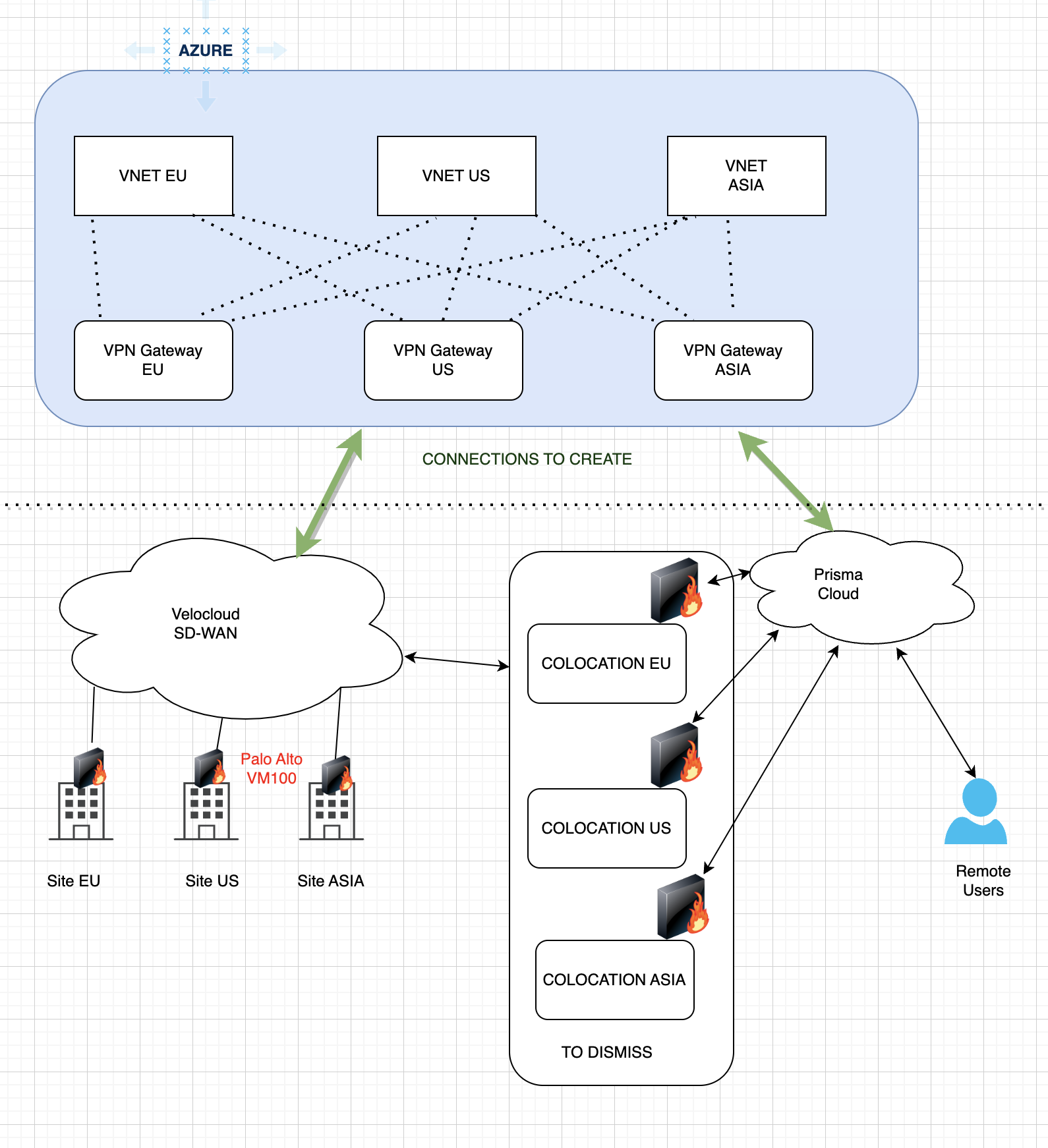
I would go, with Azure Virtual WAN, link the VNETs up to the WAN and an Azure Point to Site connection for remote clients. Using the Azure Virtual WAN will help with keeping the network traffic within the Azure backbone.
The branch office sites can just use an S2S connection to the WAN.
Additional Links:
https://learn.microsoft.com/en-us/azure/virtual-wan/virtual-wan-about
https://learn.microsoft.com/en-us/azure/virtual-wan/how-to-virtual-hub-routing
https://learn.microsoft.com/en-us/azure/virtual-wan/migrate-from-hub-spoke-topology
If you do need an NVA - https://learn.microsoft.com/en-us/azure/virtual-wan/how-to-nva-hub
https://github.com/adstuart/azure-vwan-anycast
https://github.com/adstuart/azure-crossregion-private-lb
https://github.com/dmauser/azure-virtualwan/tree/main/inter-region-azfw