Hello @mjunglw , Thanks for reaching out.
I worked upon yours ask and a couple of ways is what I could find suitable in your case. You can check the approved attribute values that can be pulled in for claims here: https://learn.microsoft.com/en-us/azure/active-directory/develop/active-directory-claims-mapping#table-3-valid-id-values-per-source
However, you could use directory schema extension feature to extend custom attribute for user and sending them in token claims (SAML SSO).
May I know for which type of user, you would like to extend users attribute ? Cloud-only (created in cloud itself) or Hybrid accounts (created in on-premises and synced to AAD) because, directory schema extension can be configured and administrated through Azure AD connect interface and Azure Portal UI (User Interface) in case of Hybrid accounts which is straight forward whereas for Cloud-Only accounts all configuration and administration are done through PowerShell which require additional steps as explained below:
For Hybrid Accounts:
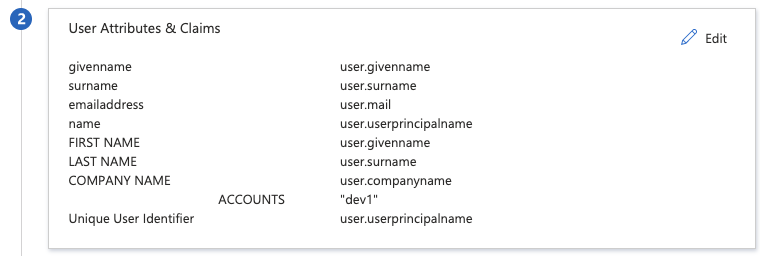
