From above description I could understand that you are looking to add roles of member/guest while signing into the application to access token rather then ID token
Please do correct me if this is not the ask.
As per : Add app roles to your application and receive them in the token. This is by design:
When the app role is set to enabled, any users, applications or groups who are assigned has it included in their tokens. These can be access tokens when your app is the API being called by an app or ID tokens when your app is signing in a user.
- Ensure that application have Implicit and hybrid grants flow enabled:
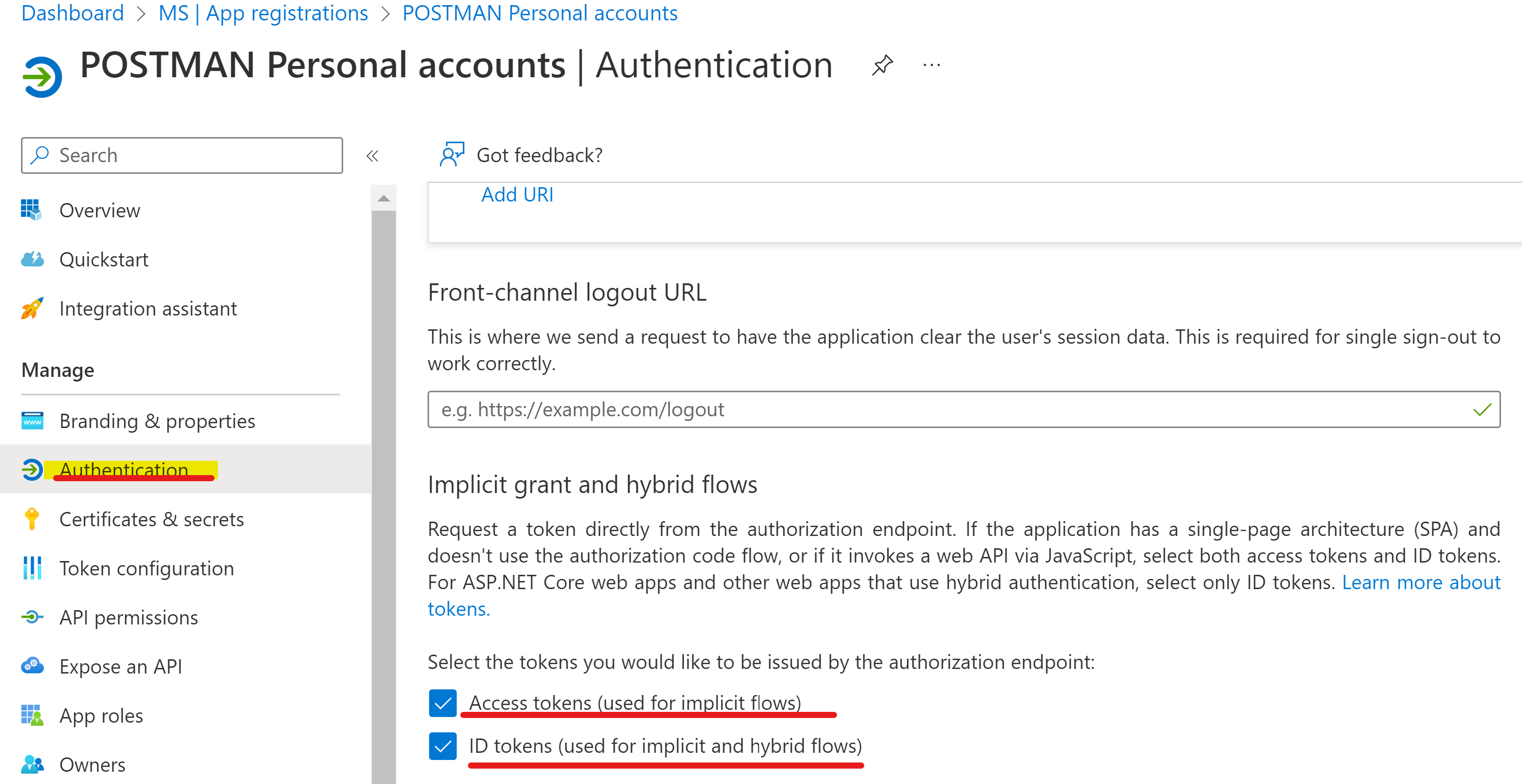
- The endpoint must be hitting organization endpoint and not common/personal, as they would not emit the roles. Given is the example
https://login.microsoftonline.com/{tenant_id}/oauth2/v2.0/authorize?
