
Hello @Nick@519 ,
Thank you for your update and sharing.
I am so glad that the problem was resolved.
As the question: is there a way to see who exactly made the change?
I have done a test in my lab and it worked.
If we want to check who exactly made the change on this machine (not all machines in the domain).
We can configure the following audit policy through local group policy on this machine(or maybe you have already configured it as mentioned).
1.Type gpedit.msc on Start search bar and click Enter.
2.Navigate to Computer Configuration\Windows settings\security settings\Advanced Audit Policy Configuration\System Audit Policies- Local Group Policy Object\Policy Change\Audit Authentication Policy Change==> Success and Failure.
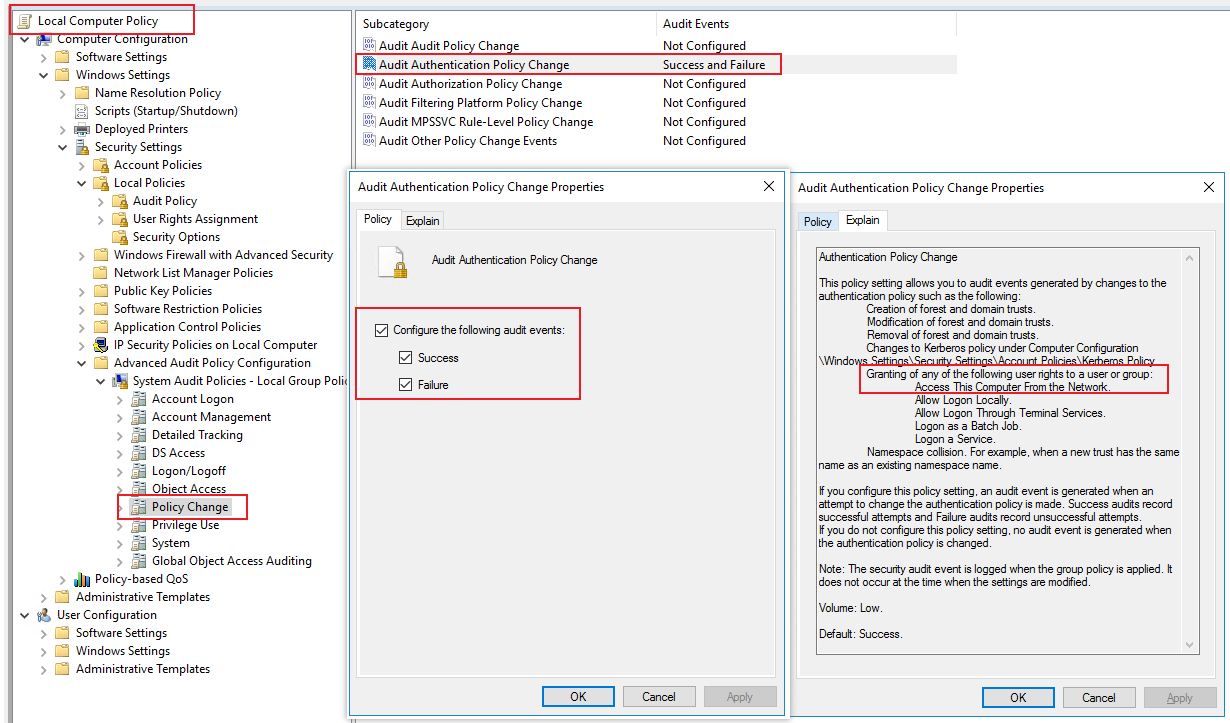
3.Run gpupdate /force or restart the machine to refresh the GPO setting.
