Hello,
I wanted to block specific remote assist applications (such as TeamViewer, AnyDesk) through Intune Portal. So I've created a app locker policy and implemented through that.
This is what I've done:-
On my laptop, opened up Local Group Policy Editor
Went to Computer Configuration --> Windows Settings --> Security Policy --> Application Control Policies. Under AppLocker,
Clicked on Configure Rule Enforcement --> Enabled Executable Rules.
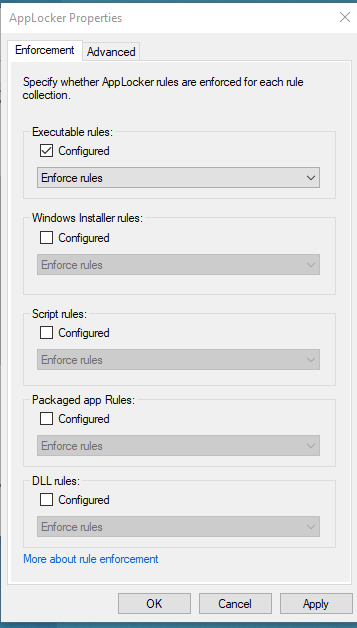
Created default rules and created a new rule to Deny the applications: AnyDesk and TeamViewer
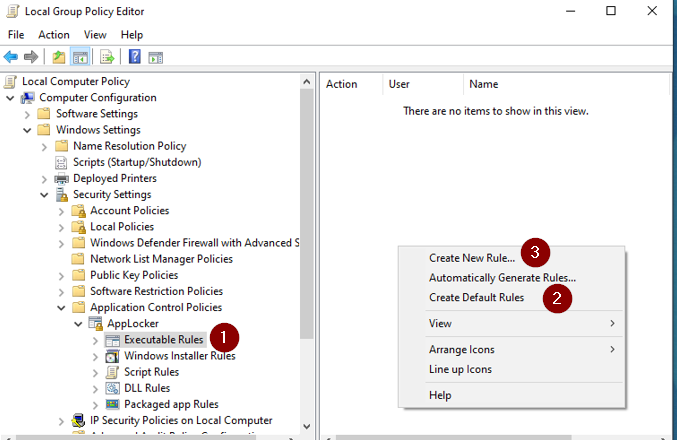
Clicked on Next
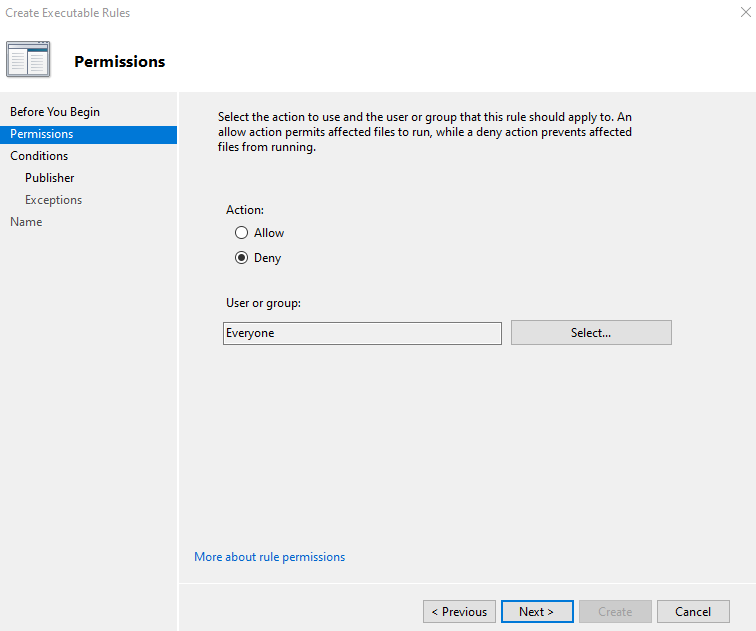
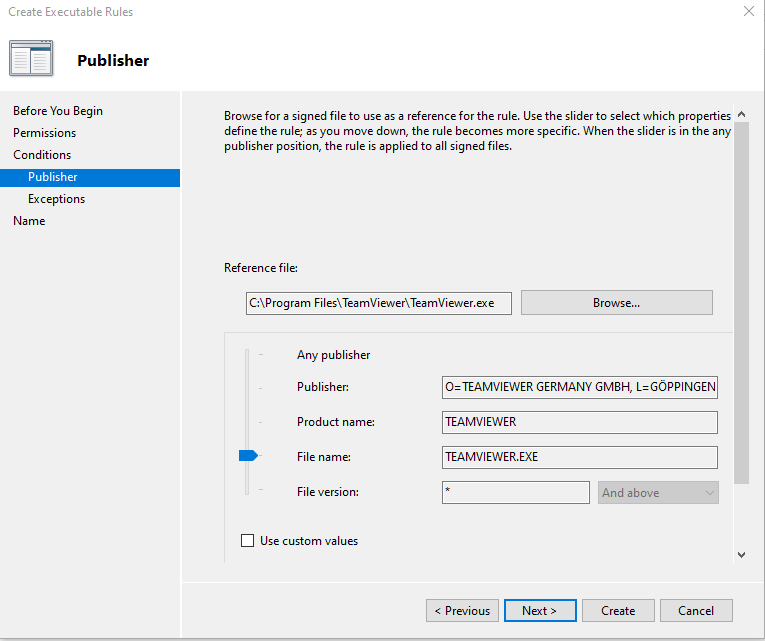
Selected Publisher
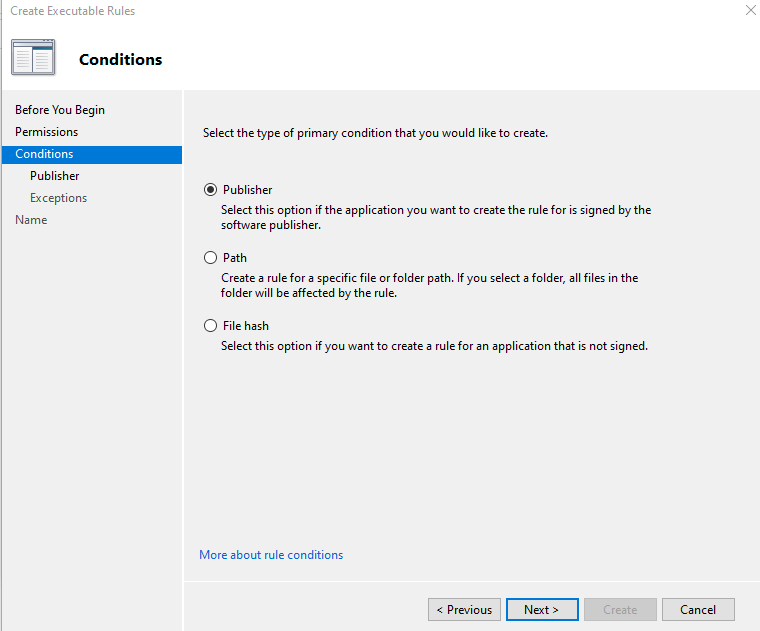
Browsed and chose Teamviewer.exe under reference file.