You can use directory extensions to extend the schema in Azure Active Directory (Azure AD) with your own attributes from on-premises Active Directory (in our case “ACCOUNTS”). For more information, refer this article
They can be used as a source for claims both by configuring them as claims in the Enterprise Applications configuration in the Portal UI for SAML applications registered using the Gallery or the non-Gallery application configuration experience under Enterprise Applications, Once a directory extension attribute created via AD Connect is in the directory, it will show in the SAML SSO claims configuration UI as shown below:
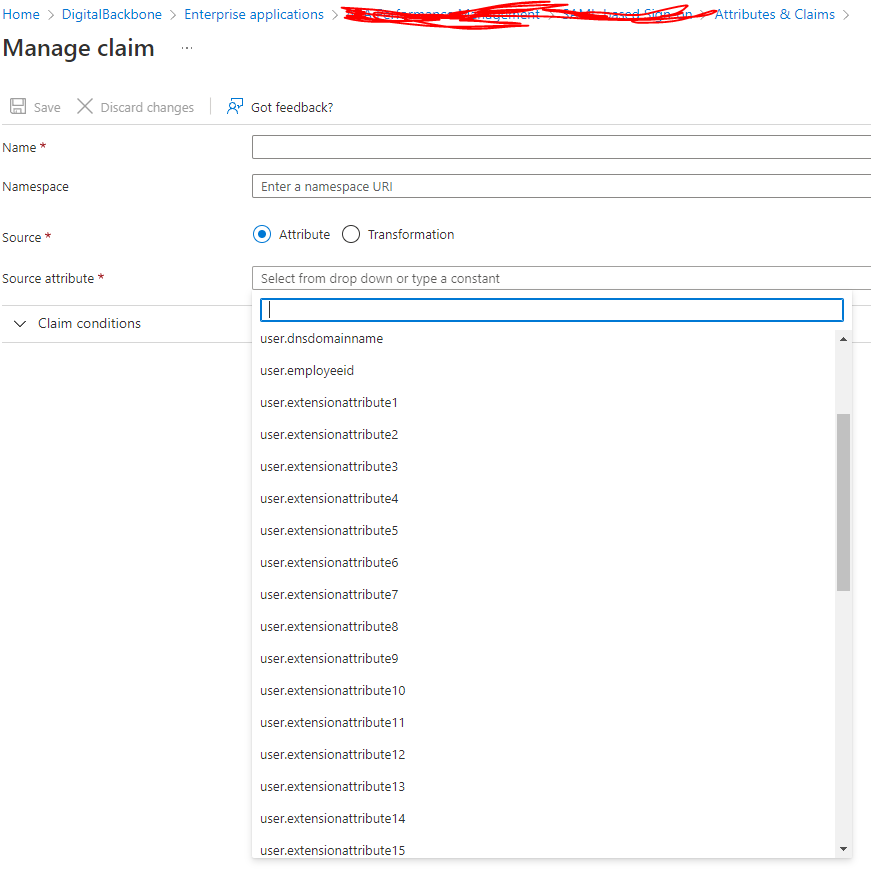
For Cloud-Only accounts:
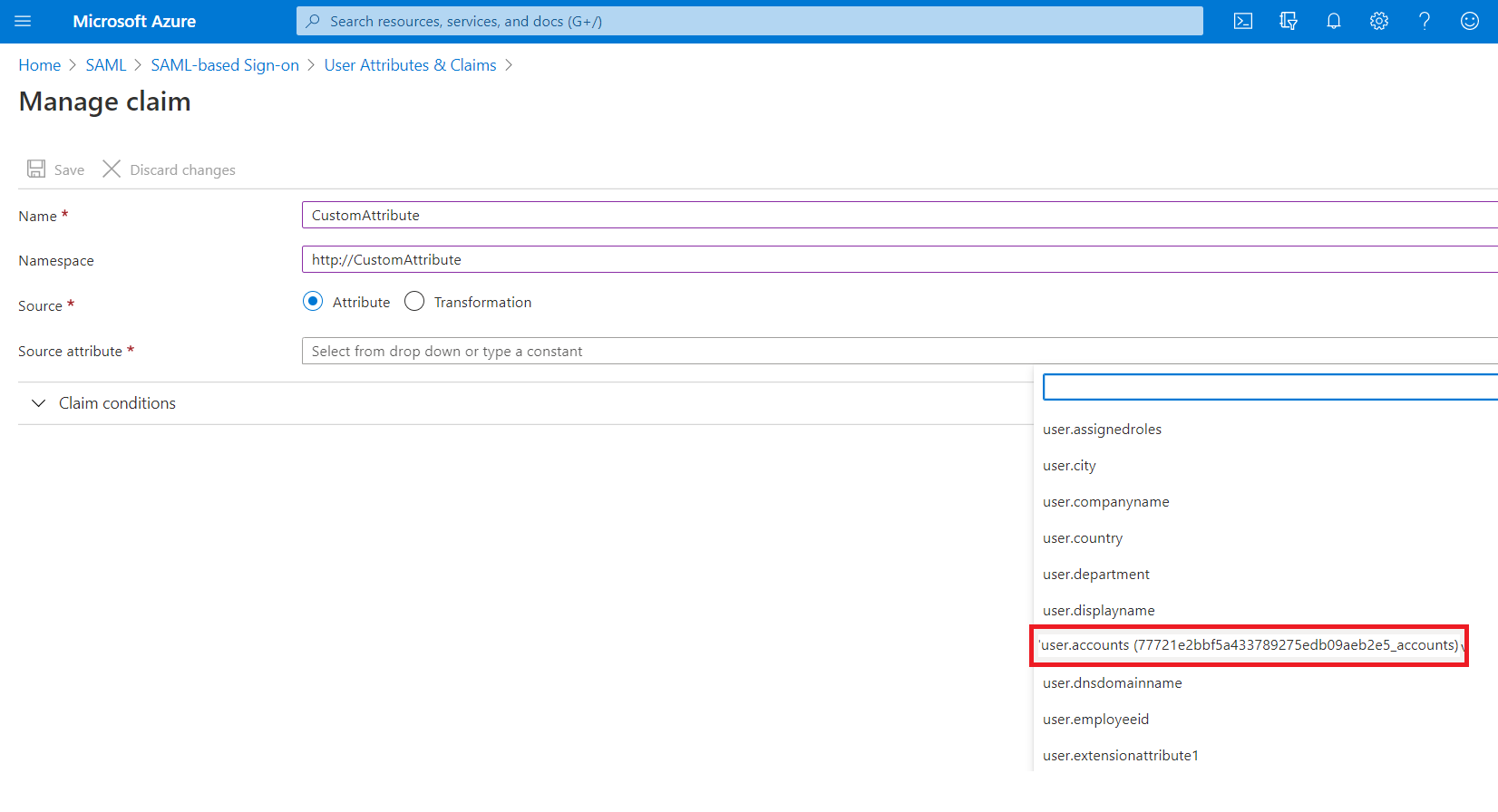
In this case, you can only use PowerShell way for creating a new directory extension, associating them to existing user and set value as explained in this article. This would create custom attribute for Cloud-Only users in AAD and allow you to associate your own custom attribute (in our case “ACCOUNTS”), but these attribute will not show in the SAML SSO claims configuration UI instead you have to use Option Claims configuration UI in the App Registrations configuration in the AAD Portal UI as shown below.
