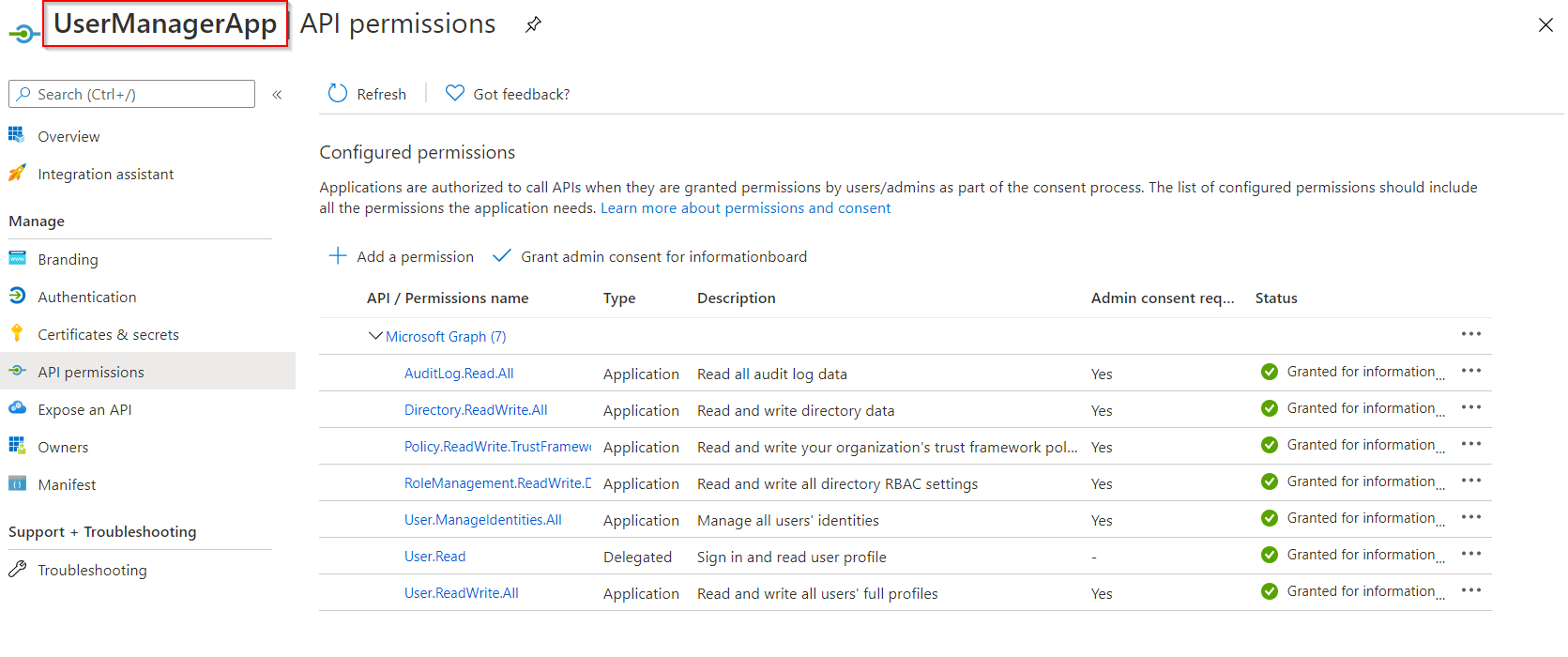
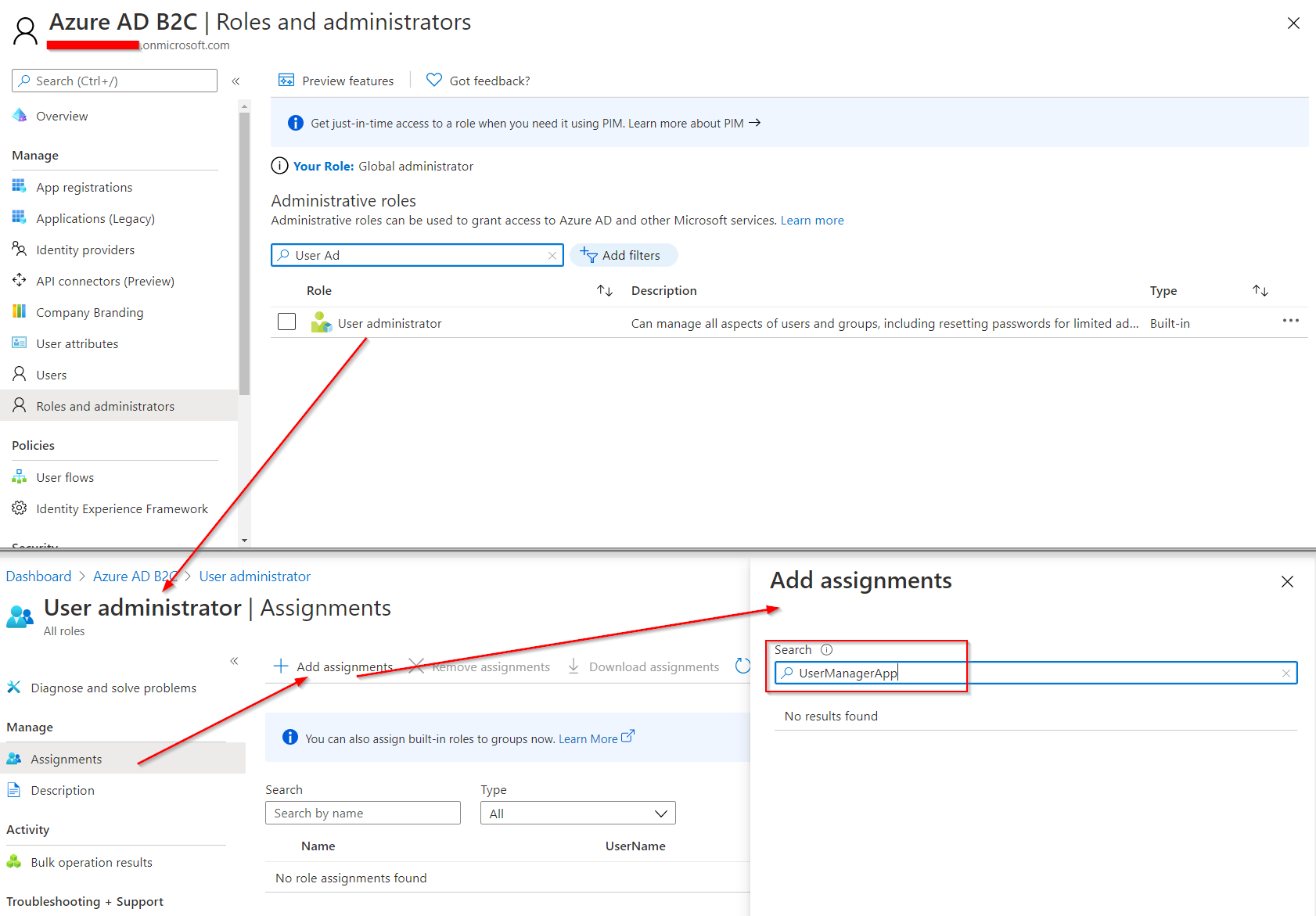
@Leandro Teles and @arun mohan ,
Thank you both for the quick follow-up! I've created a short GIF that should help walk you through the steps.
@Varun CT
I've reached out to our Product Group regarding your ask and providing them the details you mentioned.
-Is there any way to automate this process without Graph explorer?(i.e. using AzureAD app registration)
Alternate Solution:
Using this MS Graph API to assign the service principal of the application the necessary role if desired.
- Find the service principal id of the application. You can use GET /servicePrincipals to do this. Graph Explorer Link.
