@Jain, Shamu
Thank you for your post!
From your initial post and follow-up, I understand that you're preparing a dashboard showing total events and total notable events from Microsoft Sentinel. While getting the total number of events is simple, you're running into issues with getting the number of notable events - for example, events that generate an alert such as twenty 4625 events for one user generating a Brute force alert.
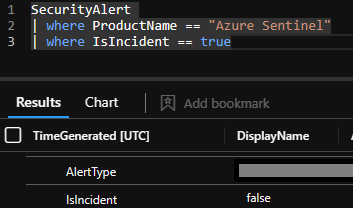
Since you're looking for notable events across all of your alerts, have you tried to look within the SecurityAlert table and filtering by technique or IsIncident? This should show all your Sentinel Alerts where an Incident was created.
SecurityAlert
| where ProductName == "Azure Sentinel"
| where IsIncident == true
Note: My Sentinel environment doesn't have sufficient data when it came to testing for "IsIncident = true"
I hope this helps!
Additional Links:
If you're still having issues or would like to work with our support team on this, please let me know.


