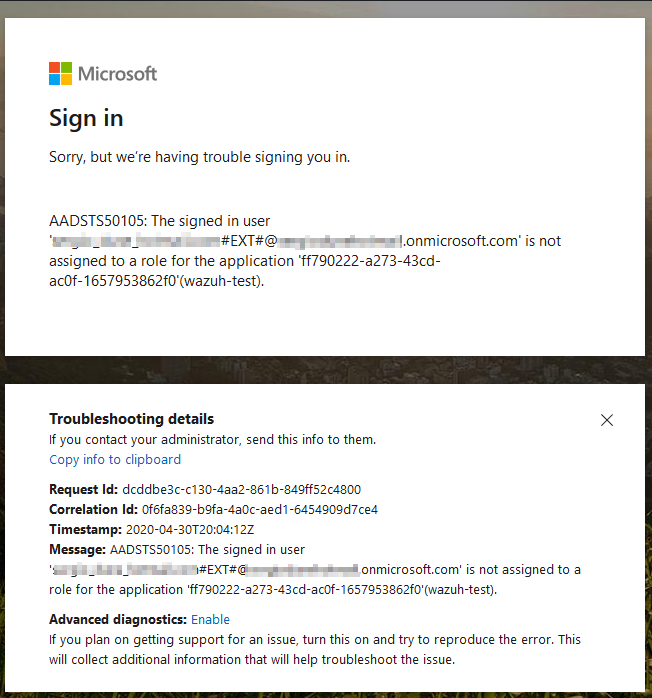
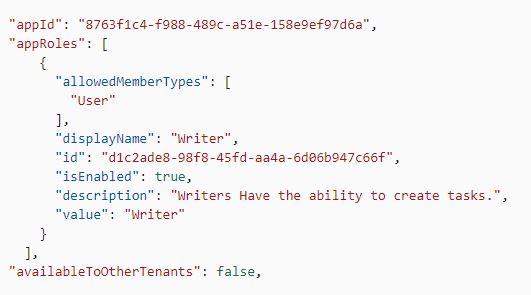
@Sergio Peral You need to define the App Roles in Application Manifest. If no role is defined in the app manifest, you get only user role, which is greyed-out. You can add below parameters to the app manifest to add "Writer" role for example. You can specify any role name using below parameters, as per the application requirement.
Once this is done, you can assign the new roles to users while adding them under "Users and groups" in the application or by editing already added users.
For more details please refer to How to: Add app roles in your application and receive them in the token
-----------------------------------------------------------------------------------------------------------
Please do not forget to "Accept the answer" wherever the information provided helps you to help others in the community.