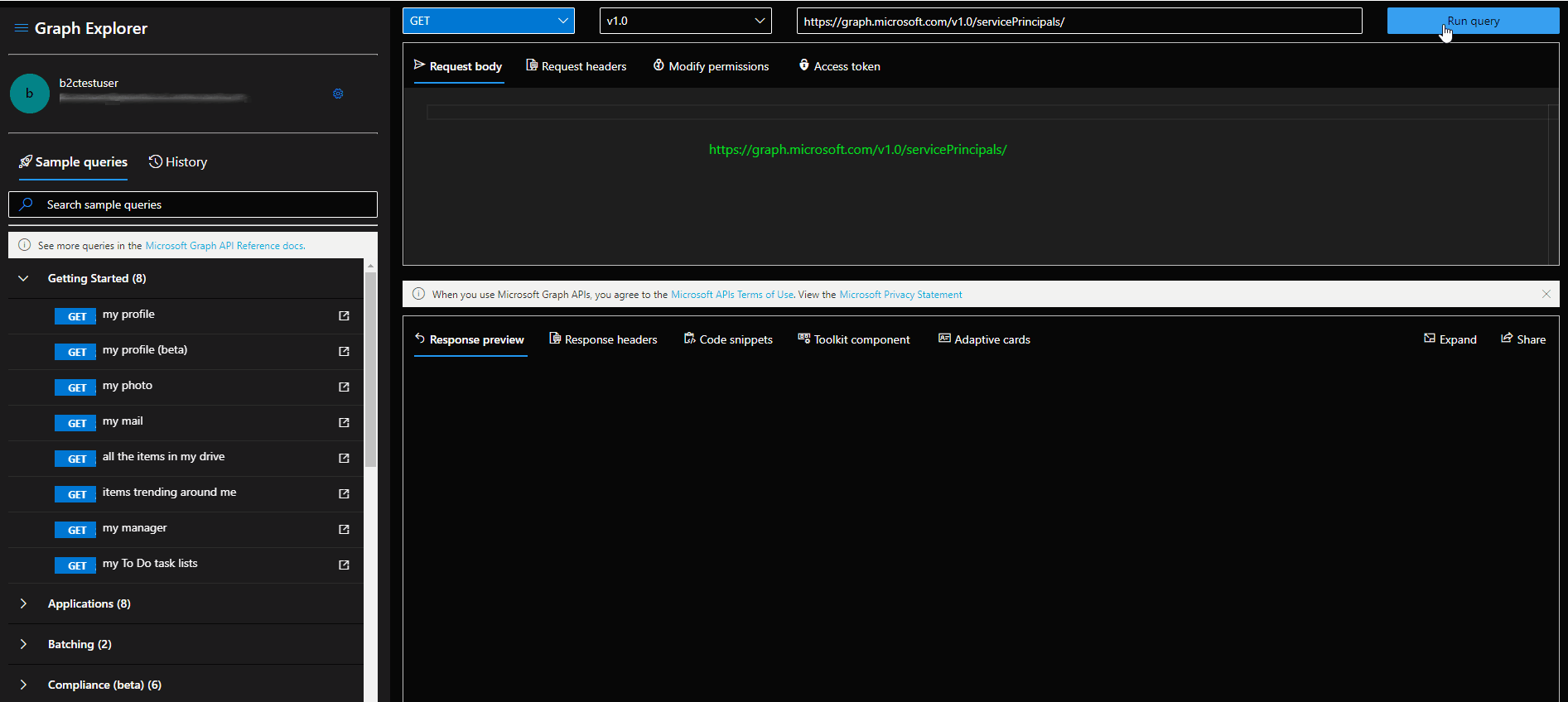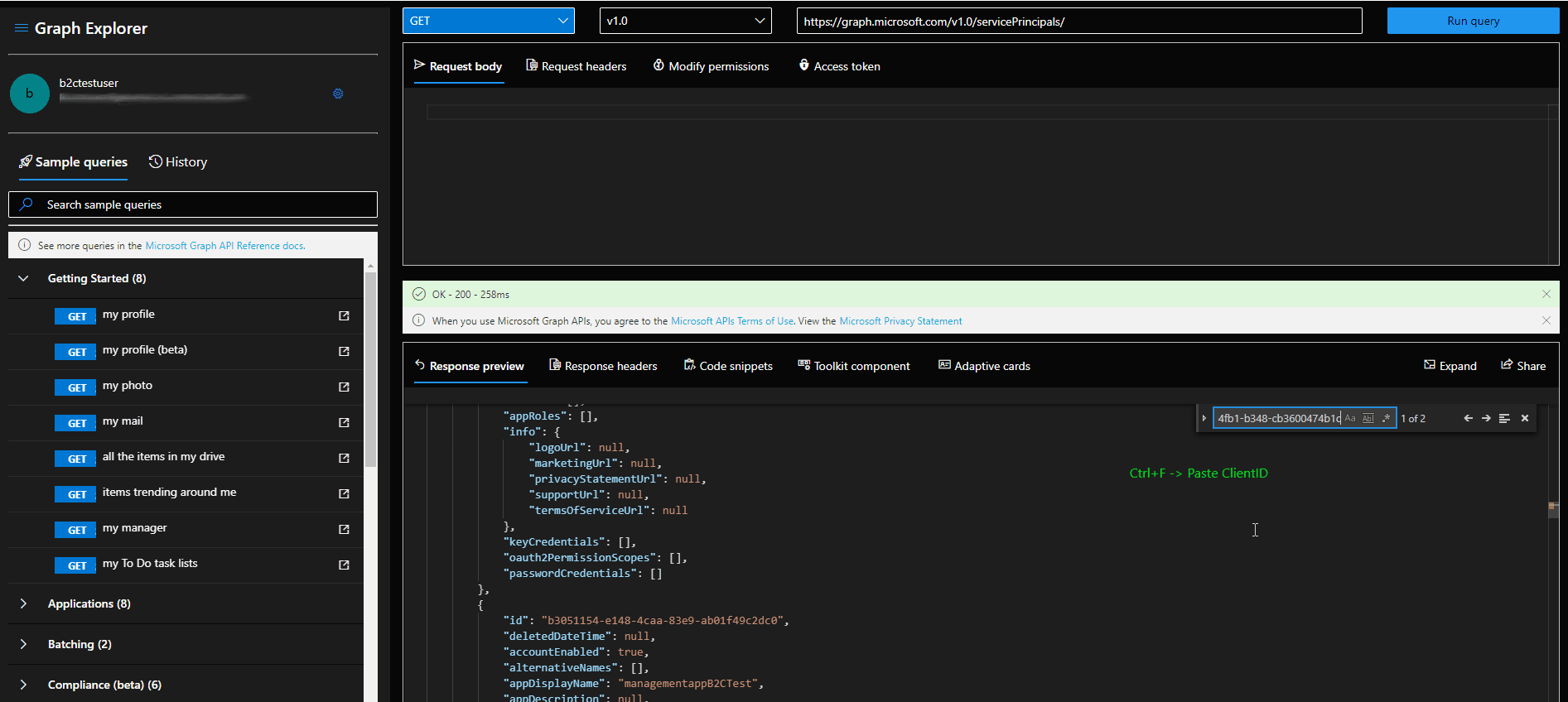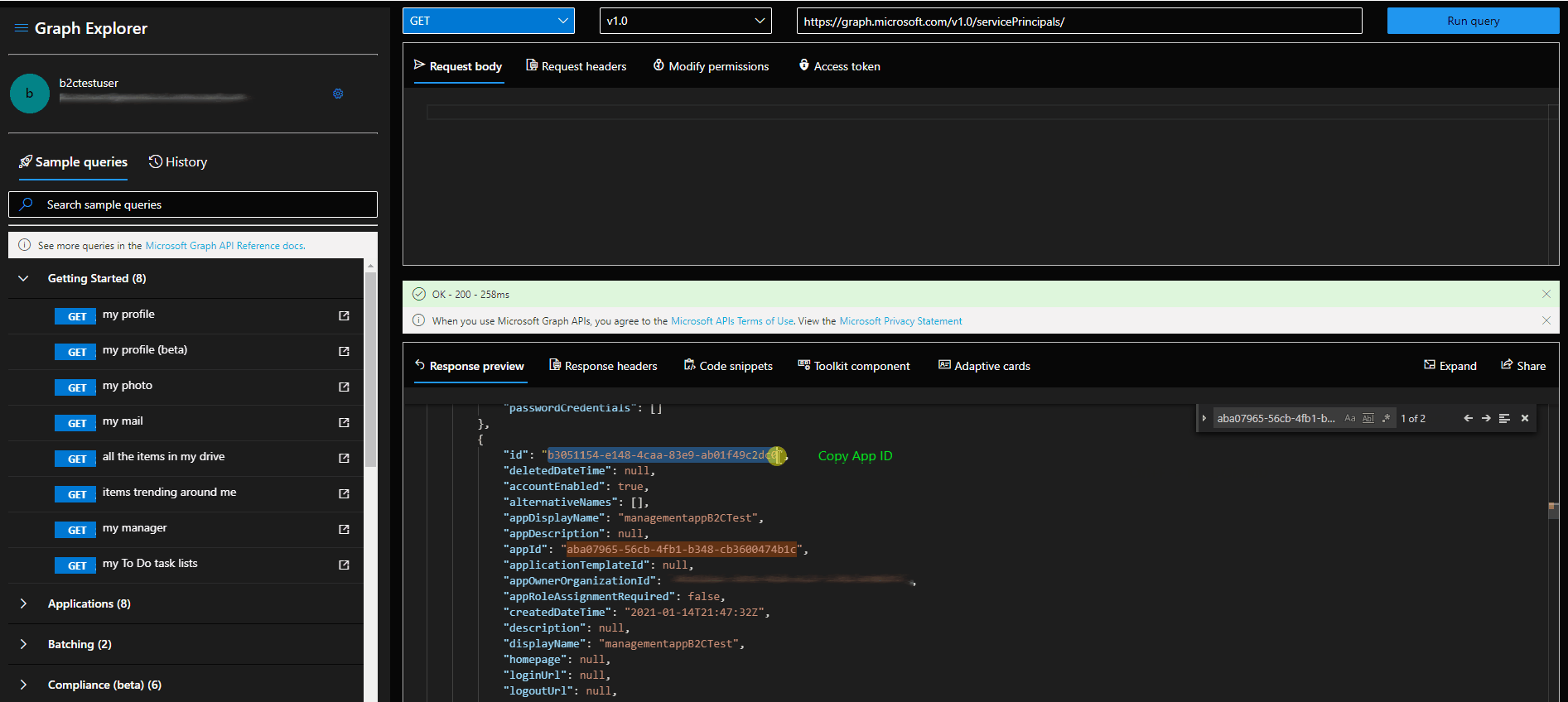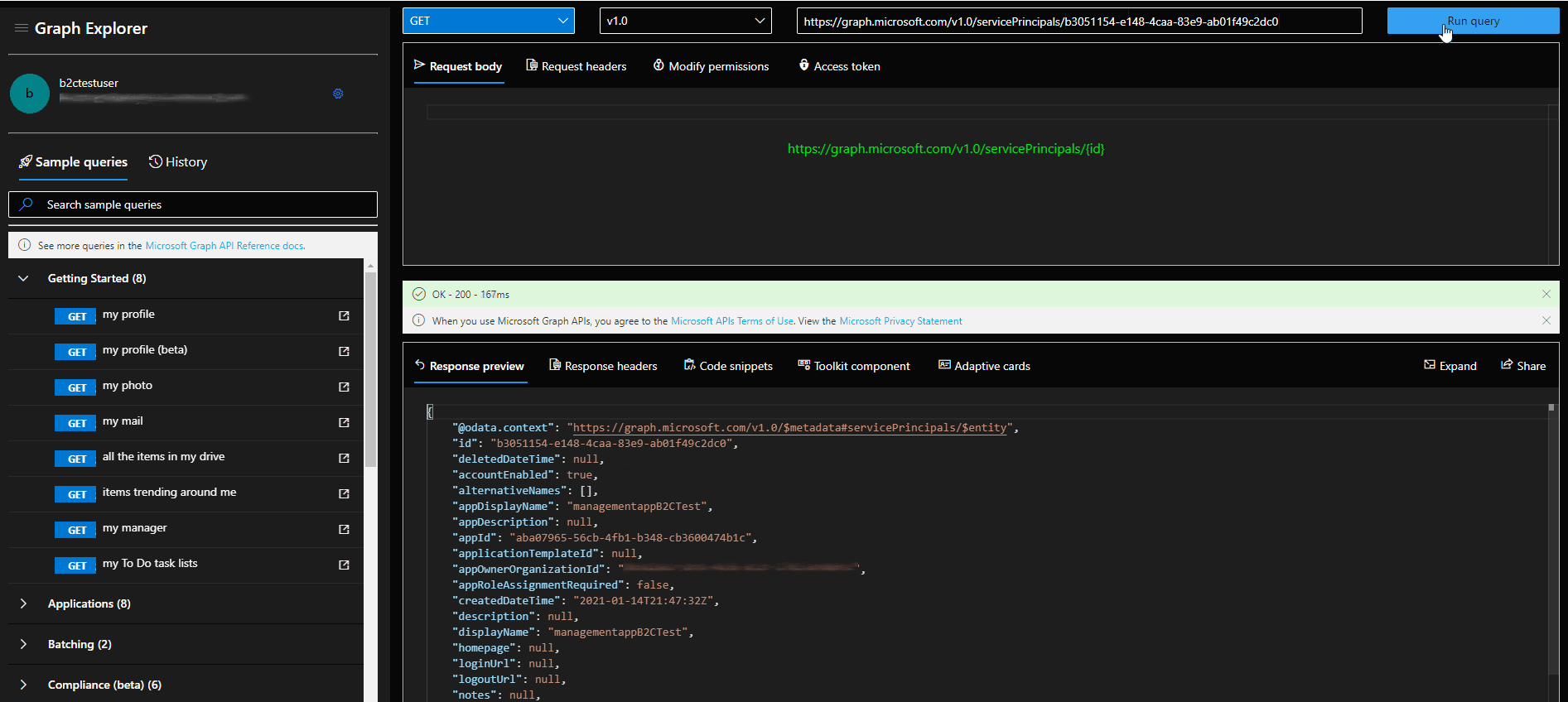
