We managed to fix this issue by following the recommendations from our Security team.
No problem, the steps to fix it are as follows:
- Go to “HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers”.
- Create Subkey “HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168”.
- Create DWORD value “Enabled” in the subkey and set its data to 0x0.
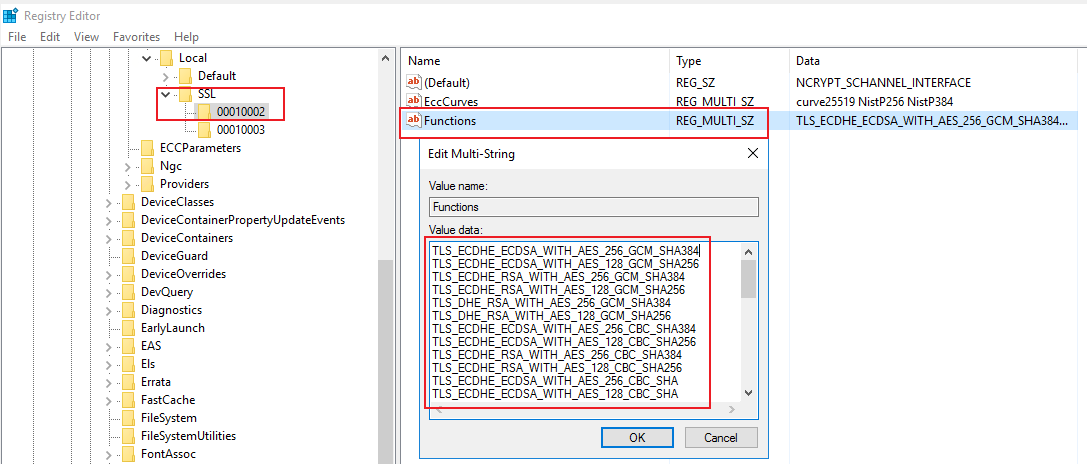
End result should look like the following.
I have tested it our lab environment for Windows 10 Pro (domain-joined workstation) and Windows Server 2019 (DC for child domain) and I can confirm it did not break Schannel-based RDP successive logins to the best of my knowledge.
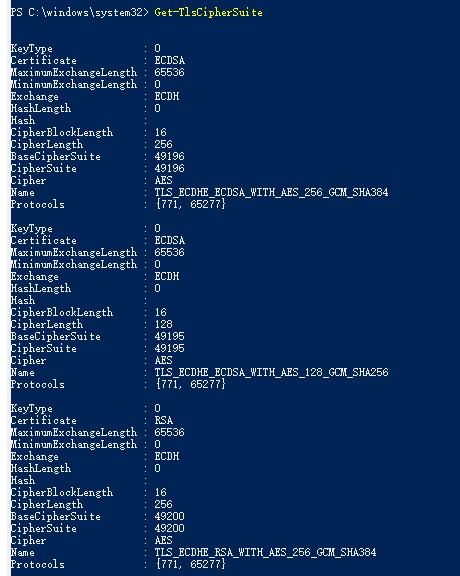
The vulnerability was also mitigated as per the following nmap scans that leveraged “ssl-enum-ciphers” script to test for Sweet32. Left being before the patch and right being after the patch.