That worked nicely many thanks!
Custom static claim in JWT token
Hi,
We have a web application configured with JWT SSO against Azure.
We need to deploy multiple instances of this application, and we would like to configure an optionalc laim to be added to the id token. The claim will be statically defined and will be unique for each application instance.
Is there a way to achieve this? All the examples I found expects value to come from an Azure object, as defined by the 'source' attribute.
What I'm looking for is something like:
"optionalClaims": {
"idToken": [
{
"name": "custom_instance_identifier",
"essential": false,
"value":"instanceid"
}
]
}
Thanks,
Microsoft Security Microsoft Entra Microsoft Entra ID
1 additional answer
Sort by: Most helpful
-
 Siva-kumar-selvaraj 15,721 Reputation points
Siva-kumar-selvaraj 15,721 Reputation points2021-02-10T10:37:09.407+00:00 Hello Hello @Giacomo Collini ,
Thanks for your reaching out.
Custom static claim can be configured by using "Claims mapping policies". Please find below detailed steps for creating AzureAD policy and then assigning them to service principal objects.
• You must have AzureAD module installed because this can be only done through PowerShell way. If not installed already refer this article to install AzureAD Module.
• Use this cmdlet to create New Azure AD Policy, this would define static claim with the name of custom_instance_identifier and value as 555
New-AzureADPolicy -Definition @('{"ClaimsMappingPolicy":{"Version":1,"IncludeBasicClaimSet":true,"ClaimsSchema":[{"Value":"555","JwtClaimType":"custom_instance_identifier"}]}}') -DisplayName "StaticClaim" -Type "ClaimsMappingPolicy"• To see your new policy, and to get the policy ObjectId, run the following command:
Get-AzureADPolicy• Assign the policy to your service principal. You can get the ObjectId of your service principal from Enterprise applications blade as shown below screenshot.
Add-AzureADServicePrincipalPolicy -Id <ObjectId of the ServicePrincipal> -RefObjectId <ObjectId of the Policy>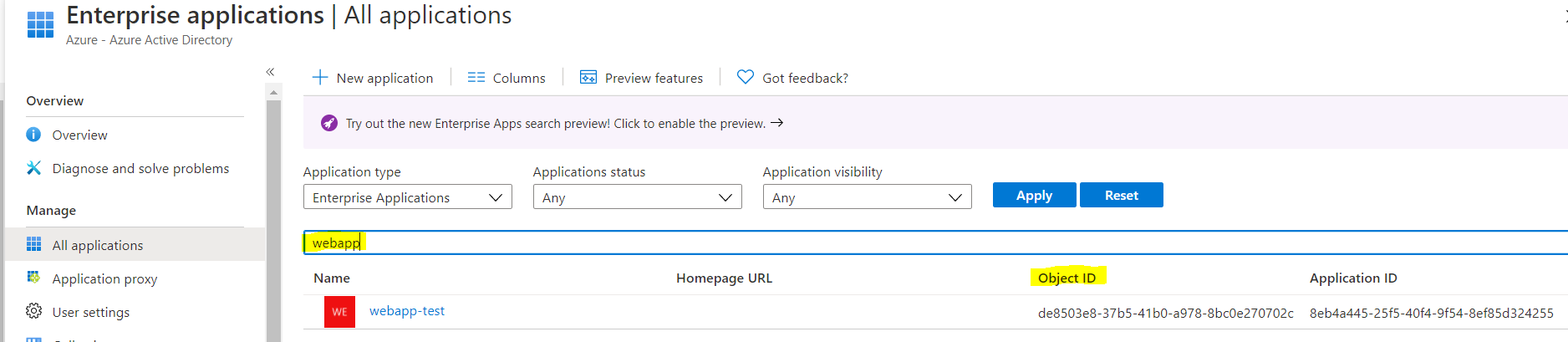
• Once policy has successfully assigned, then enable the AcceptMappedClaims to true in the App Registration Manifest as we can see in the following image:
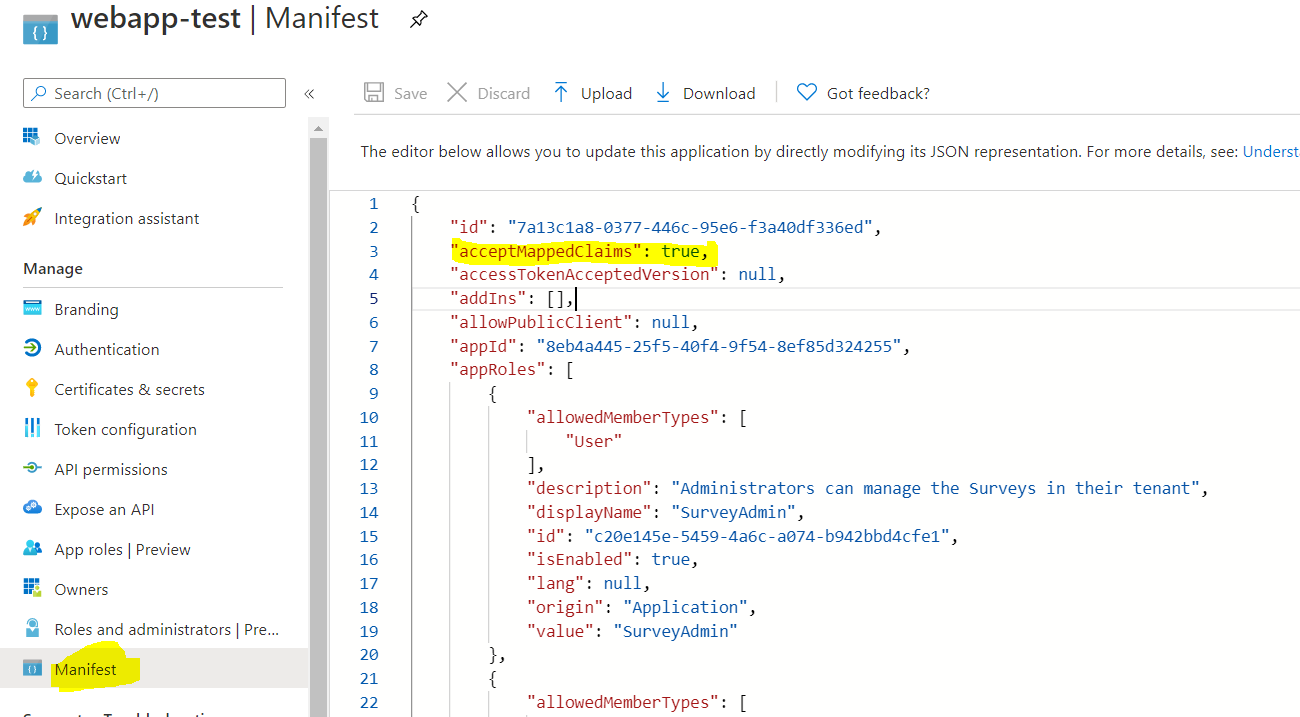
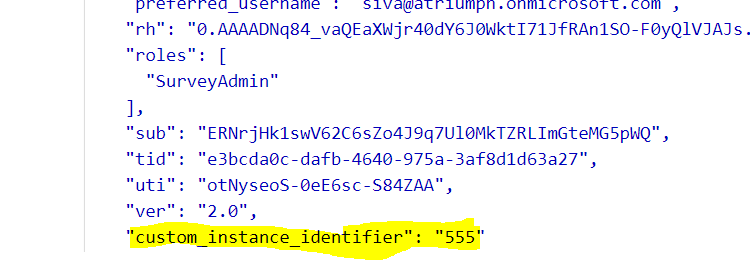
Now you should see defined static claim appears in ID_Token (JWT token). Please find below screenshot from my lab for your reference:
id_token (JWT):
------------------------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.