Selected File Name
Clicked on Next
No exceptions are required, so clicked on Next
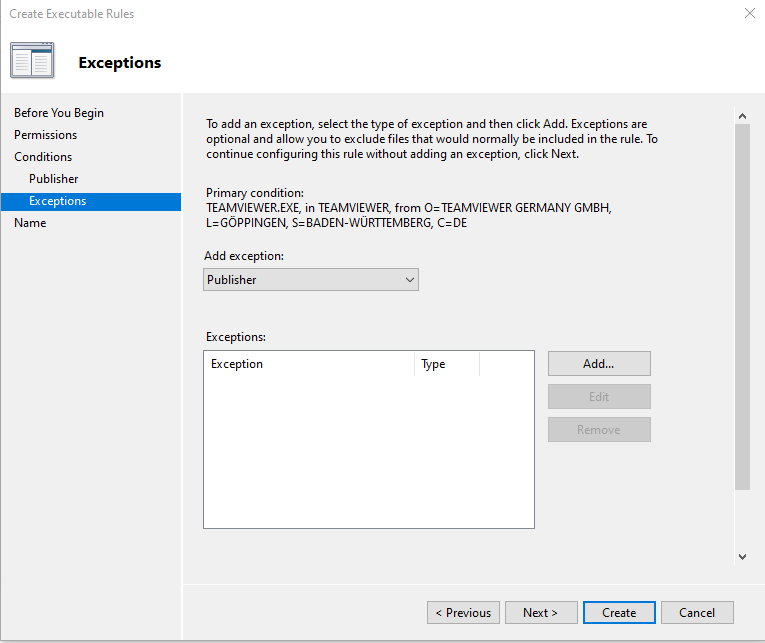
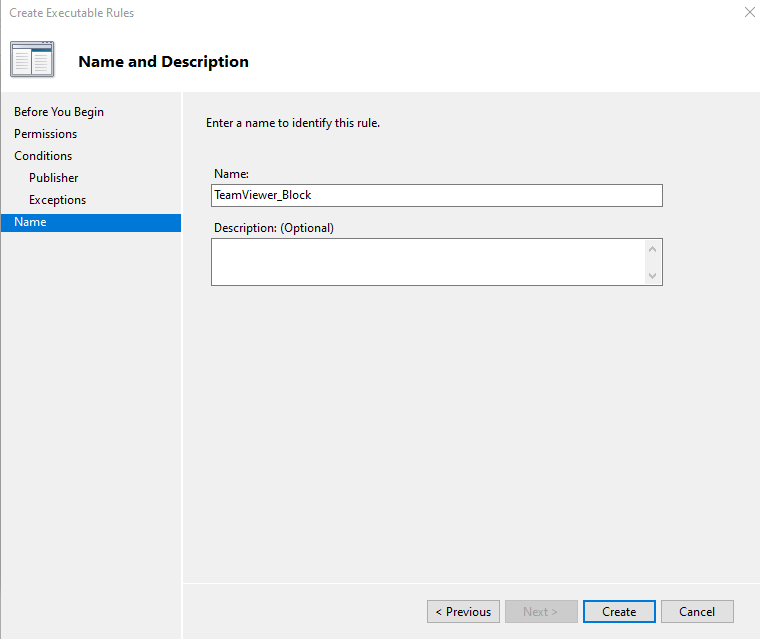
Provided a name for the rule
Clicked on Create
Rule has been created successfully.
Have followed the same steps again and created a rule for AnyDesk as well.
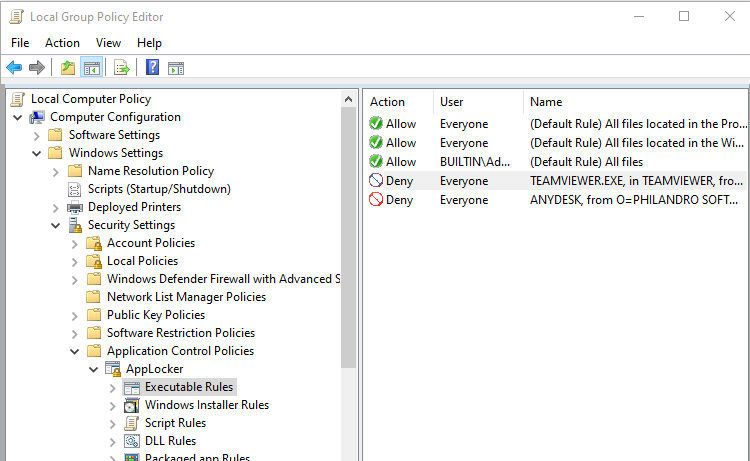
Exported this as a XML file and saved it as a XML file.