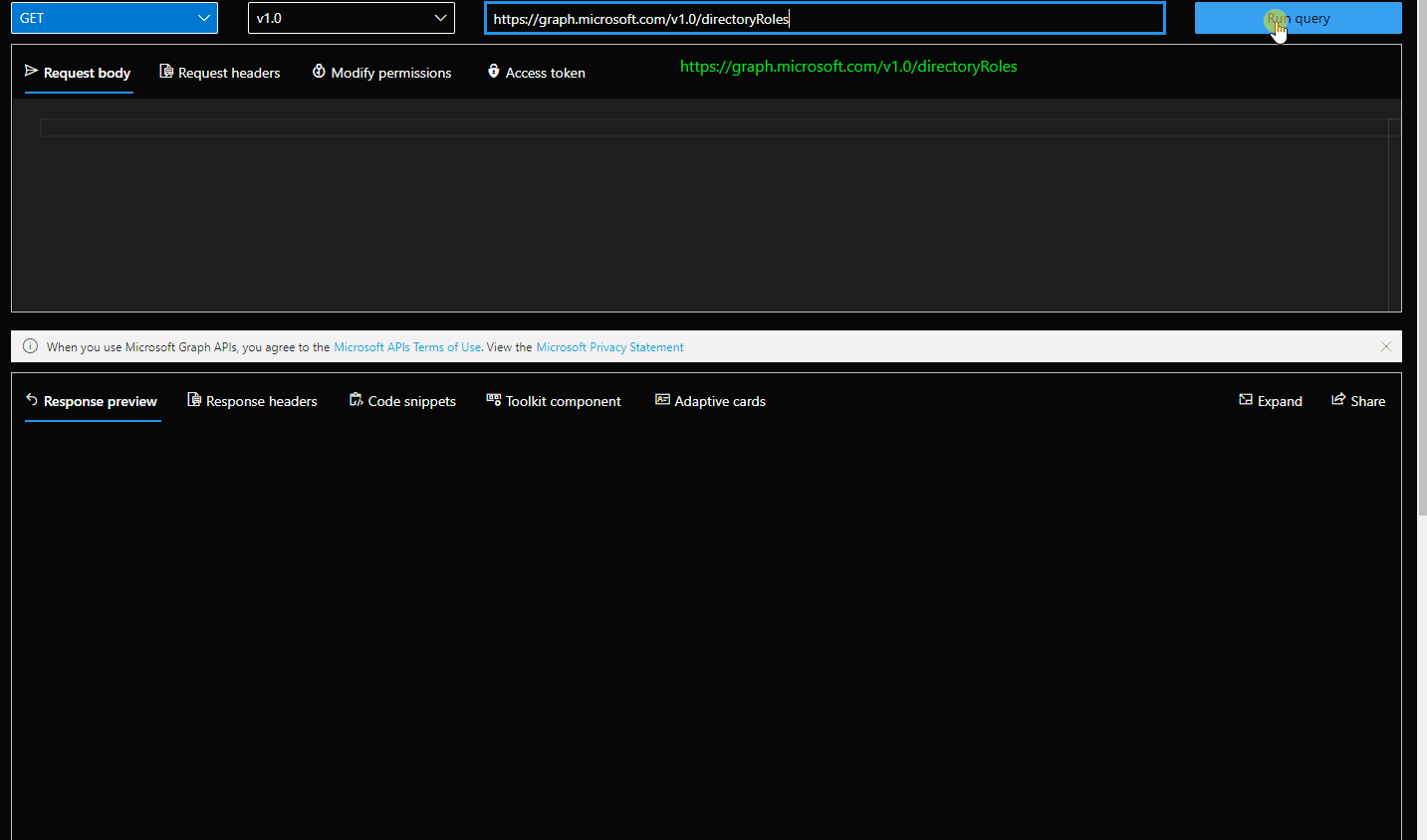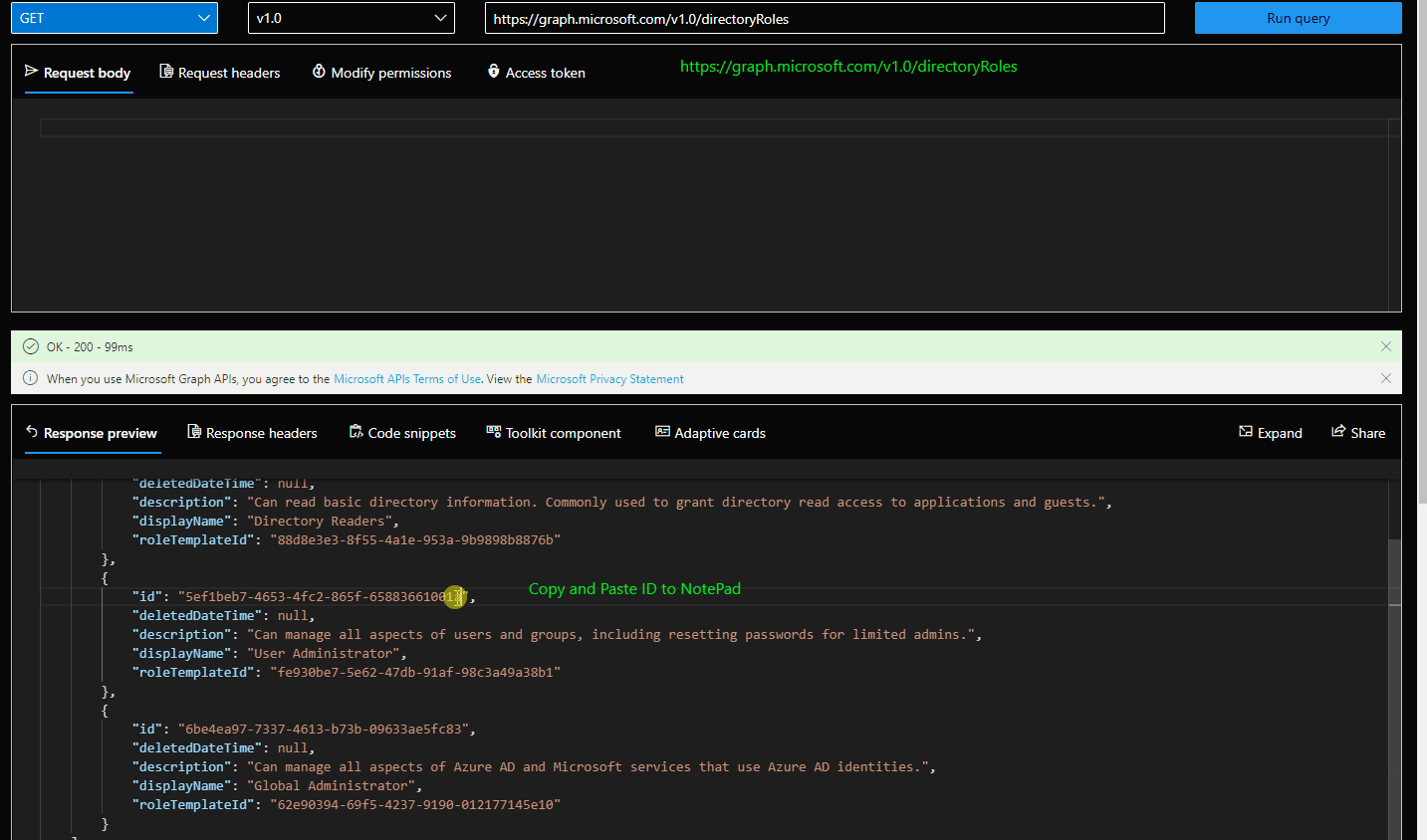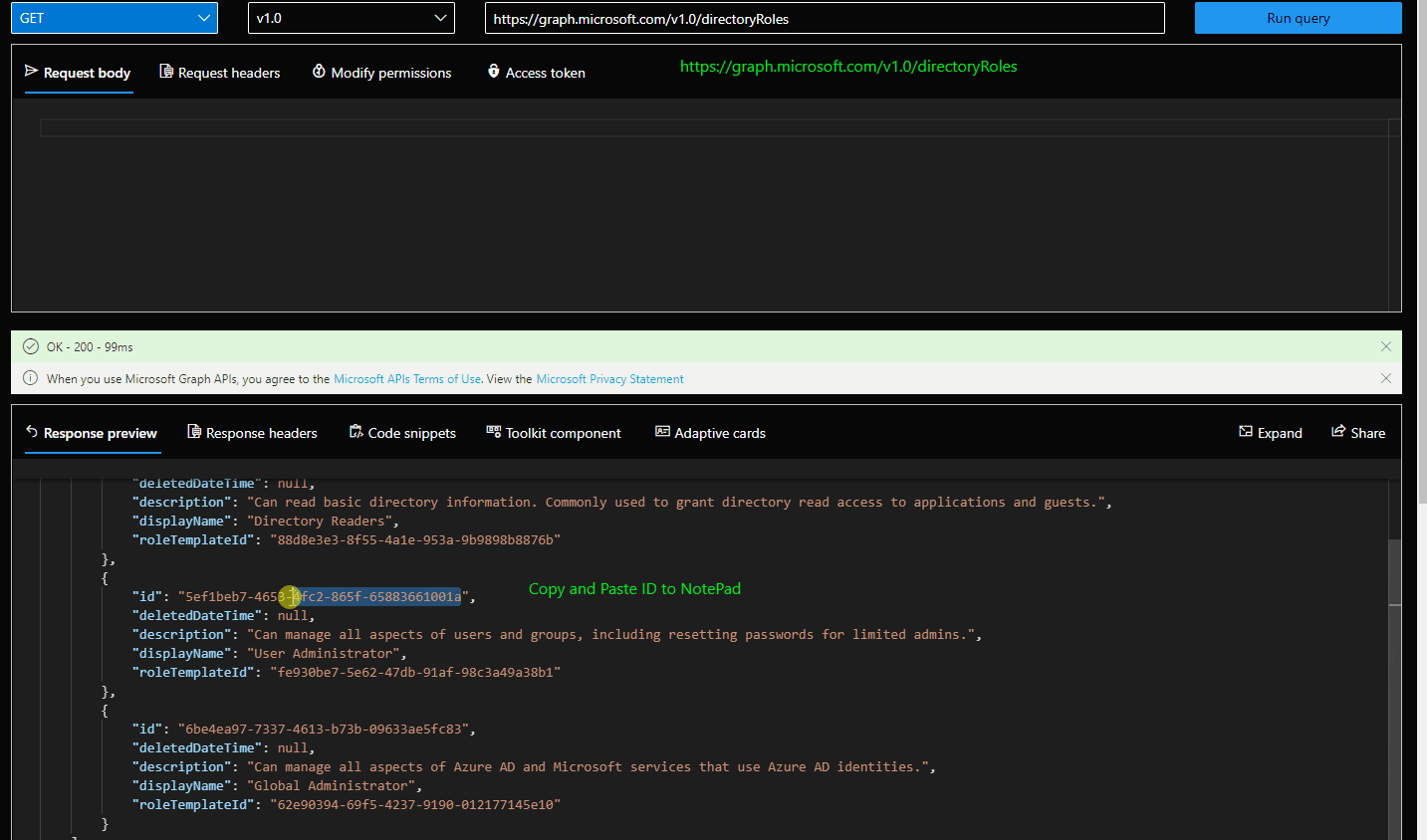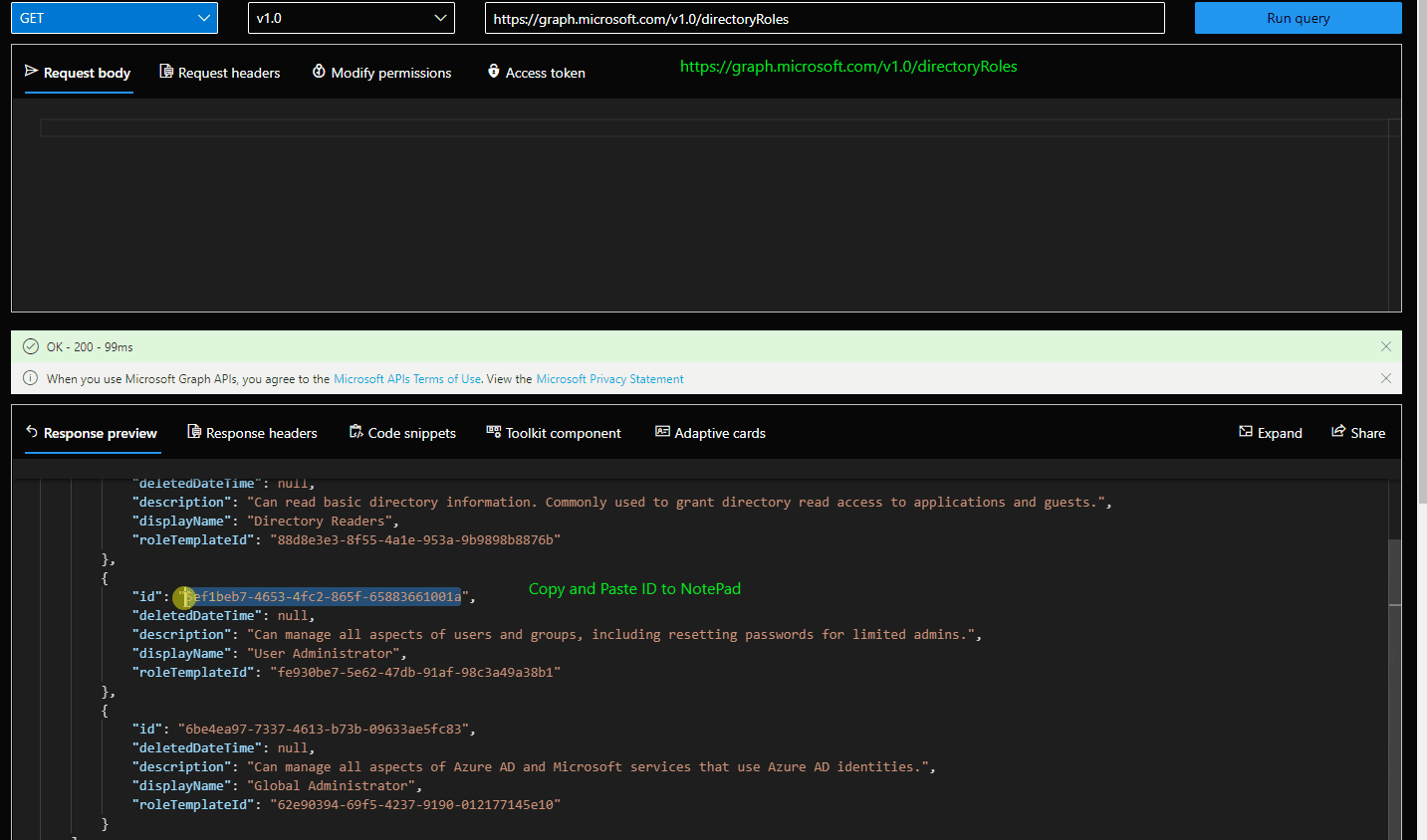
