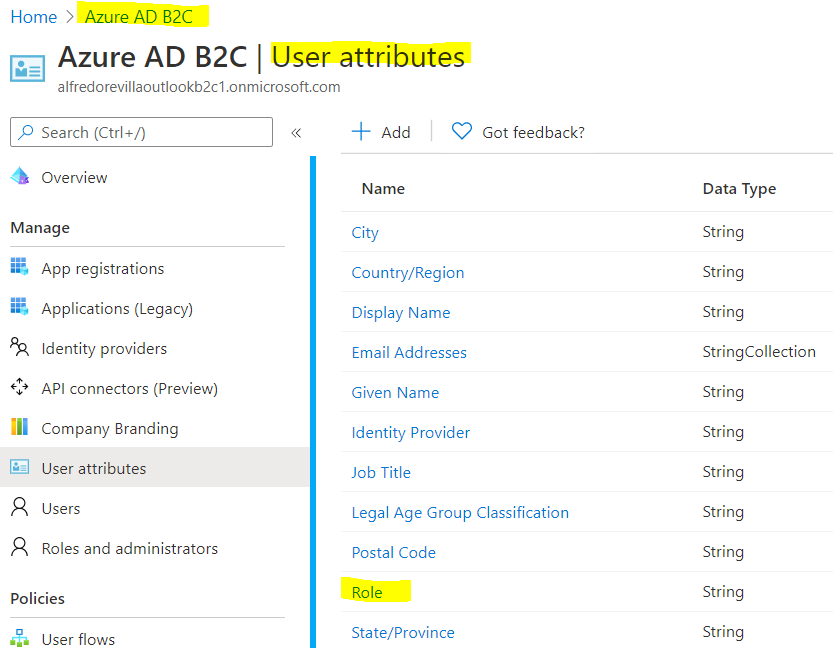
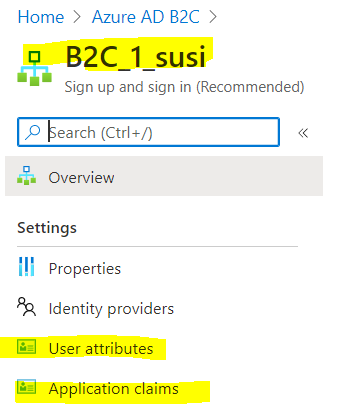
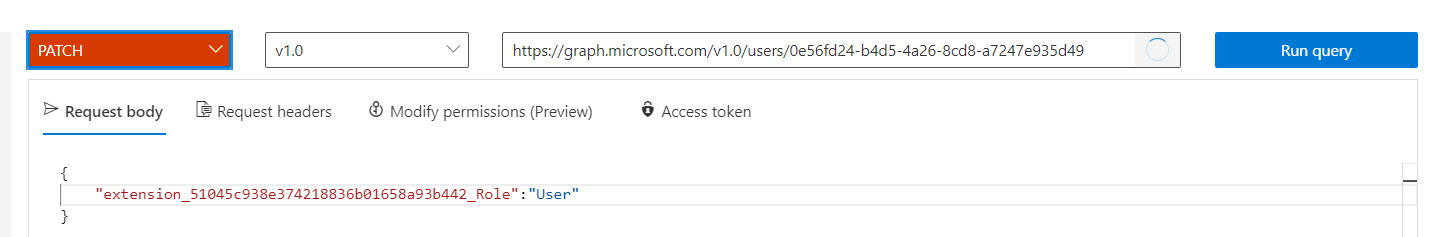
Howdy, using B2C app registrations you cannot retrieve MS Graph scopes besides open_id and offline_access, In cases where you need access to more MS Graph endpoints you need to use a regular Azure AD app registration preferabily using a client credential flow to acquire the token. To issue a custom role or roles claim you can use custom attributes (for both user flow and custom policies) or custom claims (custom policies only). Once your B2C token includes a roles claim you can re-use the same code found in other samples. Basically:
services.Configure<OpenIdConnectOptions>(OpenIdConnectDefaults.AuthenticationScheme, options =>
{
// The claim in the Jwt token where App roles are available.
options.TokenValidationParameters.RoleClaimType = "roles"; //or role (claim types) or extension_roles or extension_role (directory extensions)
});
// Adding authorization policies that enforce authorization using Azure AD roles.
services.AddAuthorization(options =>
{
options.AddPolicy(AuthorizationPolicies.AssignmentToUserReaderRoleRequired, policy => policy.RequireRole("UserReaders"));
options.AddPolicy(AuthorizationPolicies.AssignmentToDirectoryViewerRoleRequired, policy => policy.RequireRole("DirectoryViewers"));
});
[Authorize(Policy = AuthorizationPolicies.AssignmentToDirectoryViewerRoleRequired)]
Or
[Authorize(Policy = AuthorizationPolicies.AssignmentToUserReaderRoleRequired)]
@soumi-MSFT
* If the answer was helpful to you, please accept it and, optionally, provide feedback so that other members in the community can benefit from it.*