I have the following setup:
- a local (RRAS) Routing and Remote Access service set up as an SSTP VPN server
- a local RADIUS + (NPS) Network Policy Server with Entra NPS addon installed
- AD to AAD Connect Service to sync local and cloud accounts
The user is able to run the configured VPN profile on their device to attempt a login, and then gets promoted via their authenticator app to approve, but most of the time the user does not have enough time to approve the push notification. MFA push notification has a timeout of around a minute in Azure so why is it that the RRAS/NPS server only gives what seems to be 3-4 seconds before loading out and posting an error.
Additionally, the error received in the timeout is extremely inaccurate since it has nothing to do with the policy but the user taking too long to approve the push notification :
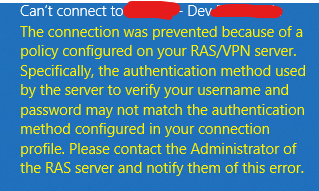
I have done over a dozen tests now timing the amount of time I have between the login attempt and when the push notification message works, after 5 or so seconds it no longer registers and the attempt fails all the time. If keep refreshing the authenticator app and jump on the push notification within the second it works all the time, so it is most definitely time-based and not a configuration issue.
How can this be extended on the RRAS/NPS server to be something more reasonable?
Additional Note: with Entra MFA disabled, the user authenticates and connects to the VPN in less than a second, so authentication speed between the VPN server, NPS and domain is fast, it is 100% the amount of time it takes for the NPS server to authenticate against Azure MFA.


