Hi,
This may be a novice question. I did a couple of hours of searching, so any docs links would be helpful.
I have an app that uses Azure AD for single sign-on via OIDC. We want to get the user's OpenID information as well as access to Key Vault on their behalf.
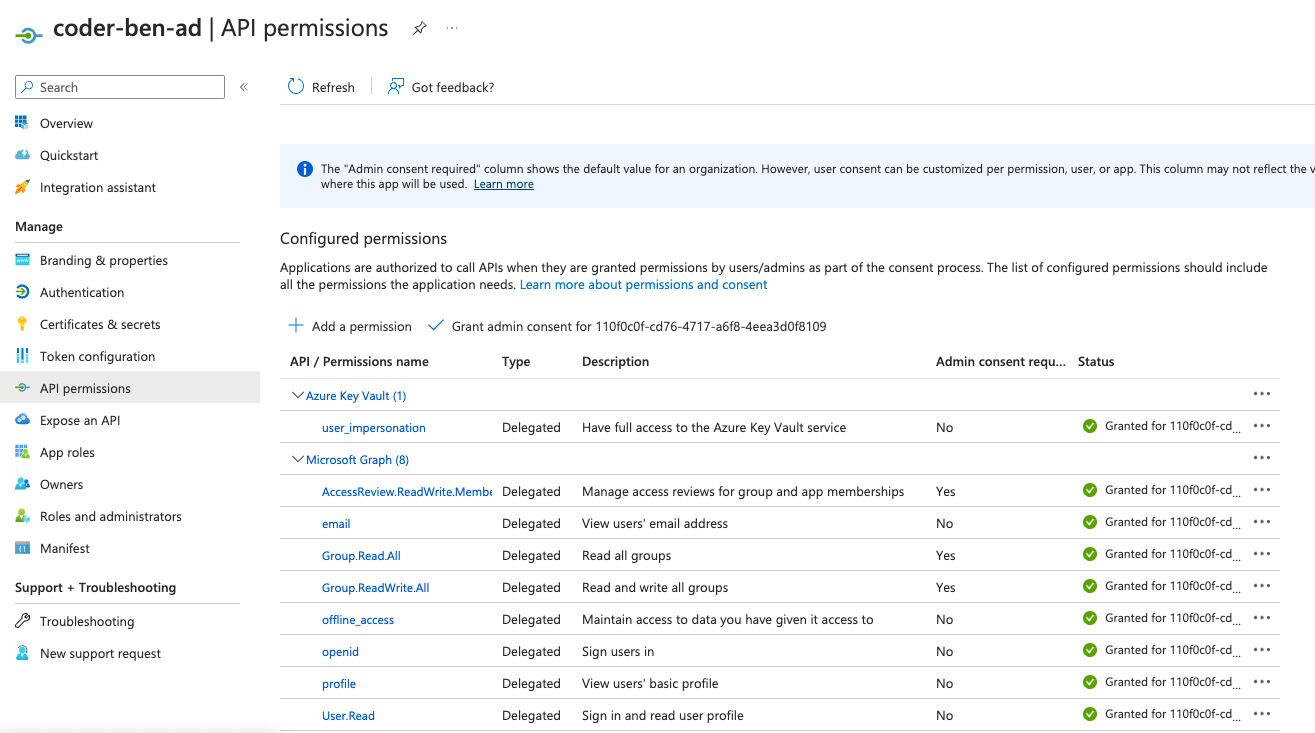
When requesting the following scopes openid,email,profile the JWT includes the proper permissions:
"scp": "AccessReview.ReadWrite.Membership email Group.Read.All Group.ReadWrite.All openid profile User.Read"
However, when adding the scope for Azure Key Vault (openid,email,profile,https://vault.azure.net/user_impersonation, the JWT only includes the user_impersonation permission for Vault, and none of the OpenID stuff:
"scp": "user_impersonation",
This prevents the token from working in the userinfo endpoint since I'm providing a key vault token to the graph API
{"error":{"code":"InvalidAuthenticationToken","message":"Access token validation failure. Invalid audience.","innerError":{"date":"2023-08-01T19:35:54","request-id":"3595a006-b767-4eeb-9db3-9fa25502ed37","client-request-id":"3595a006-b767-4eeb-9db3-9fa25502ed37"}}}
I'm still able to get the OpenID claims via the token that is sent, but this feels like a bit of a workaround since I won't be able to get access to a third API (e.g. Azure Maps) down the road. What is the recommended way to get tokens for multiple APIs/scopes (e.g. graph, key vault, azure maps) via OIDC? When I combine graph scopes and key vault scopes (https://graph.microsoft.com/AccessReview.ReadWrite.Membership,https://graph.microsoft.com/email,https://graph.microsoft.com/Group.Read.All,https://graph.microsoft.com/Group.ReadWrite.All,https://graph.microsoft.com/openid,https://graph.microsoft.com/profile,https://graph.microsoft.com/User.Read,https://vault.azure.net/user_impersonation) I get another error:
"detail": "oauth2: \"invalid_request\" \"AADSTS28003: Provided value for the input parameter scope cannot be empty when requesting an access token using the provided authorization code. Please specify a valid scope.\\r\\nTrace ID: e5a47177-3912-49c8-9611-c5ff93746600\\r\\nCorrelation ID: 2213072a-2134-41af-9976-a85fc82cbf89\\r\\nTimestamp: 2023-08-01 20:32:52Z\"
I assume there is not "one token to rule them all," so I'm curious if there are ways the app can ask for permissions once via OIDC and then access multiple APIs.
Ben