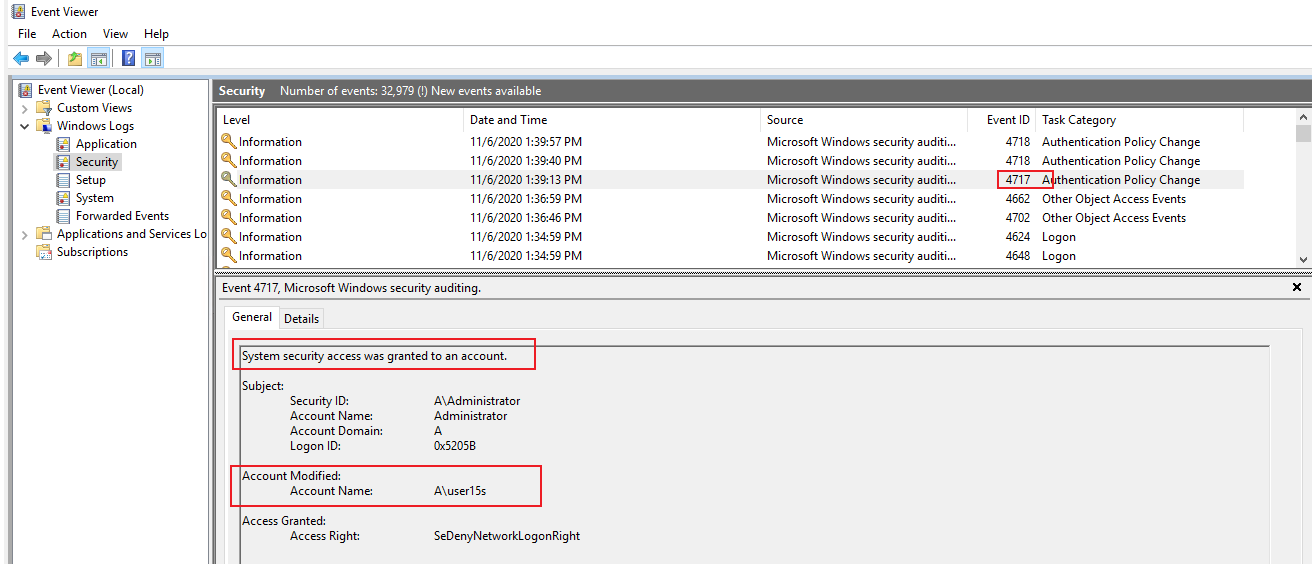
4.If I add a user or group Deny access to this computer from the network under Local Group Policy Editor > Local Computer Policy > Computer Configuration > Windows Settings > Security Settings > Local Policies > Users Rights Assignments.
I will see event ID 4717 as below (I added user account user15s using A\administrator).
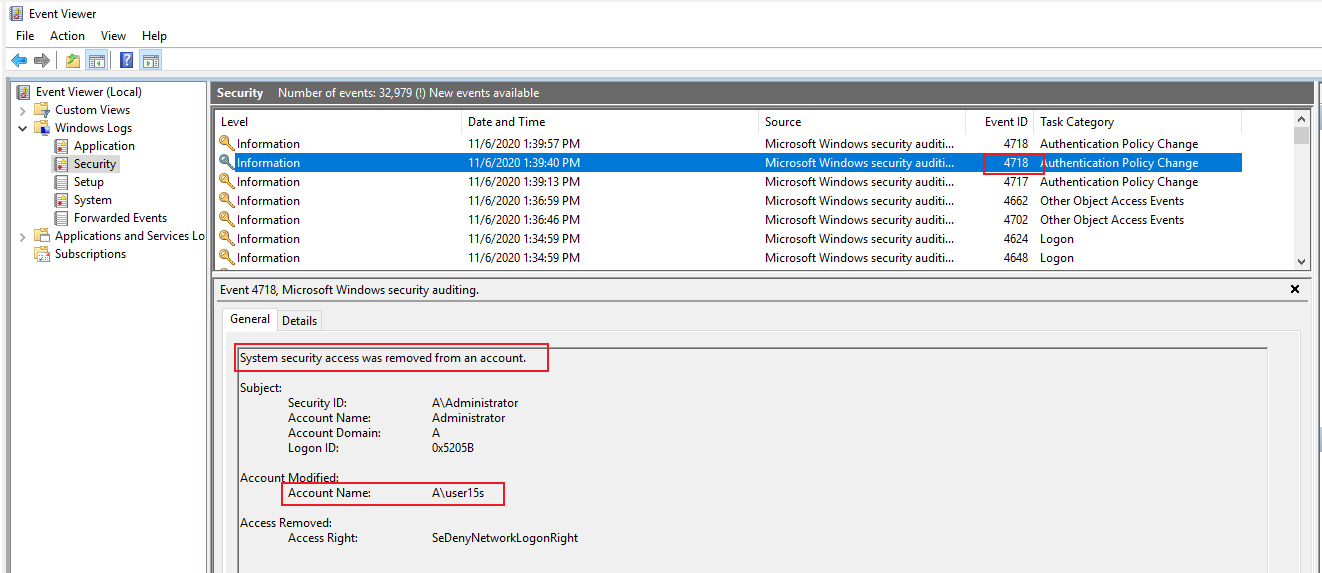
5.4.If I removed a user or group Deny access to this computer from the network under Local Group Policy Editor > Local Computer Policy > Computer Configuration > Windows Settings > Security Settings > Local Policies > Users Rights Assignments.
I will see event ID 4718 as below(I removed user account user15s using A\administrator)..
Hope the information above is helpful. If anything is unclear, please feel free to let us know.
Best Regards,
Daisy Zhou