Hello @A.Frick - ipstyle ,
Welcome to Microsoft Q&A Platform. Thank you for reaching out & hope you are doing well.
I understand that you would like to learn about Azure network security and how are Azure firewalls & NSG implemented along with the cost associated with them.
Thank you JimmySalian-2011 for your inputs above. I've also added some more points below:
I am interested in learning about your Azure landscape setup with regards to network security.
You can find the collection of Azure best practices to enhance your network security in the below article:
https://learn.microsoft.com/en-us/azure/security/fundamentals/network-best-practices
Do you prioritize Azure Firewalls, Fortigate Firewalls, or Network Security Groups?
Azure Firewalls and Network Security Groups are native solutions for network security in Azure.
FortiGate Firewalls are 3rd party offerings which are available to deploy in Azure via the Azure Marketplace.
https://learn.microsoft.com/en-us/marketplace/azure-marketplace-overview
https://azuremarketplace.microsoft.com/en-us/marketplace/apps/fortinet.fortinet-fortigate?tab=overview
Network security groups (NSGs) are used to restrict network traffic within the virtual network.
Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. It's a fully stateful firewall-as-a-service with built-in high availability and unrestricted cloud scalability. You can centrally create, enforce, and log application and network connectivity policies across subscriptions and virtual networks. It provides both east-west and north-south traffic inspection.
The Azure Firewall service complements network security group functionality. Together, they provide better "defense-in-depth" network security. So, it is recommended to use them together.
Refer: https://learn.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
https://learn.microsoft.com/en-us/azure/firewall/overview
So, you can choose which service/product to use depending upon your existing setup and requirements.
I am curious about the cost implications of using Azure Firewall and how that affects your strategy for services behind the firewall and Network Security Groups. Are there any strategies for minimizing network data costs associated with Azure Firewall?
As mentioned in the FAQ of Azure Firewall,
You can deploy Azure Firewall on any virtual network, but customers typically deploy it on a central virtual network and peer other virtual networks to it in a hub-and-spoke model. You can then set the default route from the peered virtual networks to point to this central firewall virtual network. Global VNet peering is supported, but it isn't recommended because of potential performance and latency issues across regions. For best performance, deploy one firewall per region.
The advantage of this model is the ability to centrally exert control on multiple spoke VNETs across different subscriptions. There are also cost savings as you don't need to deploy a firewall in each VNet separately. The cost savings should be measured versus the associate peering cost based on the customer traffic patterns.
You can find more best practices for Cost optimization with Azure Firewall in the below doc:
https://learn.microsoft.com/en-us/azure/well-architected/services/networking/azure-firewall?toc=%2Fazure%2Ffirewall%2Ftoc.json&bc=%2Fazure%2Ffirewall%2Fbreadcrumb%2Ftoc.json#cost-optimization
A hub and spoke topology is a way to isolate workloads while sharing common services. These services include identity and security. The hub is a virtual network (VNet) that acts as a central connection point to an on-premises network. The spokes are VNets that peer with the hub. Shared services are deployed in the hub, while individual workloads are deployed inside spoke networks.
You can find more about hub and spoke topology and their architecture in the below docs:
https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/ready/azure-best-practices/hub-spoke-network-topology
https://learn.microsoft.com/en-us/azure/architecture/reference-architectures/hybrid-networking/hub-spoke?tabs=cli
You can also incorporate these best practices and resources in your hybrid network (if you extend your on-premises network to Azure):
https://learn.microsoft.com/en-us/azure/architecture/reference-architectures/dmz/secure-vnet-dmz?tabs=portal
Coming to the pricing side of it:
There are no additional charges for creating NSGs in Microsoft Azure.
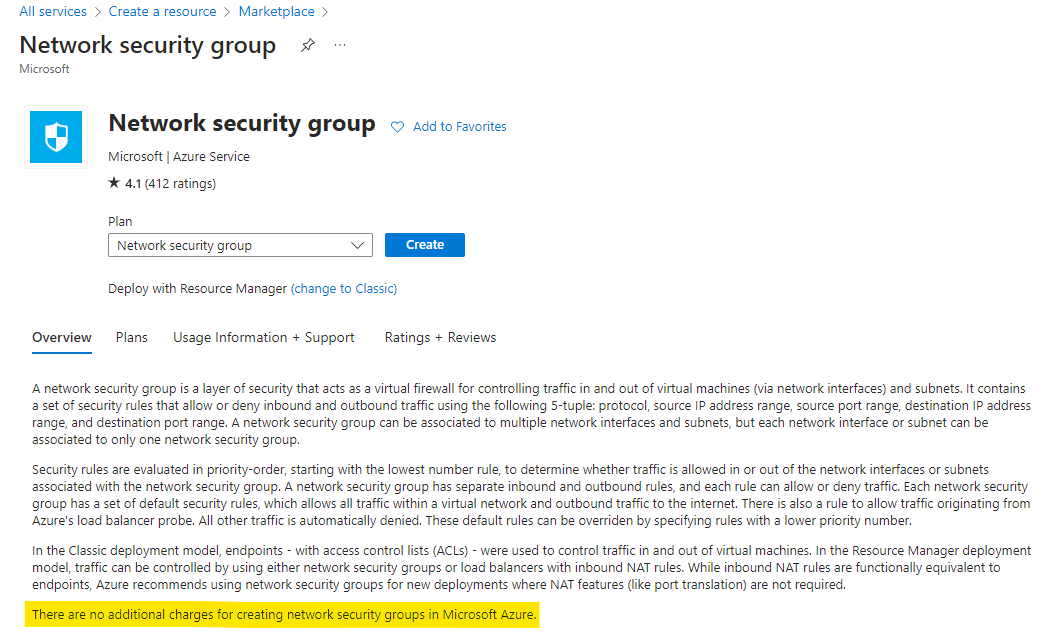
For Azure Firewall pricing, you can refer the below page:
https://azure.microsoft.com/en-in/pricing/details/azure-firewall/
Kindly let us know if the above helps or you need further assistance on this issue.
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.