Cleared the policy
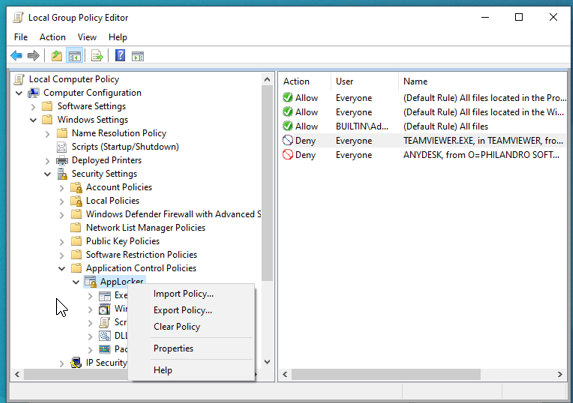
Opened up the local group policy editor again, went to Windows Installer Rules, and created default policy only without enabling it (Set to: Not Configured)
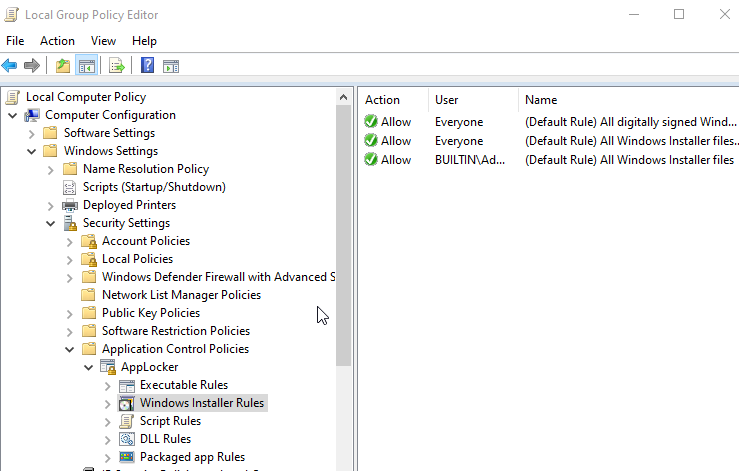
Similarly, created default rules for Script Rules, DLL Rules and Packaged App Rules without enabling them.
On Microsoft Intune Console, I went to Devices --> Windows --> Configuration Profiles --> Profiles --> Create Profile ---> Selected "Windows 10 or later" as Platform --> Selected "Template" as profile type --> "Custom" as Template Name
Clicked On "Add Row" under "OMA-URI Settings"
Provided Name: AppLocker_exe
Description: XML doc to restrict .exe files
OMA-URI: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/apps/EXE/Policy
Uploaded XML File:-
<AppLockerPolicy Version="1">
<RuleCollection Type="Exe" EnforcementMode="Enabled">
<FilePathRule Id="921cc481-6e17-4653-8f75-050b80acca20" Name="(Default Rule) All files located in the Program Files folder" Description="Allows members of the Everyone group to run applications that are located in the Program Files folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%PROGRAMFILES%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="a61c8b2c-a319-4cd0-9690-d2177cad7b51" Name="(Default Rule) All files located in the Windows folder" Description="Allows members of the Everyone group to run applications that are located in the Windows folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%WINDIR%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="fd686d83-a829-4351-8ff4-27c7de5755d2" Name="(Default Rule) All files" Description="Allows members of the local Administrators group to run all applications." UserOrGroupSid="S-1-5-32-544" Action="Allow">
<Conditions>
<FilePathCondition Path="*" />
</Conditions>
</FilePathRule>
<FilePublisherRule Id="0cc2d920-9609-418a-8244-a1de20ed685c" Name="ANYDESK, from O=PHILANDRO SOFTWARE GMBH, L=STUTTGART, S=BADEN-WÜRTTEMBERG, C=DE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=PHILANDRO SOFTWARE GMBH, L=STUTTGART, S=BADEN-WÜRTTEMBERG, C=DE" ProductName="ANYDESK" BinaryName="*">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="d7f4c601-0918-40e1-b8ee-aae774e4d118" Name="TEAMVIEWER.EXE, in TEAMVIEWER, from O=TEAMVIEWER GERMANY GMBH, L=GÖPPINGEN, S=BADEN-WÜRTTEMBERG, C=DE" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=TEAMVIEWER GERMANY GMBH, L=GÖPPINGEN, S=BADEN-WÜRTTEMBERG, C=DE" ProductName="TEAMVIEWER" BinaryName="TEAMVIEWER.EXE">
<BinaryVersionRange LowSection="*" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
</RuleCollection>
</AppLockerPolicy>
Added an another row for AppLocker_MSI
Name: AppLocker_MSI
Description: App Locker policy for MSI Installers
OMA-URI: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/Apps/MSI/Policy
Uploaded XML:-
<AppLockerPolicy Version="1">
<RuleCollection Type="Msi" EnforcementMode="NotConfigured">
<FilePublisherRule Id="b7af7102-efde-4369-8a89-7a6a392d1473" Name="(Default Rule) All digitally signed Windows Installer files" Description="Allows members of the Everyone group to run digitally signed Windows Installer files." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePublisherCondition PublisherName="*" ProductName="*" BinaryName="*">
<BinaryVersionRange LowSection="0.0.0.0" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePathRule Id="5b290184-345a-4453-b184-45305f6d9a54" Name="(Default Rule) All Windows Installer files in %systemdrive%\Windows\Installer" Description="Allows members of the Everyone group to run all Windows Installer files located in %systemdrive%\Windows\Installer." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%WINDIR%\Installer\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="64ad46ff-0d71-4fa0-a30b-3f3d30c5433d" Name="(Default Rule) All Windows Installer files" Description="Allows members of the local Administrators group to run all Windows Installer files." UserOrGroupSid="S-1-5-32-544" Action="Allow">