- Find the role template id of the desired role. You can use GET /DirectoryRoles for listing them. If you don't see User Admin role proceed to step 3.
- Activate the desired role using POST /directoryRoles and the RoleTemplateID.
- Add the service principal as a "member" to the directory role using POST /directoryRoles/{ID}/members/$ref in which the body is {
"@odata.id": "https://graph.microsoft.com/beta/servicePrincipals/<servicePrincipalId>"
}
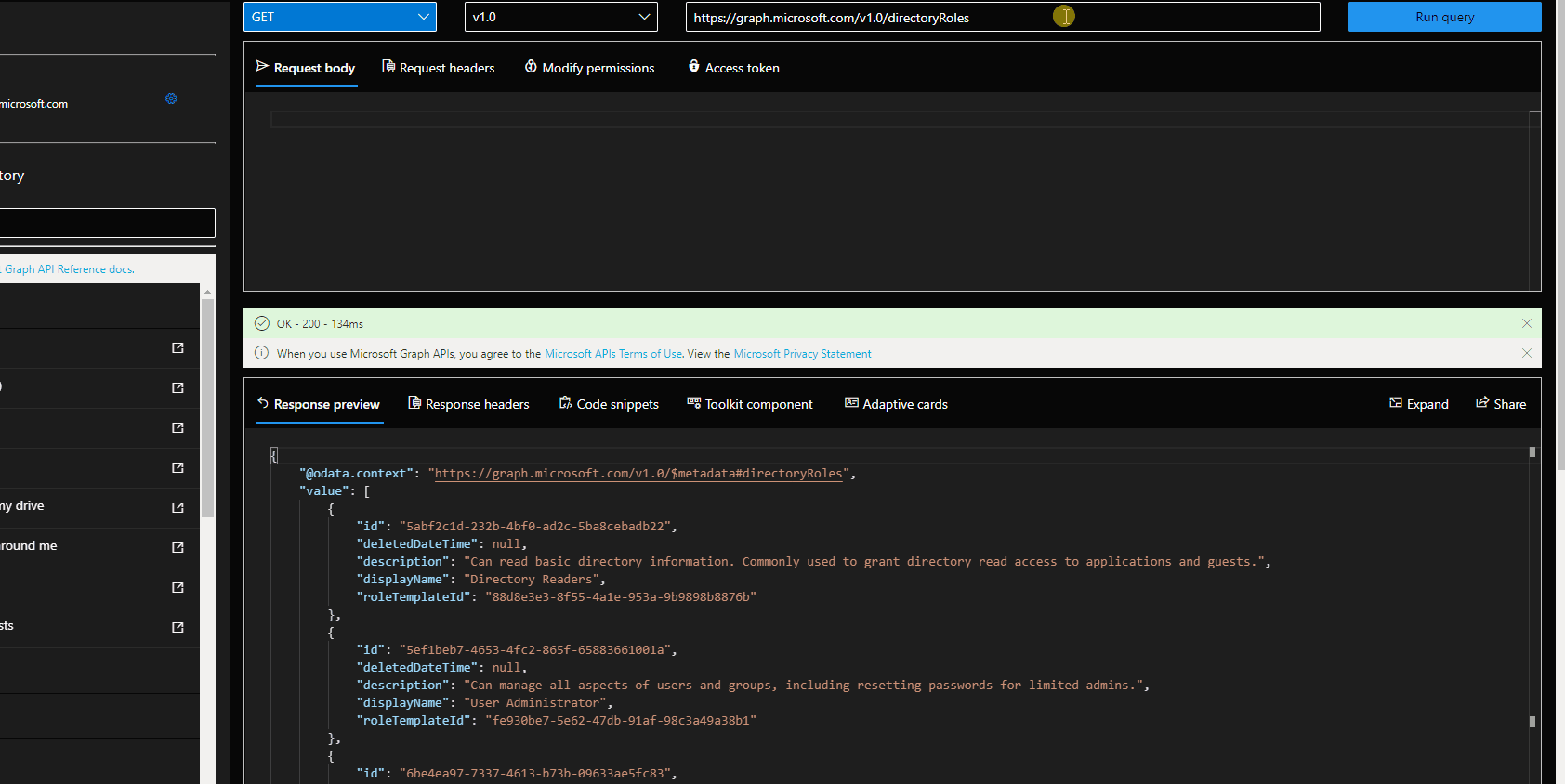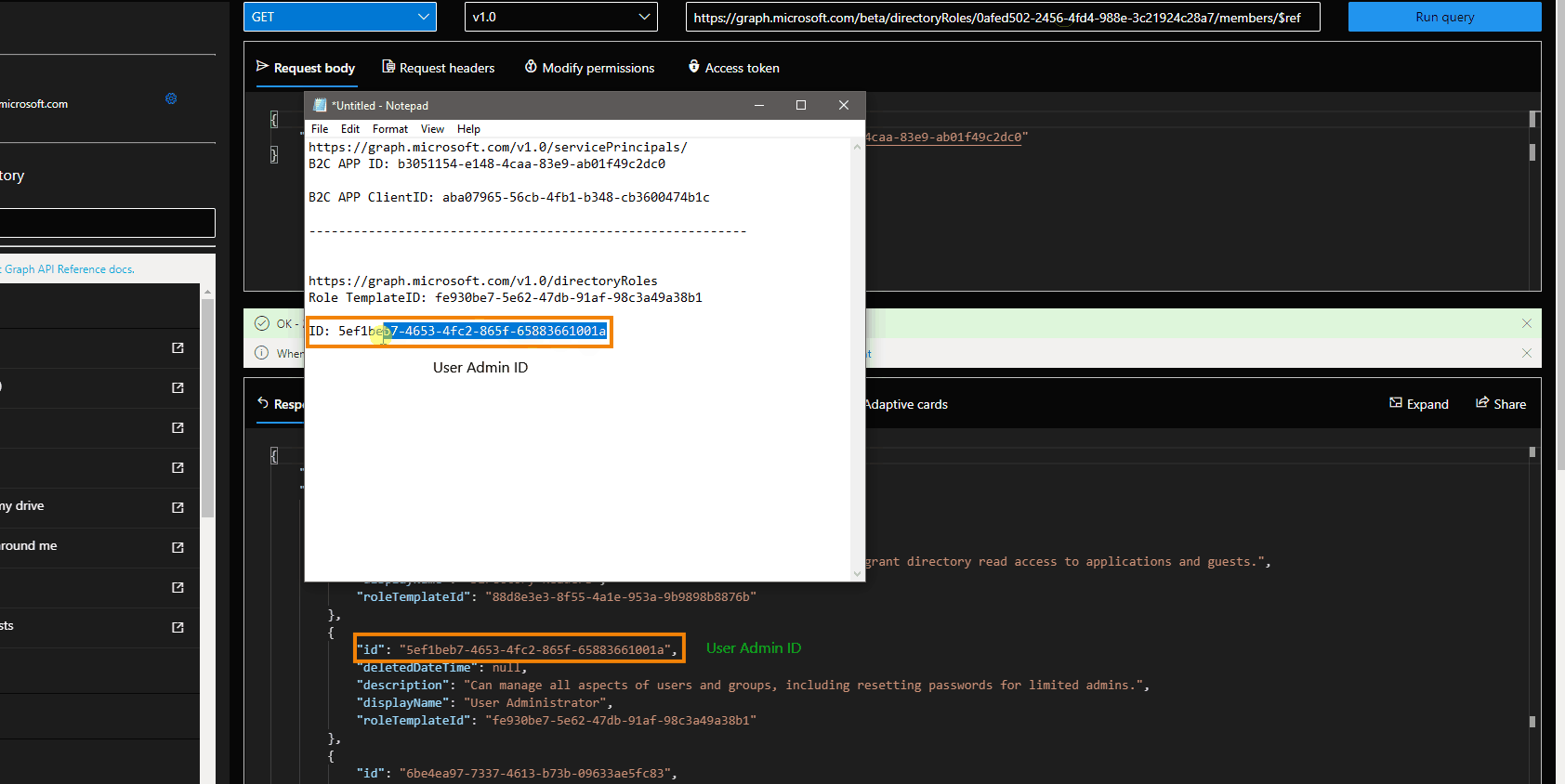