Hi everyone
I just wanted let you know that we have found an error in combination with TPM-saved RSA certificates and Client Authentication on TLS1.2 with newer Windows 10 Clients (probably all after 1909).
It seems that a lot of 2.0 TPMs have a problem with RSA PSS.
I wanted to share this problem because we have spent a lot of time to identify the issue. So I hope that other admins will find this post before they spend a lot of time in troubleshooting.
The issue happens during the TLS handshake. The TPM just doesn't signs the certificate verify step as shown on this print screen:
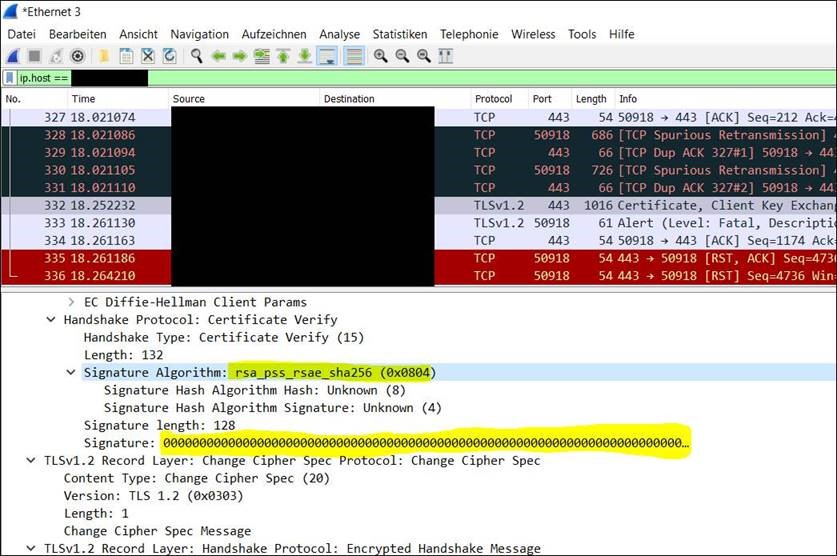
By disabling RSA PSS on the client, the client uses another cipher to sign the packet and then it works.
You can disable RSA PSS by following those steps:
- Backup this key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Cryptography\Configuration\Local\SSL\00010003
- Under Functions remove the following signature suites from the list:
- RSAE-PSS/SHA256
- RSAE-PSS/SHA384
- RSAE-PSS/SHA512
- Reboot
After the reboot, the client uses now RSA PKCS1 and the signature step runs successful:
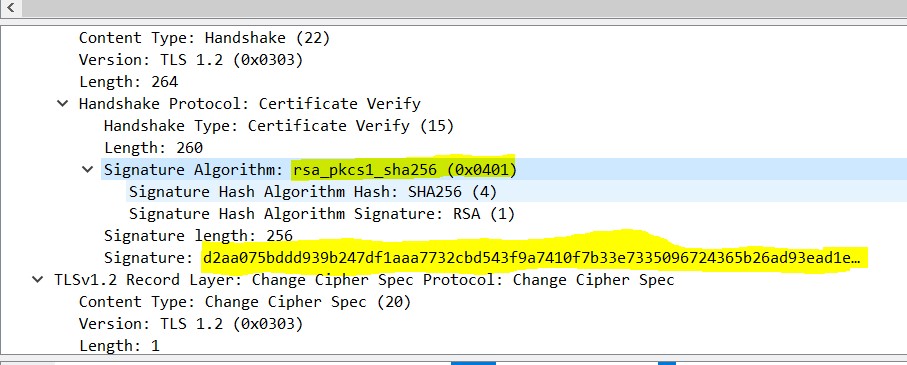
The issue was initially identified on a EAP-TLS authentication for an IPSec tunnel. But the issue happens also on client certificate authentication on https websites as both use TLS for the handshake.
Keep in mind that this is only a workaround and should not be used as a final solution. We are actually still working with Microsoft on a solution.
It's still not 100% clear if it's the TPM that is making the issue or if it is the OS.
I will keep you updated...

