Issue
We tried to connect SQL server instances from Azure VM machine from SSMS. Azure VM is also part of same domain as of on-premise servers.
The connection of individual SQL server instances is functioning properly When trying to perform a test connection from linked servers, an error is mentione below. screenshot is as attached.
__Fout! Bestandsnaam niet opgegeven.__TITLE: Microsoft SQL Server Management Studio ------------------------------
The test connection to the linked server failed. ------------------------------ ADDITIONAL INFORMATION: An exception occurred while executing a Transact-SQL statement or batch. (Microsoft.SqlServer.ConnectionInfo) ------------------------------ Login failed for user 'NT AUTHORITY\ANONYMOUS LOGON'. OLE DB provider "SQLNCLI11" for linked server "ServerXXXXX" returned message "Invalid connection string attribute". (Microsoft SQL Server, Error: 18456) For help, click: https://docs.microsoft.com/sql/relational-databases/errors-events/mssqlserver-18456-database-engine-error ------------------------------ BUTTONS: OK ------------------------------
Resolution:
- Few MSSQL server were using MSA account as a logon account and few as a domain account.
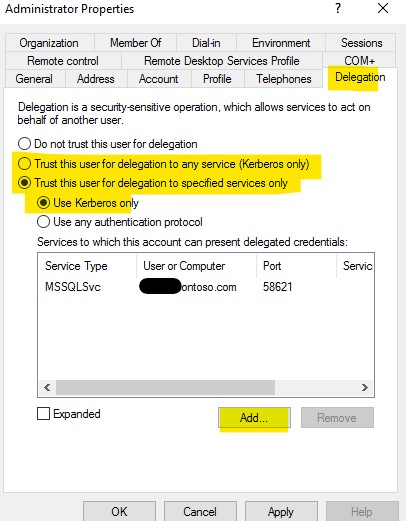
- Full delegation was provided to service account. (i.e. Unconstrained delegation)
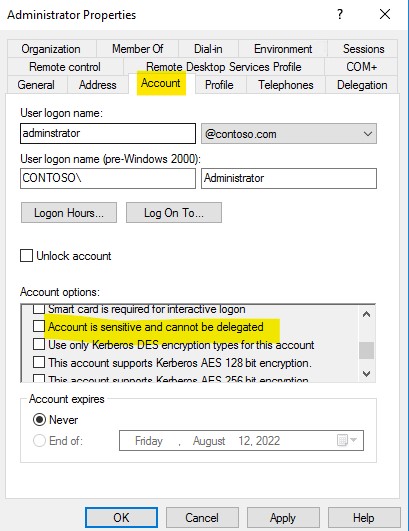
- When Credential Guard is enabled. Unconstrained delegation will not work.
- We disabled the credential guard on server side.
You can resolve this issue by changing delegation to constrained delegation and adding required services. When Credential Guard is enabled constrained delegation will work.
Note: I have used sqlcheck utility for analysis.