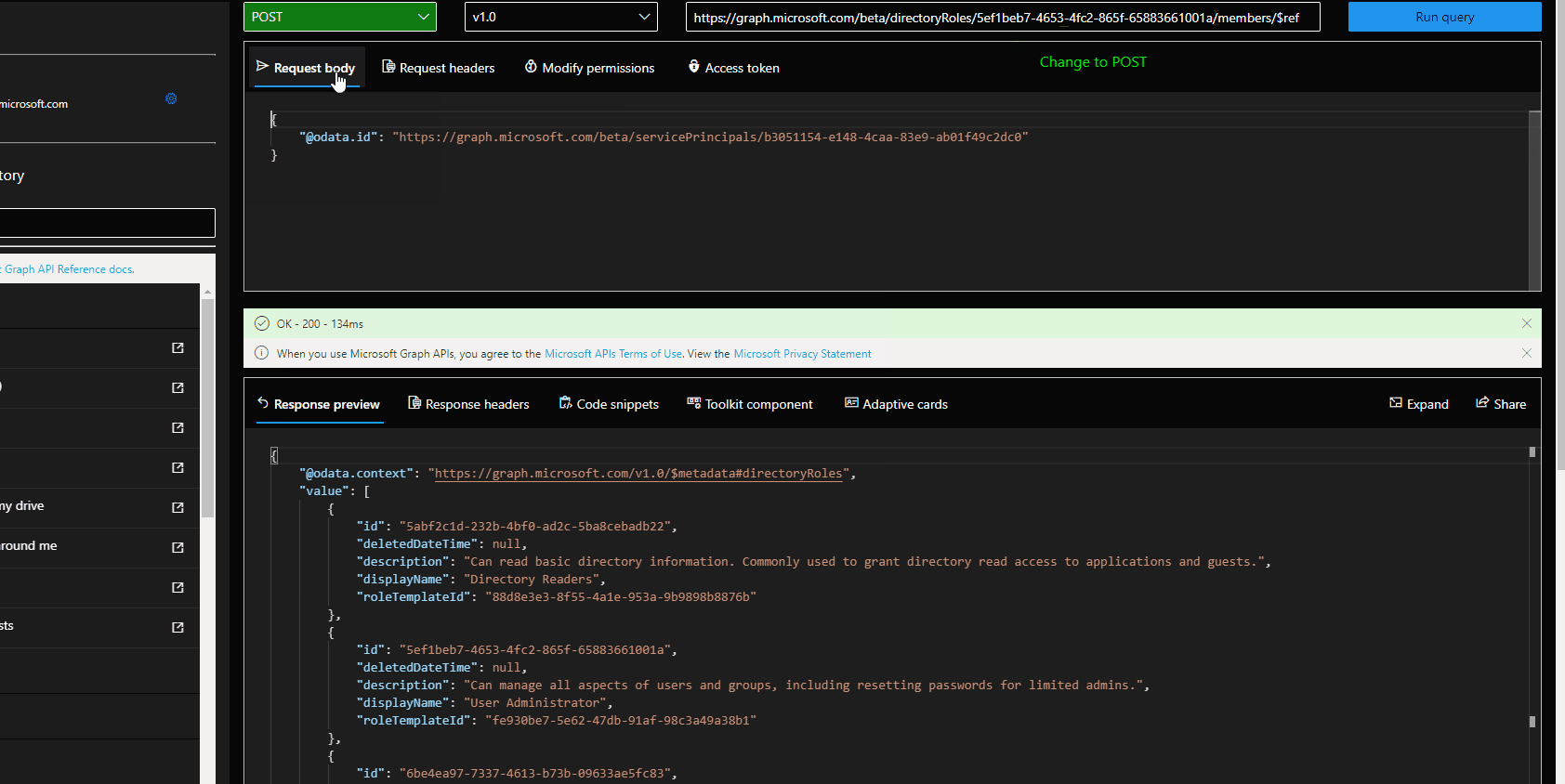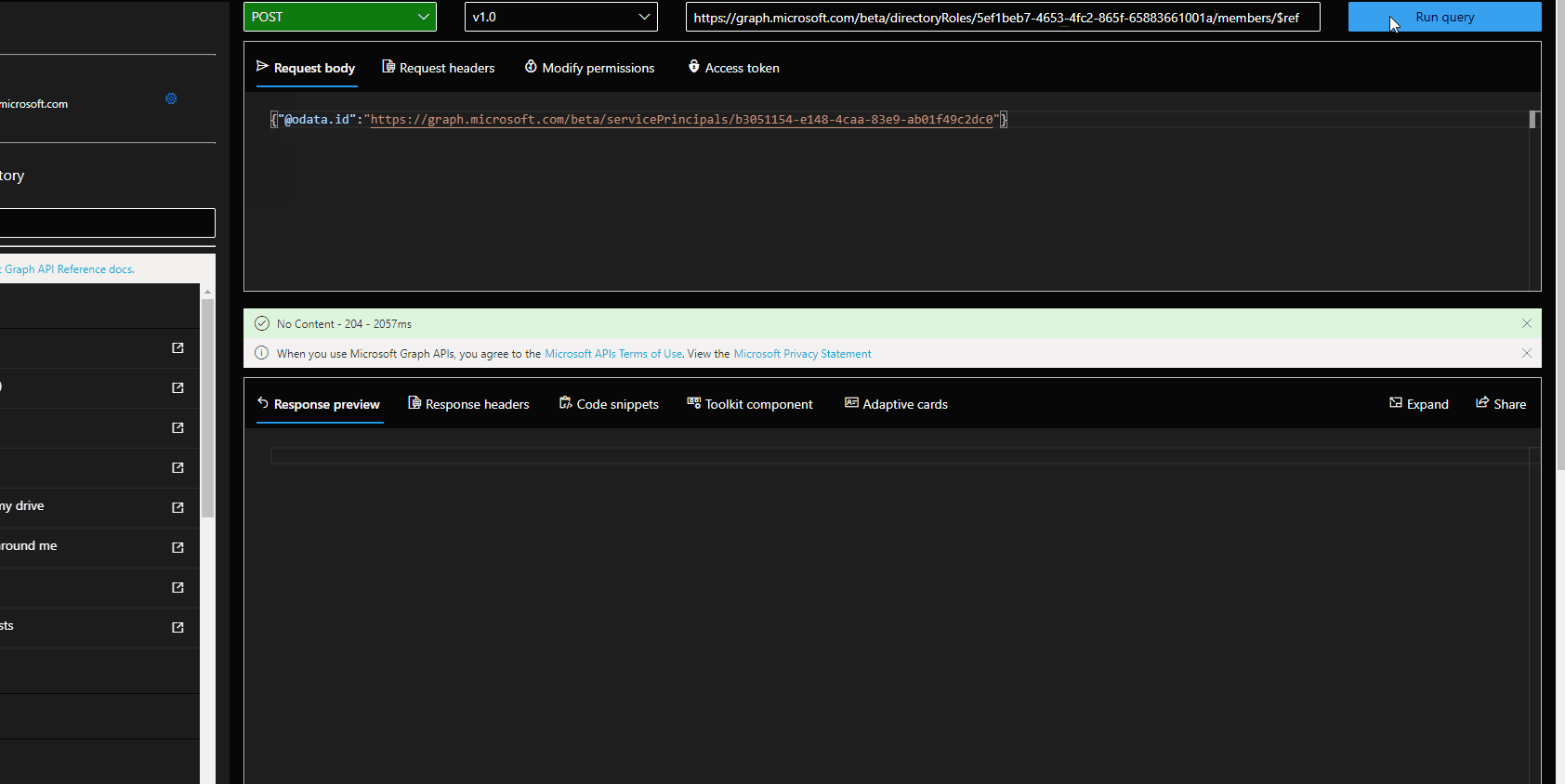
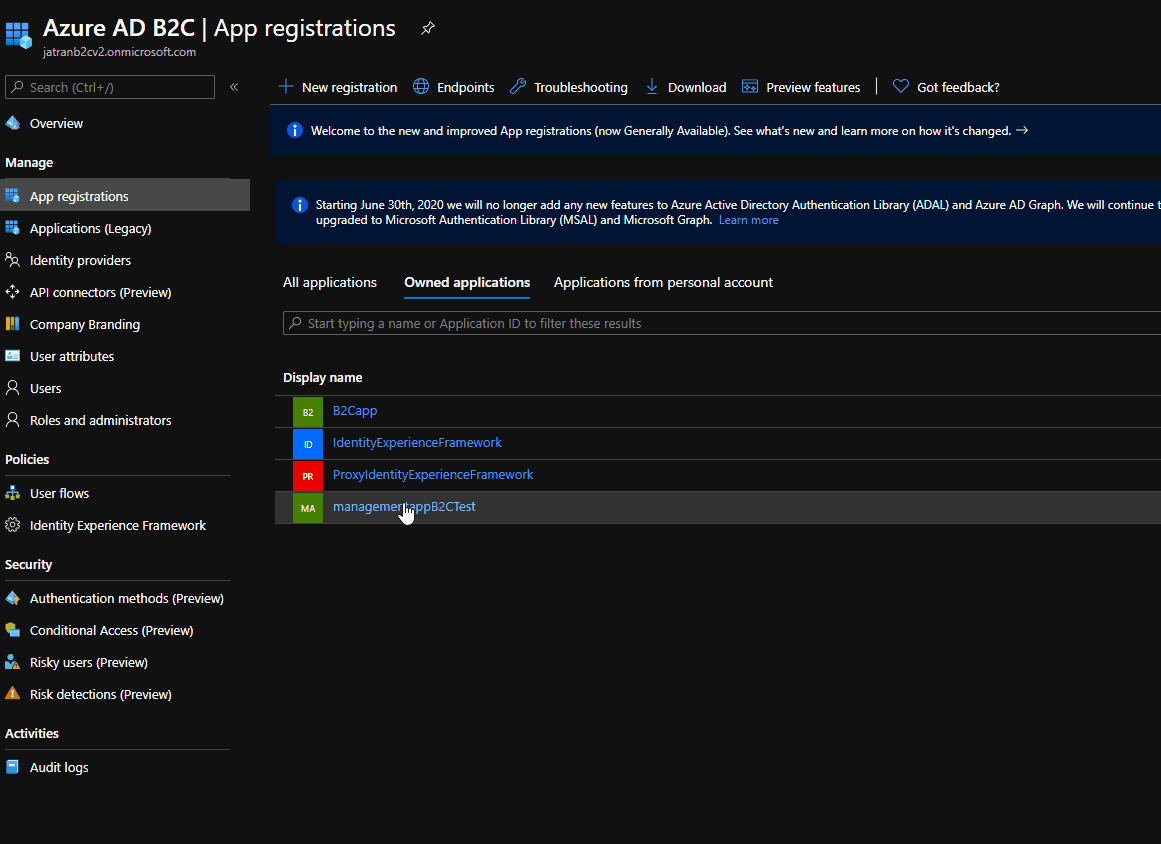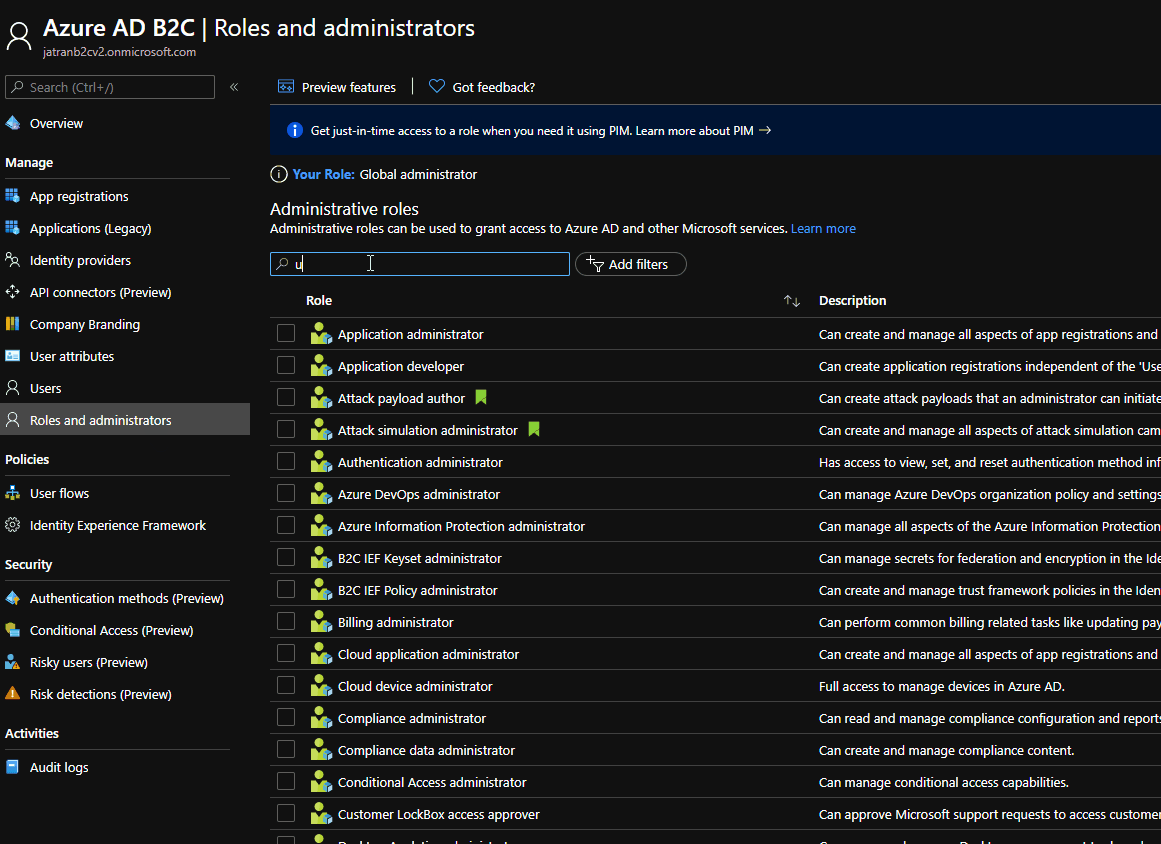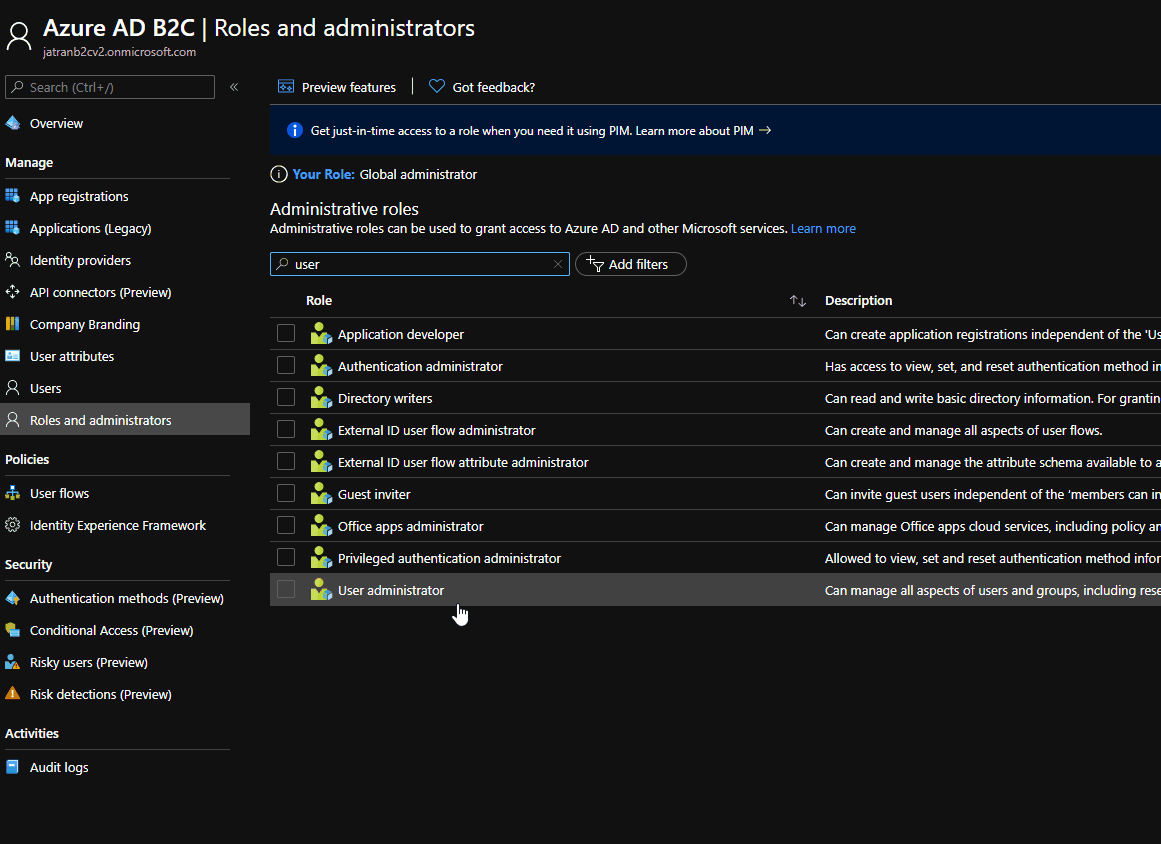