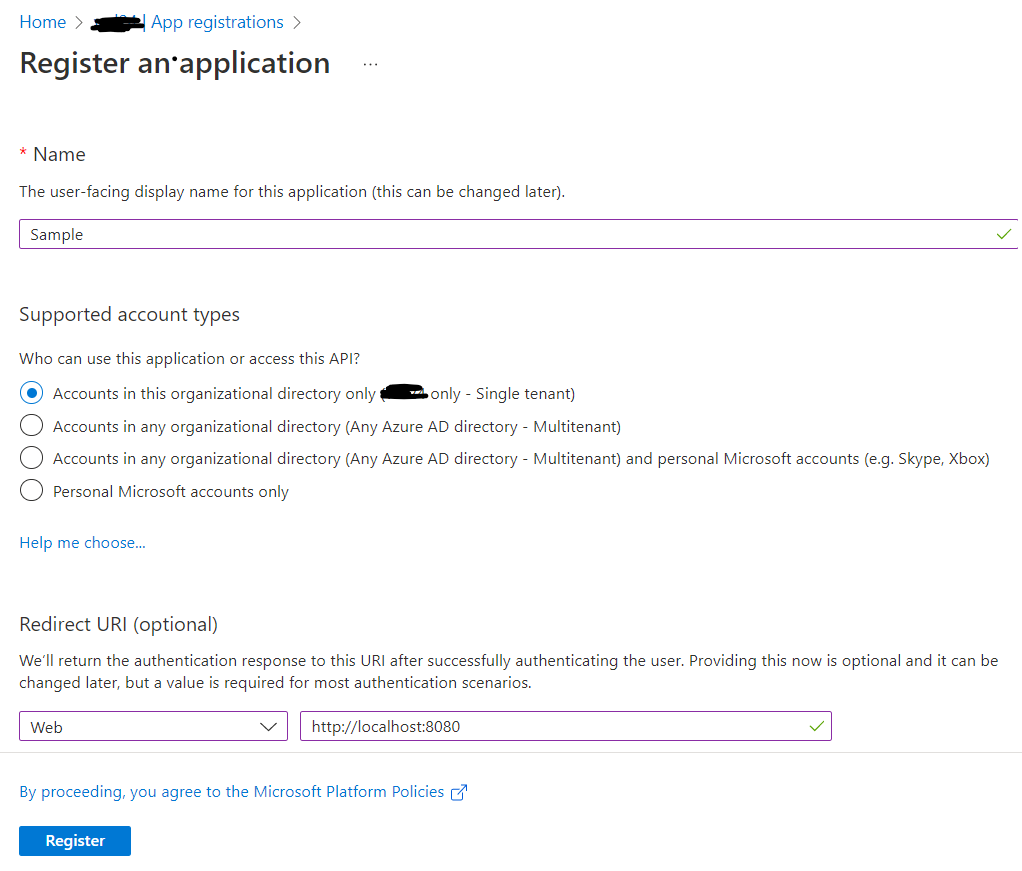
- Click on the "New registration" button.
- Enter a name for the service account in the "Name" field.
- In the "Supported account types" section, select "Accounts in this organizational directory only" or select the appropriate options for your service account.
- Click on the "Register" button.
You can then use this service account or service principal to authenticate to Azure resources and perform operations on behalf of your organization. As you create these service accounts for automated use, they're granted permissions to access resources in Azure and Azure AD.
Grant the service account only the permissions necessary to perform its tasks i.e User.Read by selecting app permissions in your registered application.
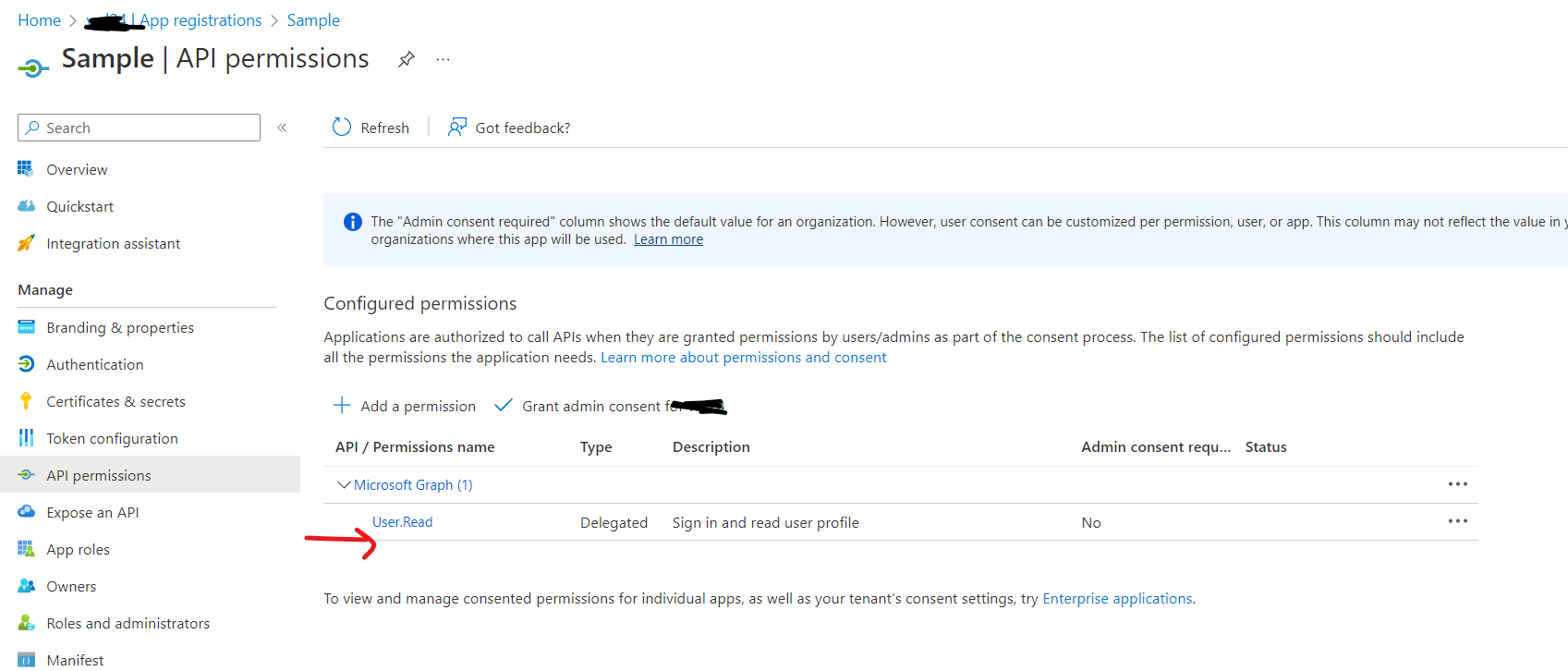
User.Read is by default added permission to your registered application.
Hope this will help.
Thanks,
Shweta
Please remember to "Accept Answer" if answer helped you.