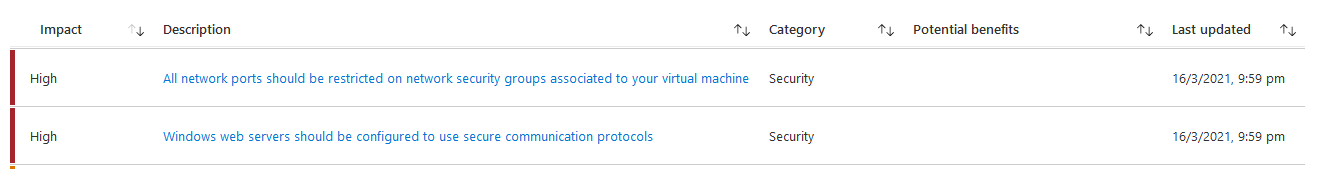
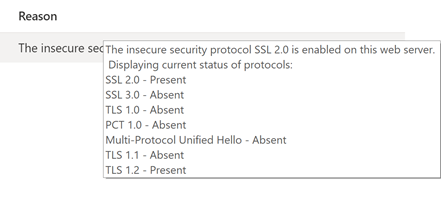
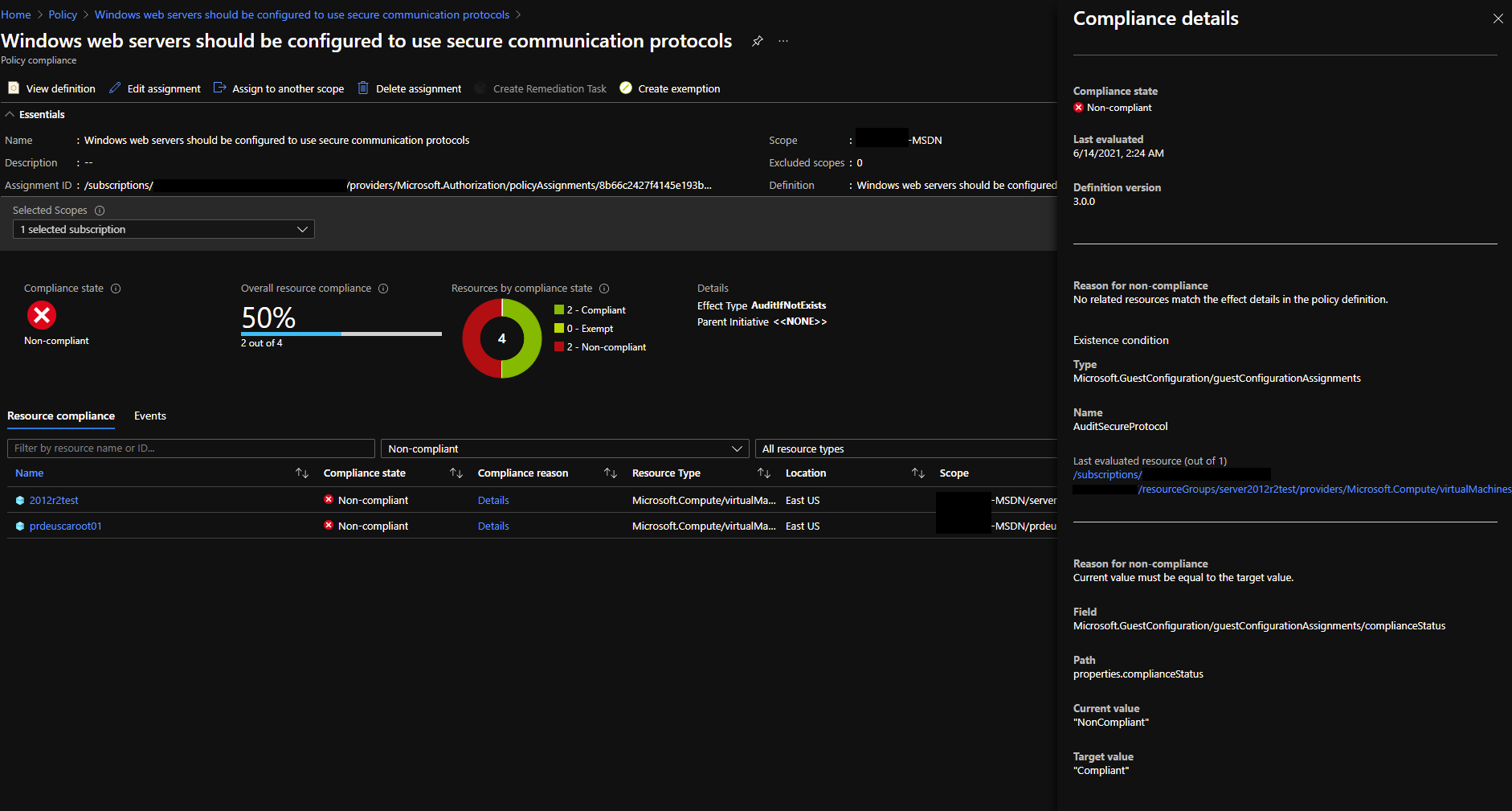
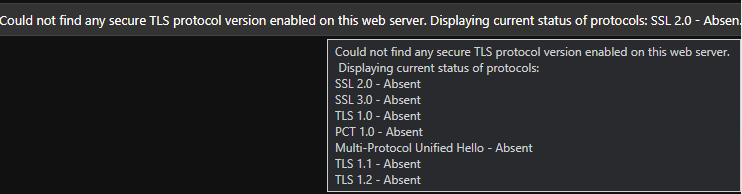
Have a look at the exact compliance reason in the recommendation.