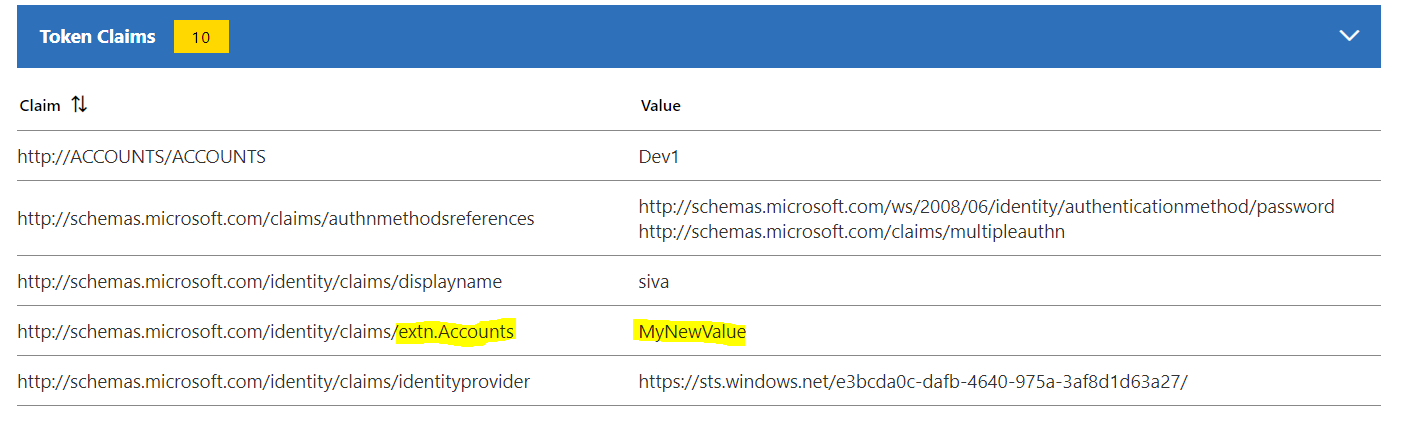
Another difference that you see within the SAML token, these claims will be emitted with the following URI format: http://schemas.microsoft.com/identity/claims/**extn.<attributename>** instead “user.account” (see below screenshot for your reference)
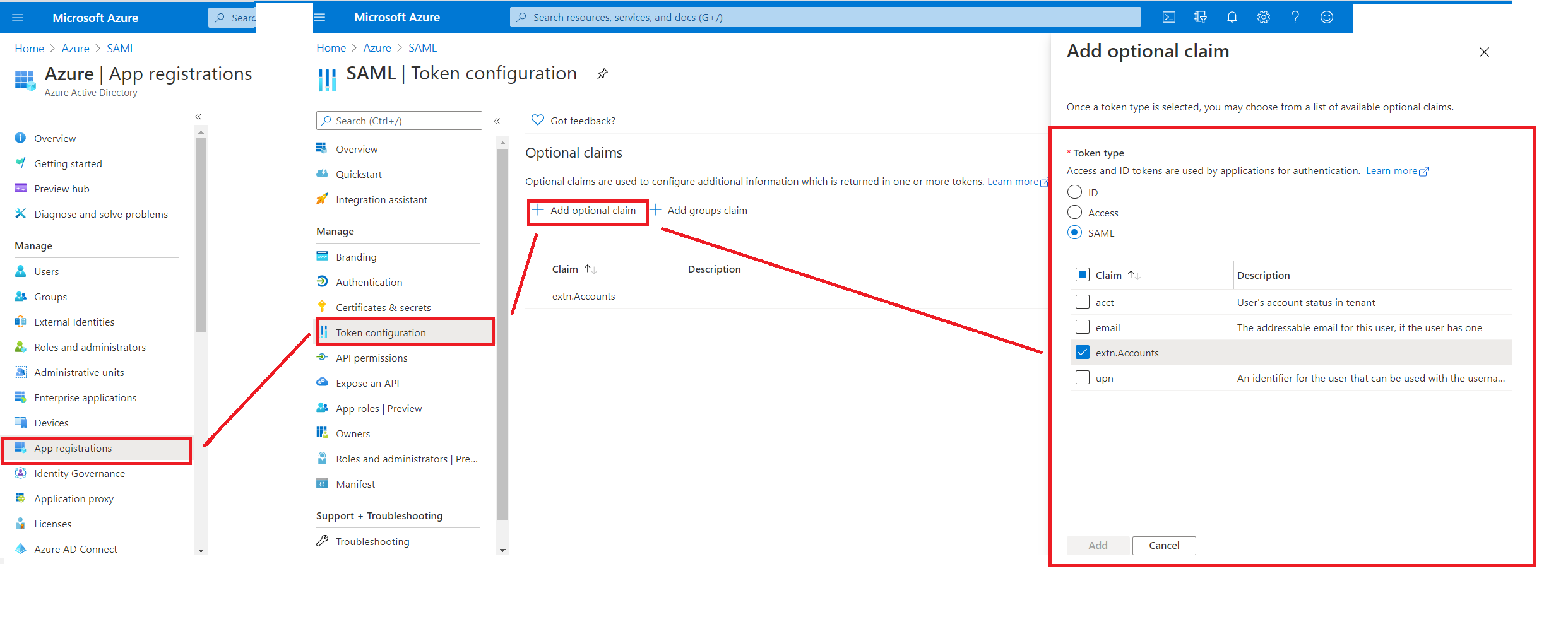
SAML token sample claims for extended attribute:
------------------------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.