client_id={Application ID}
&response_type=code&id_token
&redirect_uri=http://localhost/myapp/
&response_mode=query
&scope=openid&https://graph.microsoft.com/mail.read
&state=12345
&nonce=abcde
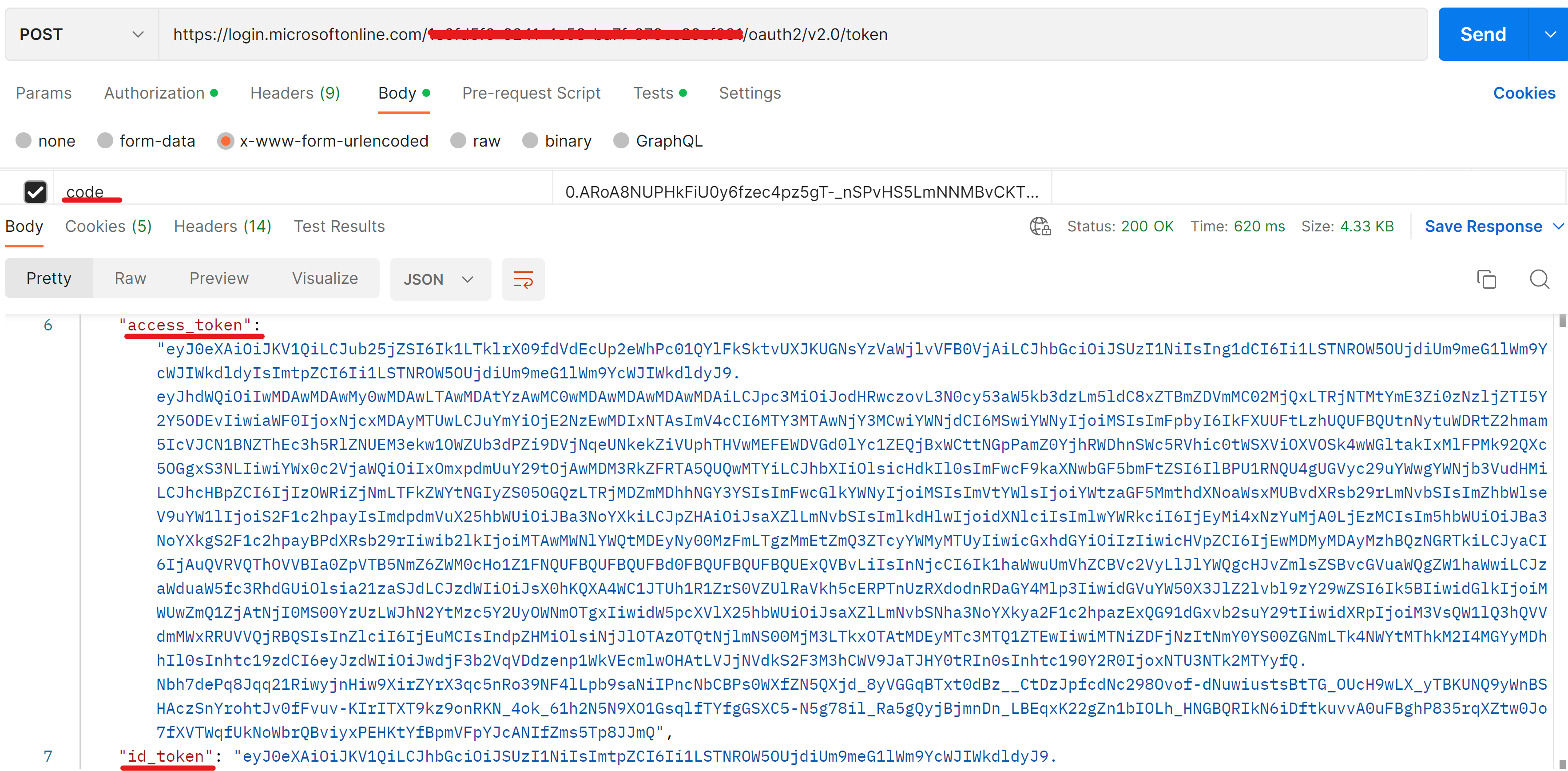
- Extract the code from request you sent above:
