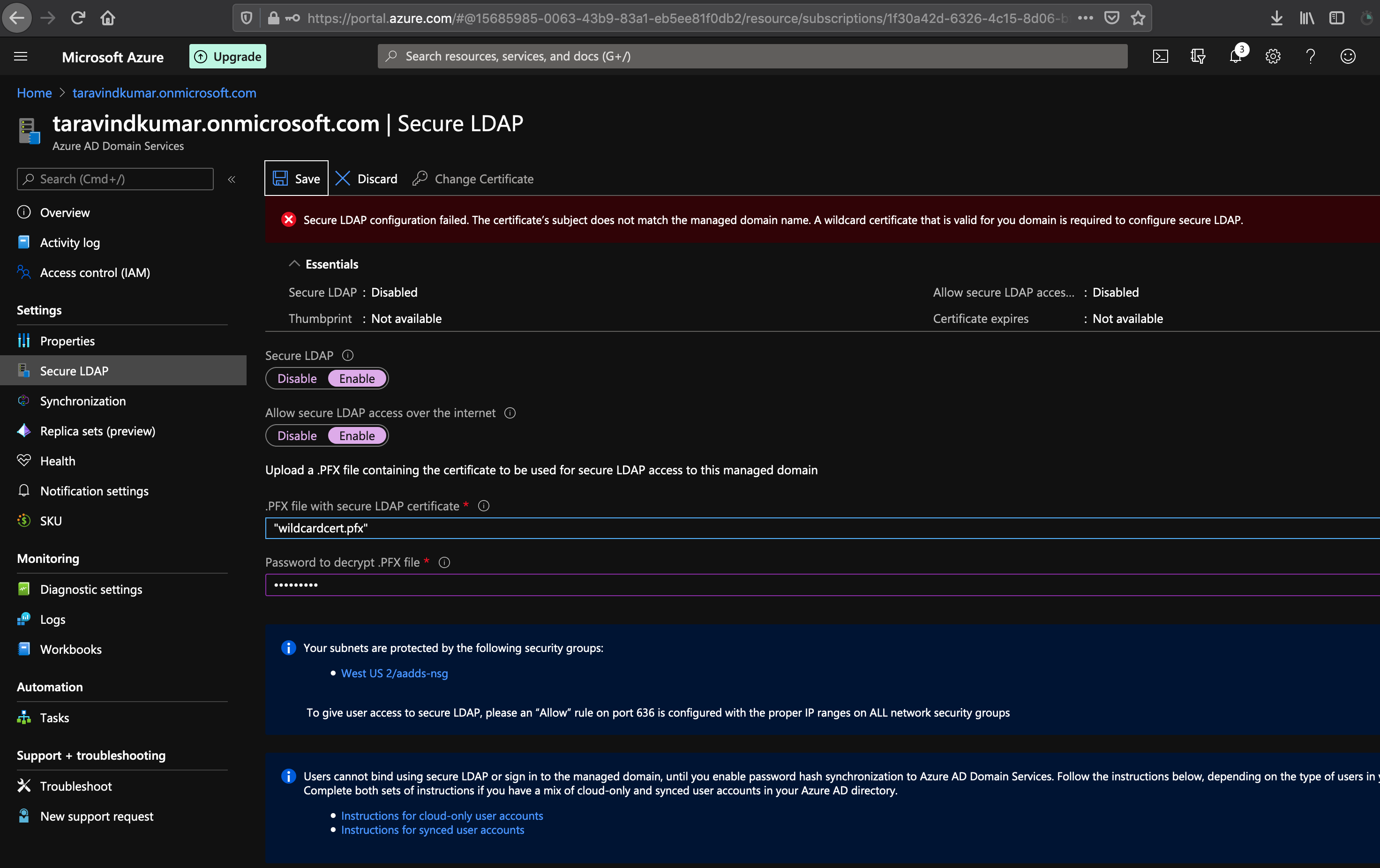
Ensure that you have checked the requirements for the secure LDAPs certificate:
Trusted issuer - The certificate must be issued by an authority trusted by computers that need to connect to the domain using secure LDAP. This may be your organization's enterprise certification authority or a public certification authority trusted by these computers.
Lifetime - The certificate must be valid for at least the next 3-6 months. This ensures that secure LDAP access to your managed domain is not broken when the certificate expires.
Subject name - The subject name on the certificate must be a wildcard for your managed domain. For instance, if your domain is named 'contoso100.com', the certificate's subject name must be '*.contoso100.com'. The DNS name (subject alternate name) must also be set to this wildcard name.
Key usage - The certificate must be configured for the following uses - Digital signatures and key encipherment.
Certificate purpose - The certificate must be valid for SSL server authentication.
It will take about 10 to 15 minutes to enable secure LDAP for your managed domain. If the provided secure LDAP certificate does not match the required criteria (eg. the domain name is incorrect, the certificate is expired or expires very soon etc.), secure LDAP will not be enabled for your directory and you will see a failure.
Also, make sure you have selected a Forest Type of Trust.