I tested the process in my lab and it works for me.
Policy Created using the PS Cmdlet:
Set-AzureADPolicy -Definition @('{"TokenLifetimePolicy":{"Version":1,"AccessTokenLifetime":"23:00:00"}}') -Id "b477b9f2-3f7d-4ccf-a702-1af7224a8016" -IsOrganizationDefault $false -Type "TokenLifetimePolicy"
PS C:\windows\system32> $policyID = "b477b9f2-3f7d-4ccf-a702-1af7224a8016"
PS C:\windows\system32> $sp = Get-AzureADServicePrincipal -SearchString "Access"
PS C:\windows\system32> Add-AzureADServicePrincipalPolicy -Id $sp.ObjectId -RefObjectId $policyID
PS C:\windows\system32> Get-AzureADServicePrincipalPolicy -Id $sp.ObjectId
Id DisplayName Type IsOrganizationDefault
-- ----------- ---- ---------------------
b477b9f2-3f7d-4ccf-a702-1af7224a8016 ExtendedAccessTokenLifetimePolicy TokenLifetimePolicy False
After that I tried getting an Access Token from Azure AD using the Authorization Code Grant Flow of OAuth2.0 protocol and got the token with the following lifetime mentioned:

Note: Inorder for this AzureADPolicy to work and provide you desired access token's lifetime, you need to keep in mind that when you make a request for the token by reaching the token endpoint of AzureAD, in the request body, for the resource parameter, you need to specify the "App ID" on whose corresponding Service Principal you have attached this Azure AD Policy.
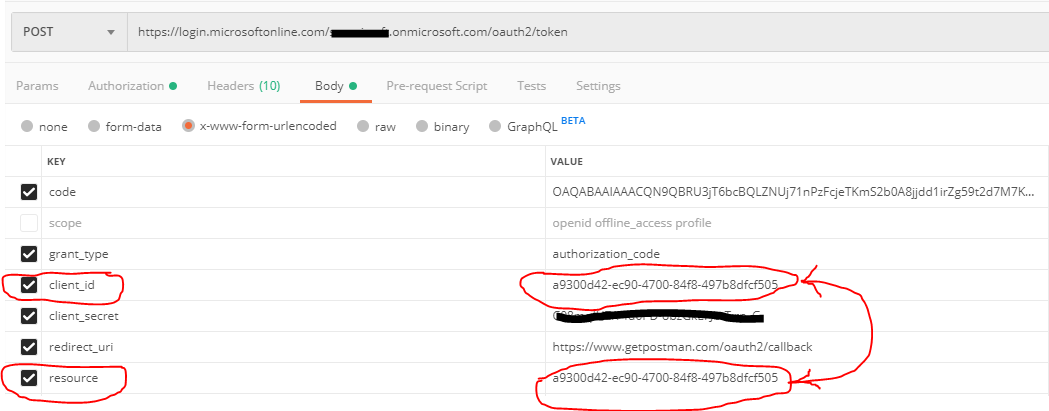
Note: This custom lifetime for Access Tokens, cant be set for first party resources like Graph API etc.
Hope this helps.