In my case, on my end it said GCExtensionInstalled=False;MSIEnabled=False;UserIdentityEnabled=False
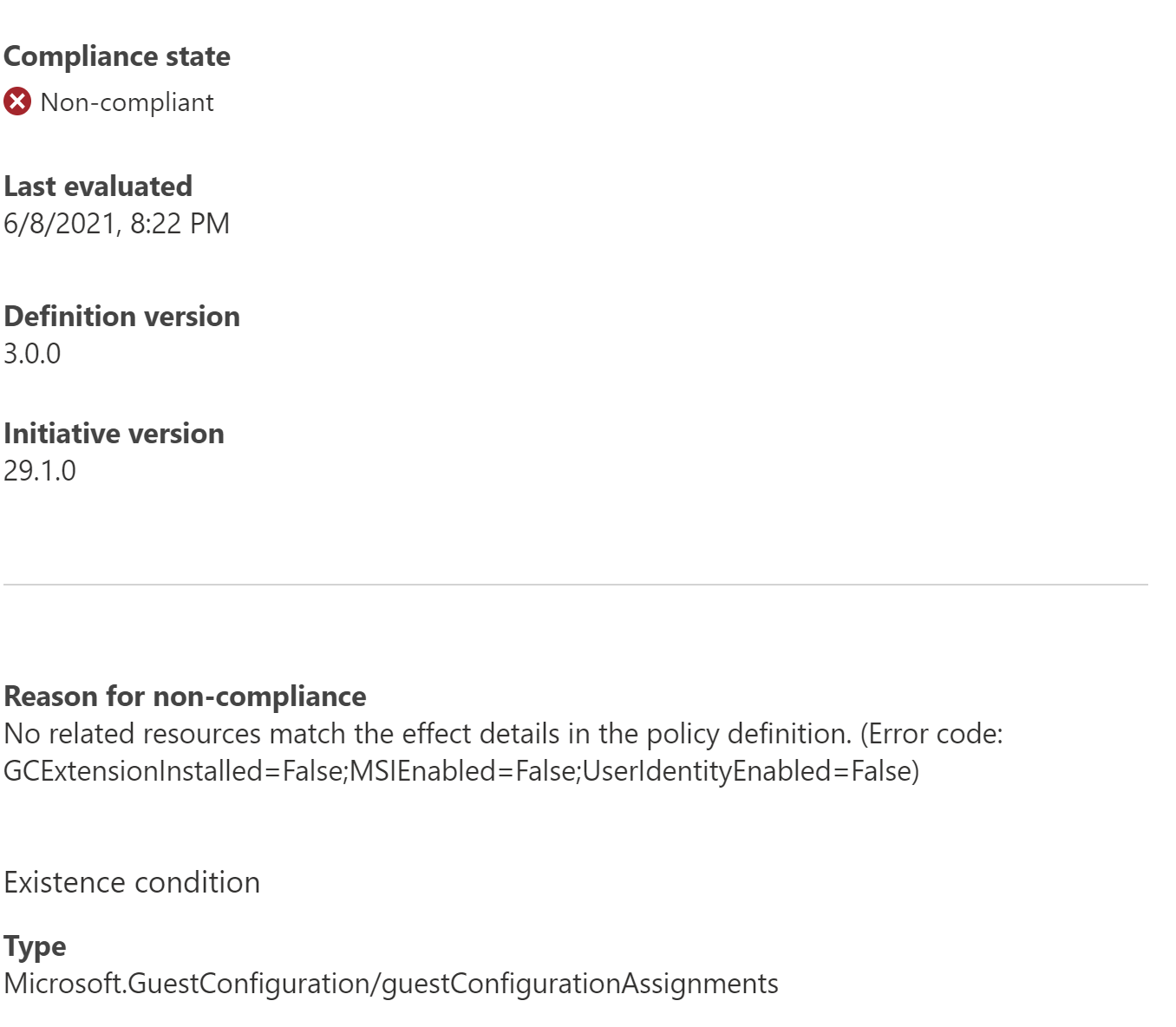
This is what I did to fix it:
A. GCextensionInstalled:
Install the Guest Configuration extension on your VM - I did this via Azure CLI:
az account set --subscription "MY SUBSCRIPTION NAME"
select-azsubscription - subscriptionname "MY SUBSCRIPTION NAME"
az vm extension set --publisher Microsoft.GuestConfiguration --name ConfigurationforWindows --extension-instance-name AzurePolicyforWindows --resource-group MYRESOURCEGROUP --vm-name MYVM
B. MSIEnabled:
Don't go looking for installation (msi) options. This means your VM doesn't have a Managed System Identity
To fix this, follow this article: https://learn.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/qs-configure-portal-windows-vm
Or in short, open the Azure PORTAL, go to your VM - Settings - Identity and enable the System Assigned Identity.
C. UserIdentityEnabled:
- First, Go to "Managed Identities" in the portal
- Create a new Managed Identity (select subscription, resource group), put it in the right region and give it a RECOGNIZABLE name (eg MY-USER-IDENTITY-VM)
- Next, go to your VM again
- Next, go to Settings - Identity
- Now, select User Assigned Identities
- Click Add
- Select the User Assigned Identity that you just created (eg MY-USER-IDENTITY-VM)
D. Now, rerun the compliancescan
In my case, my test case VM was in an isolated resource group, so I ran this command:
start-azpolicycompliancescan -resourcegroupname 'my-isolated-resource-group'
An hour later, my VM was marked compliant.