I am trying to implement per-user MFA on Azure AD B2C so we can support a segment of our external customers with MFA offered as an option. I have successfully tested MFA when it's on at the user-flow (policy) level (for all users). However, when I enable it at a per-user level, I get an error "Invalid username or password" using the same test account I previously tested MFA ON/OFF with. Below are my test cases and results - the last test case may be unnecessary but I added it to show that regardless of the state of MFA at the user flow level, if it's enabled per-user, I get the error message.
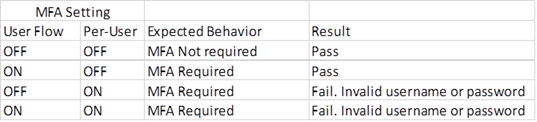
I reviewed the "Sign-in logs" and ran a diagnosis on one of the failed attempts and got this back...which doesn't make sense because when I click on the link I see valid sign-in methods and my default which is my phone.
"Based on the information you provided the user [redacted] was trying to sign into CPIM PowerShell Client but the user sign-in was interrupted for required setup of Multi-Factor Authentication (MFA).
This can happen when the user is required to set MFA up for the first time or when an admin has set their account to require a new proofup for some reason.
This interrupt can be avoided next time by having the user finish the MFA setup (also known as "proofup"). If the user has not finished the MFA setup you can direct them to https://mysignins.microsoft.com/security-info. This means the user would simply configure and verify the additional authentication methods for MFA. For example, if using the Microsoft Authenticator App, the user can use the scan QR Code or use the code & url provided to add a sign-in method.
After proofup is done the user will be able to sign-in for the application they were trying to use."