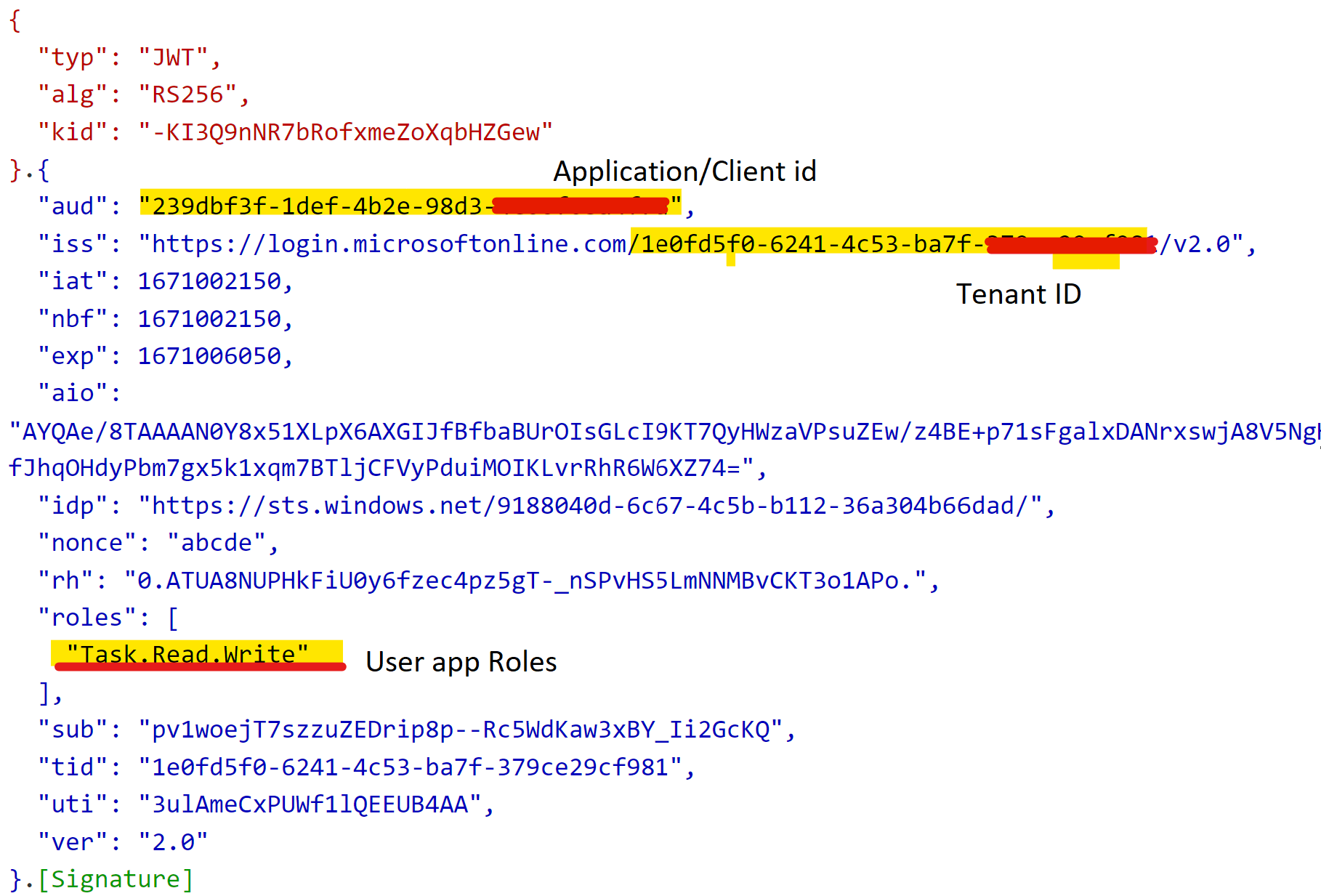
- The id_token will contain the user app roles assigned to the guest user and endpoint with tenant id:
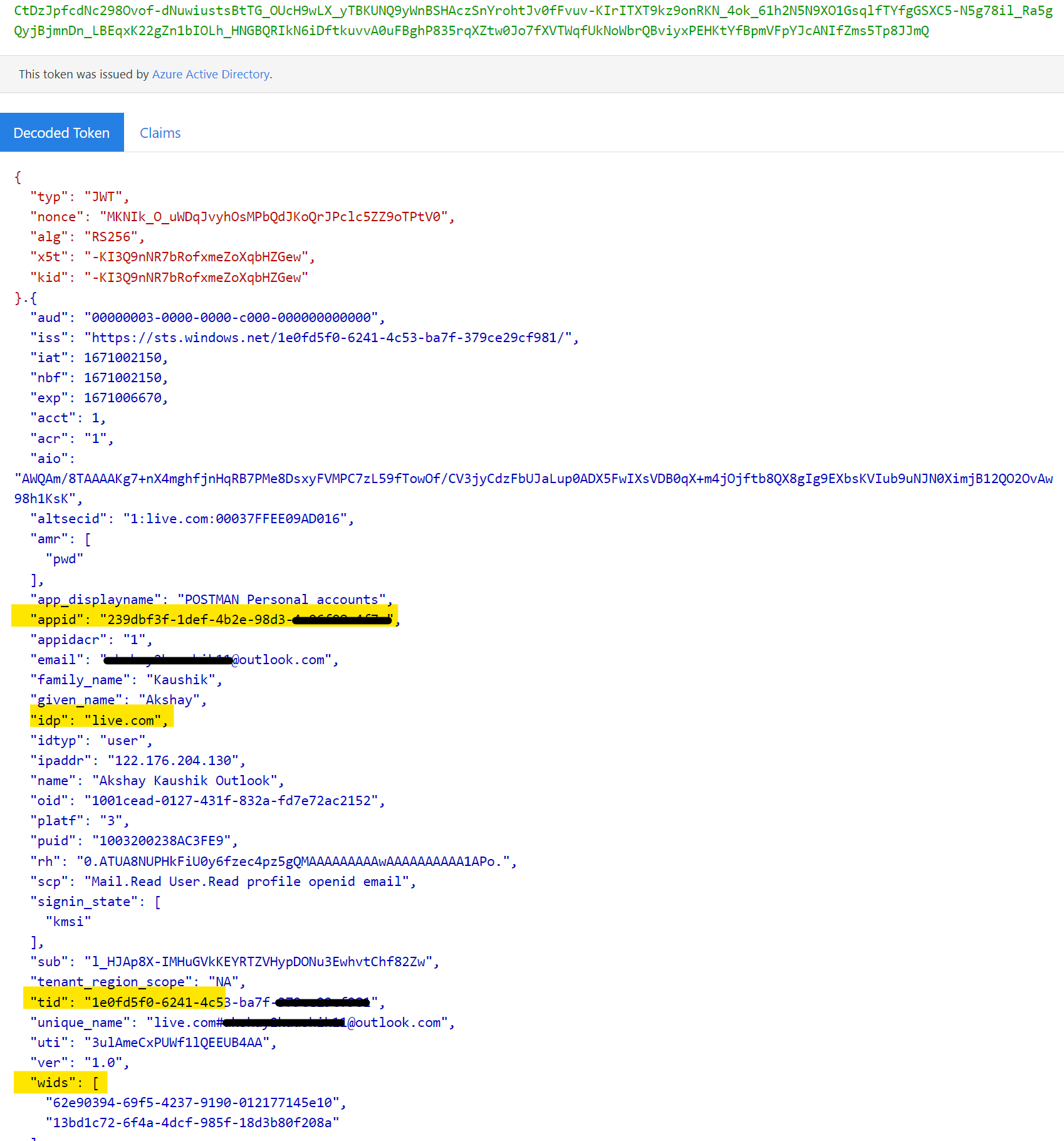
- The access_token will contain the User info, tenant id and wids claim (contain user permission templates GUID)
If you don't have any further queries and the suggestion works as per your business need. Please "Accept the answer (Yes)" and "share your feedback ". This will help us and others in the community as well.
Thanks,
Akshay Kaushik