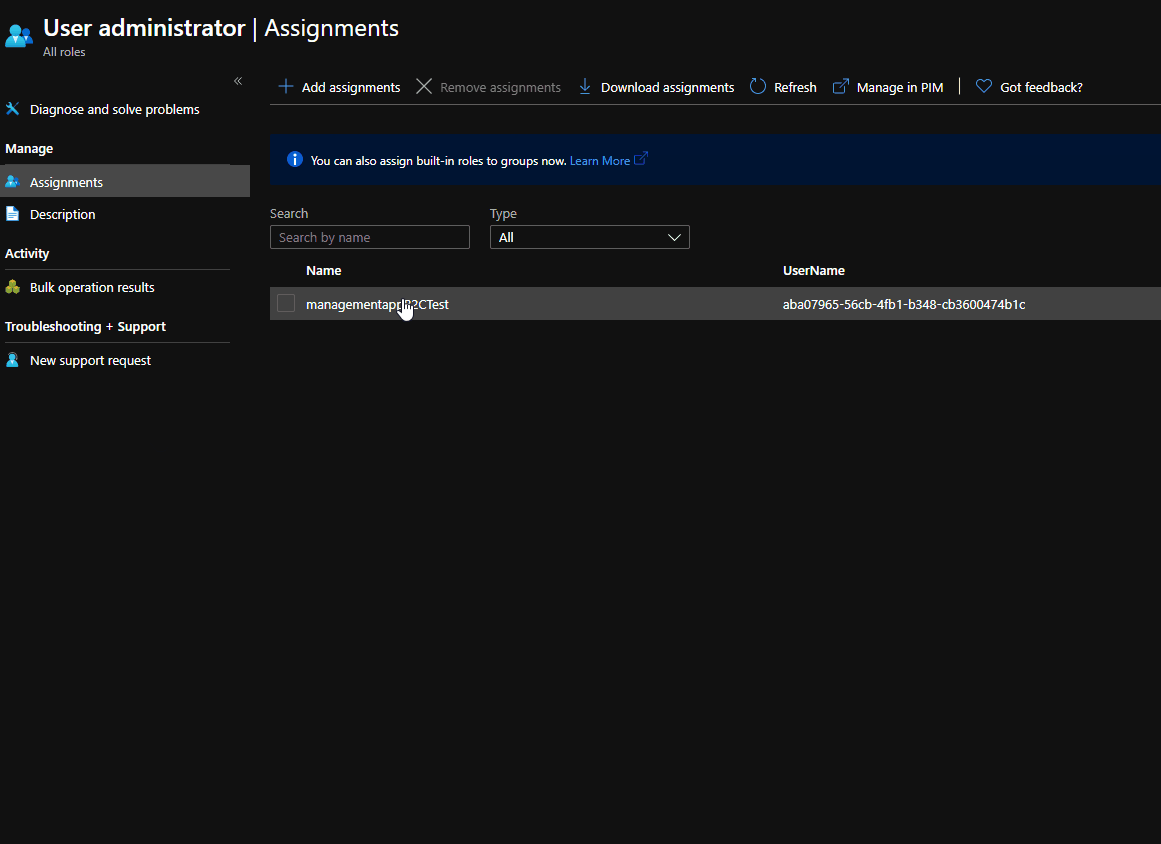
- Check if your role was assigned correctly to your B2C app.
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.