<Conditions>
<FilePathCondition Path="*.*" />
</Conditions>
</FilePathRule>
</RuleCollection>
</AppLockerPolicy>
Added a row for Scripts:-
Name: AppLocker_Script
Description: App Locker script default policy to allow all scripts
OMA-URI:
./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/Apps/Script/Policy
Uploaded XML File:-
<AppLockerPolicy Version="1">
<RuleCollection Type="Script" EnforcementMode="NotConfigured">
<FilePathRule Id="06dce67b-934c-454f-a263-2515c8796a5d" Name="(Default Rule) All scripts located in the Program Files folder" Description="Allows members of the Everyone group to run scripts that are located in the Program Files folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%PROGRAMFILES%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="9428c672-5fc3-47f4-808a-a0011f36dd2c" Name="(Default Rule) All scripts located in the Windows folder" Description="Allows members of the Everyone group to run scripts that are located in the Windows folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%WINDIR%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="ed97d0cb-15ff-430f-b82c-8d7832957725" Name="(Default Rule) All scripts" Description="Allows members of the local Administrators group to run all scripts." UserOrGroupSid="S-1-5-32-544" Action="Allow">
<Conditions>
<FilePathCondition Path="*" />
</Conditions>
</FilePathRule>
</RuleCollection>
</AppLockerPolicy>
One more row for Store Apps:-
Name: AppLocker_StoreApps
Descriptions: Default Appx policy to allow all store Apps
OMA-URI: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/apps/StoreApps /Policy
<AppLockerPolicy Version="1">
<RuleCollection Type="Appx" EnforcementMode="NotConfigured">
<FilePublisherRule Id="a9e18c21-ff8f-43cf-b9fc-db40eed693ba" Name="(Default Rule) All signed packaged apps" Description="Allows members of the Everyone group to run packaged apps that are signed." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePublisherCondition PublisherName="*" ProductName="*" BinaryName="*">
<BinaryVersionRange LowSection="0.0.0.0" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
</RuleCollection>
</AppLockerPolicy>
Another one for DLL:-
Name: AppLocker_DLL
Description: Dynamic Link Library app locker policy allows all by default
OMA-URI: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/Apps/DLL/Policy
Uploaded XML file:-
<AppLockerPolicy Version="1">
<RuleCollection Type="Dll" EnforcementMode="NotConfigured">
<FilePathRule Id="bac4b0bf-6f1b-40e8-8627-8545fa89c8b6" Name="(Default Rule) Microsoft Windows DLLs" Description="Allows members of the Everyone group to load DLLs located in the Windows folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%WINDIR%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="3737732c-99b7-41d4-9037-9cddfb0de0d0" Name="(Default Rule) All DLLs located in the Program Files folder" Description="Allows members of the Everyone group to load DLLs that are located in the Program Files folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%PROGRAMFILES%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="fe64f59f-6fca-45e5-a731-0f6715327c38" Name="(Default Rule) All DLLs" Description="Allows members of the local Administrators group to load all DLLs." UserOrGroupSid="S-1-5-32-544" Action="Allow">
<Conditions>
<FilePathCondition Path="*" />
</Conditions>
</FilePathRule>
</RuleCollection>
</AppLockerPolicy>
Have deployed it to the group of users (Microsoft 365 Security Group)
Number of members in the group: 7 (including me)
But all policies are providing an error code: -2016345596
Error reason: Syncml(516): Command was inside Atomic element and Atomic failed. This command was not rolled back successfully.
I'm stuck up here. Can you please assist me in resolving the issue and let me know what went wrong please?
